Anyone who’s gone to a website has probably noticed that the URL starts with http or https.
You may have also seen a green lock icon with the word ‘secure’ written beside it.
Have you ever wondered what those letters and that lock sign mean?

Below, we will review the most important concepts related to HTTPS.
The S at the end of HTTPS stands for ‘secure.’
If you are using Content Management System (CMS) like WordPress or Joomla, HTTPS is necessary.
Often, people switch to HTTPS because their sites Google ranking is adversely affected without it.
However, they are not aware of the security benefits of HTTPS.
Beyond Google rankings, using HTTPS can also improve user trust in your website.

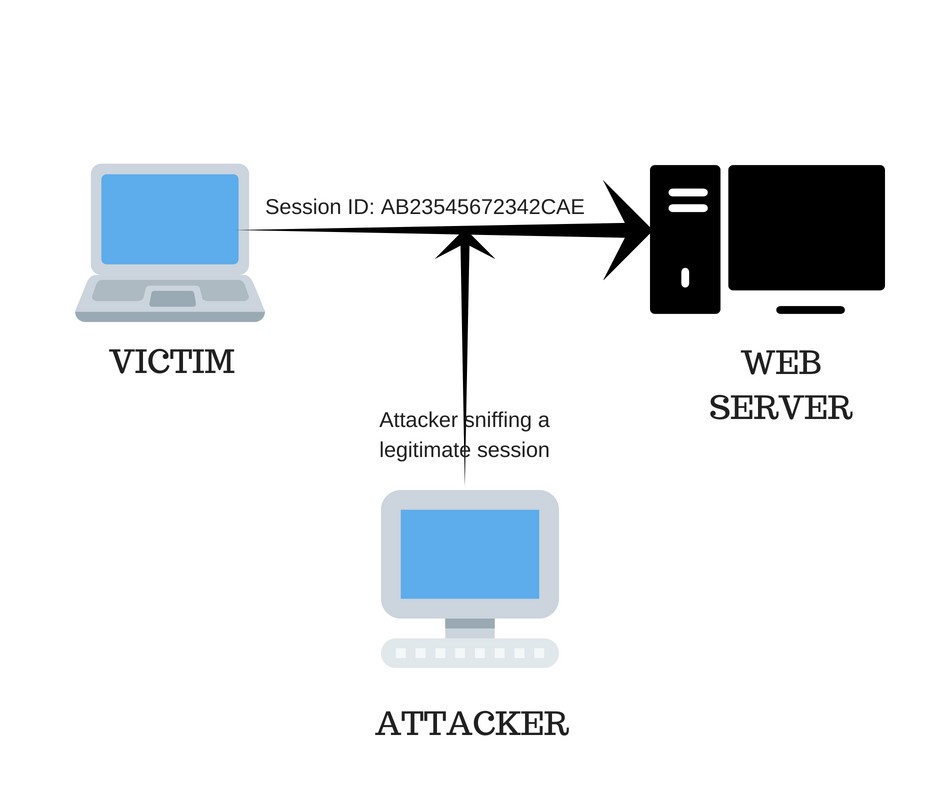
Attackers may make a run at trick the user by making a forged request appear genuine.
This is just one simple example of how an attack can occur using Cross-Site Request Forgery.
Attackers generally use images, cookies, scripts, and HTML to exploit users.

They generally use sniffers to grab the data while it is being transferred via the communication line.
First, let’s define a few key terms:
How is an SSL Connection Established?
First, an SSL connection between a client and a server is set up by a handshake.
In this case, the online window is the client and the website is the server.
Let’s discuss each phase one by one.
Hello The process begins with the client sending a ClientHello message to the server.
In a similar manner, the server sends a ServerHello message containing the information required by the client.
Certain sensitive applications also require the client to send a certificate to the server to prove its identity.
Then the client and the server create their shared secret key, called the Master Secret.
This is done by combining these numbers with some additional information.
The write MAC secret is used for hashing and the write key is the session key used for encryption.
The key that is required for the asymmetric algorithm is generated by the client.
This encrypted key is sent to the server, which decrypts it using its own private key.
The HTTP requests that are in the plaintext format are thus encrypted and sent over the data pipe.
Only the receiving party has the key to decrypt this message.
Therefore,man-in-the-middle attackers are unable to intercept the communication.
How is Trust Established?
so that establish a secure connection, the public key is distributed as part of the certificate.

In contrast, the private key is kept secret.
Alternatively, a legal authority can sign a certificate and encrypt its contents by using their private key.
Now, this newly generated ciphertext is attached to the certificate as a digital signature.
However, it should be noted thatonly a certified authority can actually encrypt content using the private key.
In other words, a valid signature can only be generated by an authority.
kindly, comment on how to improve this article.
