Short on Time?
For phishing hackers, your ignorance is their bliss.
So how do you go about identifying and avoiding phishing attacks?

Well explain below…
What Is Phishing?
Phishing is an exception to this rule as it describeshowthe problem happened, rather thanhowit behaves.
In most cases, scammers are able to convince or coerce their victims into giving over their information willingly.
Its extremely important to protect your personal information, especially sensitive things like your Social Security number.
How Does Phishing Work?
The email is actually fake, but you dont realize it at first.
When you hit the link, the page even looks like Amazons website.
Even the checkout process is the same.
The message offers you an unbelievable discount on a laptop and provides a link to the buying page.
You poke the link to buy it, key in your credit card information, and complete your order.
However, youve just become a victim of a phishing attack.
The product page was fake and disguised very convincingly like the real thing.

Instead of placing your order, the website sent your payment details straight to a thief.
How Can you Recognize the Scam?
In the above case, there were three tell-tale signs.
Attacks can now affect more than just banking.
PayPal, eBay, and Amazon accounts have all reported incidents of phishing attempts on unsuspecting customers.
Watch out for these common types of phishing attacks:
1.
Deceptive Phishing
Deceptive phishing is the most well-known lure.
This strategy involves impersonating a legitimate businesss website to steal data.
It takes a phisher with strong knowledge in social engineering to pull this tactic off effectively.
The phisher then orders employees to send funds to a separate account.
Whaling can also affect other high-profile individuals such as celebrities and politicians.
Phishing Kits
Phishing kits are basically collections of software utilities you’re free to download by mistake.
Once installed, these tools can launch large phishing campaigns and send mass emails to spread the phishing attempts.
Spear Phishing
Some phishers can personalize the fraudulent messages they send you to make them more believable.
These might contain your name, workplace, and phone number gathered through websites like LinkedIn.
In fact,95% of all attacks on enterprise networks are the result of spear phishing.
No losses were recorded, but the outcome demonstrated how dangerous pharming can be.
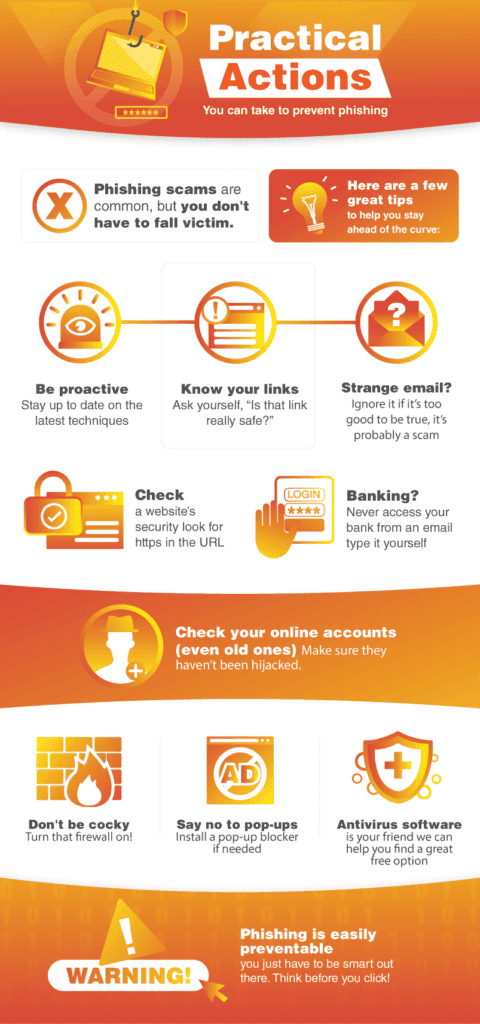
Educate yourself
Knowing that a problem exists is the first step to fighting back.
Careless Internet surfing can leave you vulnerable to phishing attacks.
Theyre common junk mail.
Most of the time, a phishing email might direct you to one of these.
However, a key giveaway is the URL.
Phishing sites may use a slightly different web address containing a small mistake.
PayPal is a commonly masked URL as the lowercase L could be replaced with an uppercase I.
Look for these subtle clues before you engage with the site.
Events likethe hypothetical one abovehave occurred with disturbing regularity throughout the years, victimizing both individuals and entire corporations.
If youre curious about the specifics of the AOHell scam,check out this paper by Koceilah Rekouche.
He established the National Cyber Investigative Joint Task Force specifically designed for these kinds of attacks.
The phishers then managed to bypass the companys SecurID two-factor authentication to steal company data.
The phishers posed as tax consultants and convinced thousands of victims to download malicious executable files.
While the final arrests were made in late 2015, the legacy of the cyberattack lives on.
The Sony Pictures Leak
2014 also sawa huge data leak from Sony.
Over 100 Terabytes containing confidential company activities was breached, resulting in well over $100 million lost.
The phishers pretended to be colleagues of the top-level employees who opened the malicious attachments in the phishing emails.
Specifically, a fake Apple ID verification email was used in the attack.
Facebook and Google
This is a huge one.
At the same time, a handful of rental scams were reported as well.
Once a lucky buyer accepted the offer, his or her credit card information was stolen.
But they arent a death threat.
There are plenty of easy steps to take to lower your chances of losing your data to phishers.
A little awareness now can save you a lifetime of battling debt collection agencies and cases of identity theft.
Lets rather be safe than sorry.