It also offers additional benefits, such as safe emailing and torrenting tools.
What Is the I2P web connection and How Does It Work?
These parts are sent through various tunnels, with each part taking a different route.

This process prevents a single entity from intercepting the complete data, thus preserving your privacy and security.
This makes it hard for snoops to analyze the traffic and link messages to specific users.
The internet also provides a secure way to communicate or share information with minimal fear of being hacked.
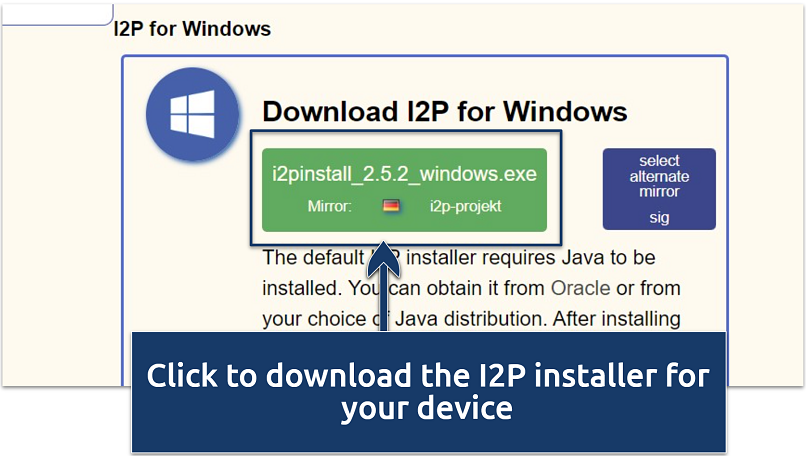
Make sure you’ve also installed Java before you begin
I2P hides users' IP addresses and encrypts all datatransmitted over the data pipe.
This keeps your online activities private and protected from prying eyes, safeguarding against surveillance and data tracking.
This also means consistent connection availability and reliability, even in restrictive environments.

Make sure you’ve also installed Java before you begin
It also provides a platform for developers to create privacy-focused apps.
It features thousands of torrents that can be loaded onto your torrent client for secure, anonymous file sharing.
I2P is an open-source project that is continually improved and maintainedby a dedicated community of developers and users.

This collaborative effort helps keep the connection up to date with the latest security enhancements and features.
Running the I2P client can consume significant amounts of CPU and memory, affecting the performance of other applications.
This potential for misuse may also attract unwanted attention from law enforcement agencies.
Each achieves enhanced security in different ways suited to various use cases.
Outproxies, which are similar to Tor exit nodes, can be used to enter the clearnet with I2P.
However, this reduces privacy as your data leaves the online grid and is a less common use case.
The content on freesites (Freenet sites) can be accessed even if the original publisher isnt online.
Also, users can securely and privately share files, publish websites, and interact through forums.
Freenet doesnt have exit nodes, so it cant be used to browse the regular internet.
It focuses on providing secure P2P communication data privacy using encrypted tunnels and a sophisticated routing system.
I2P is decentralized and does not rely on a central authority.
It’s natively supported on Android mobile devices but not iOS.
Linux users can use I2P on Debian Ubuntu or Mint, but it doesn’t work on Tails anymore.
That said,you’re able to easily set up I2P with privacy-friendly browsers like Firefox or Brave.
Without Java, the I2P client installation can fail.
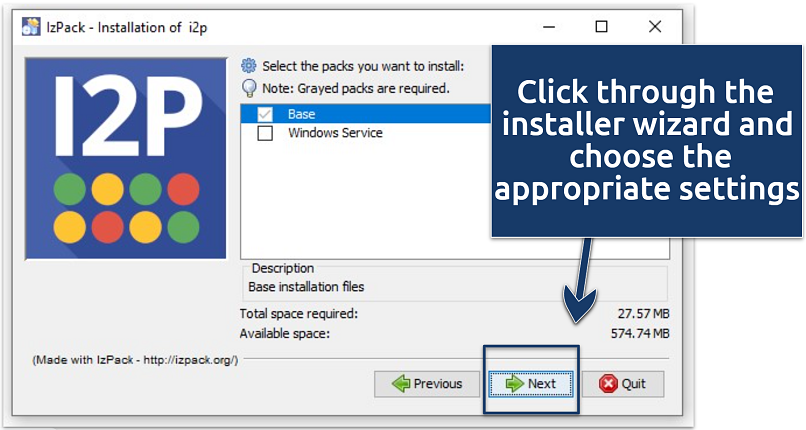
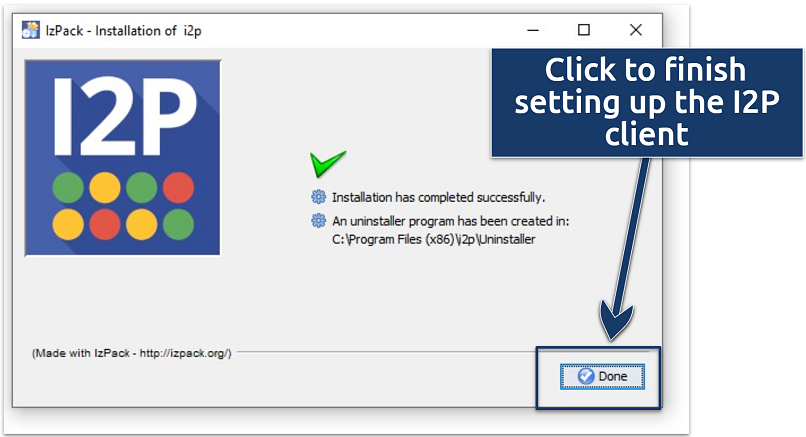
Here is a step-by-step guide to installing I2P on a desktop platform.
My guide uses Windows, but the procedure is similar for macOS.
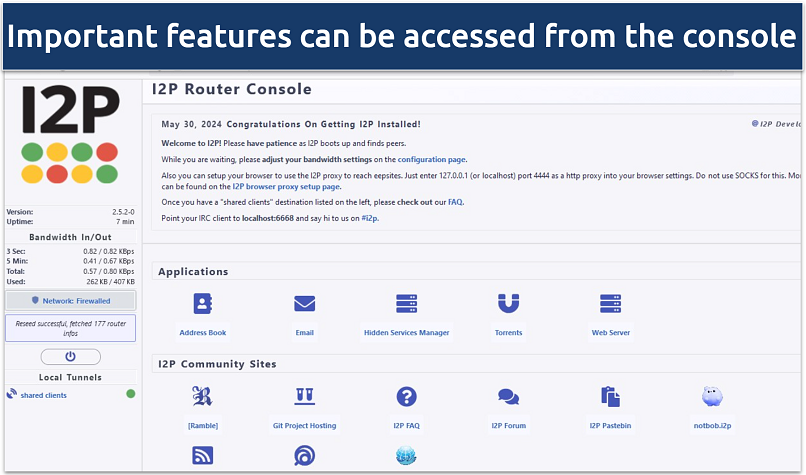
How to Use I2P
The I2P internet offers privacy-focused features to help keep your online activities secure.
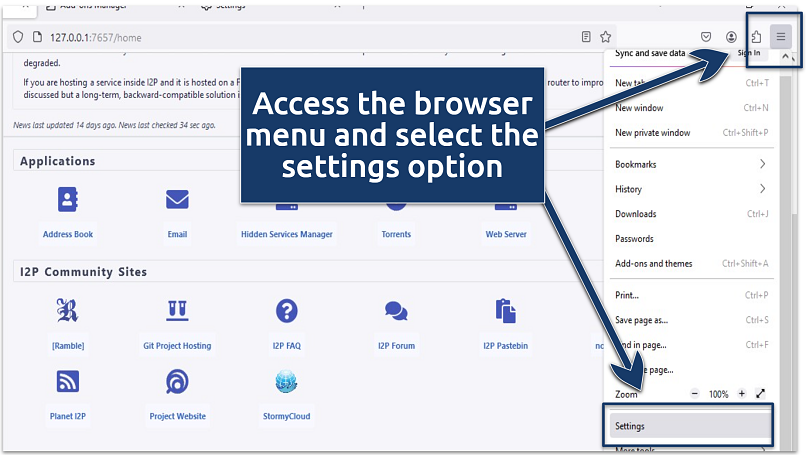
Heres how you’re free to get the most out of the app.
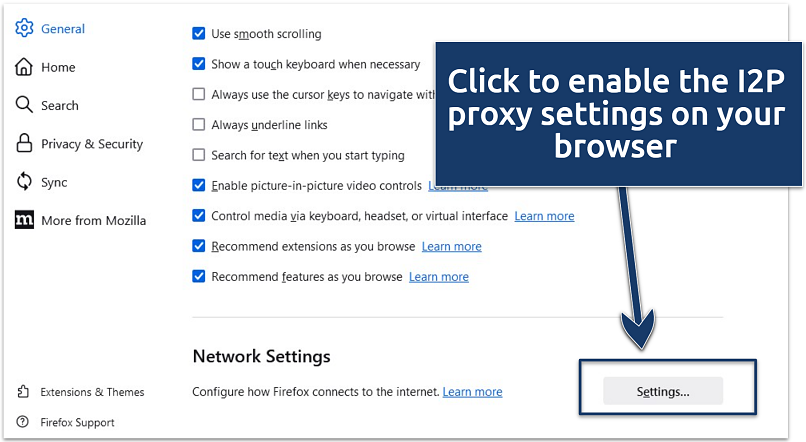
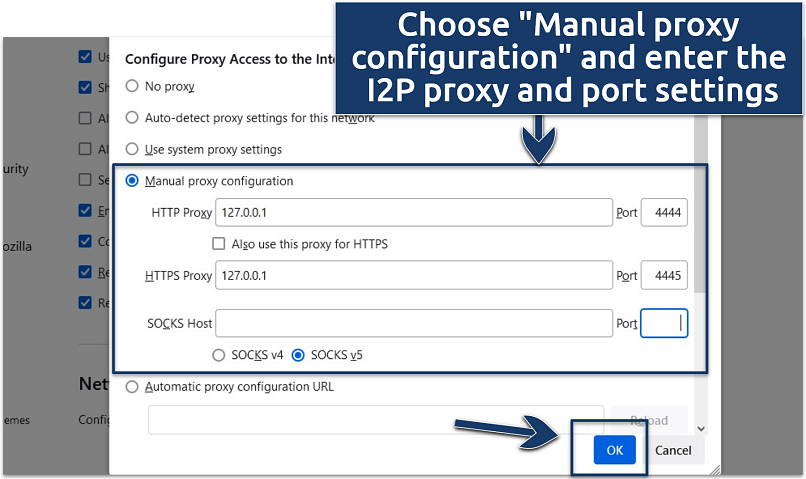
To start browsing privately online, you first need to configure your net online gate to work with I2P.
Firefox offers dedicated features for I2P (including extensions) and integrates well with the client.
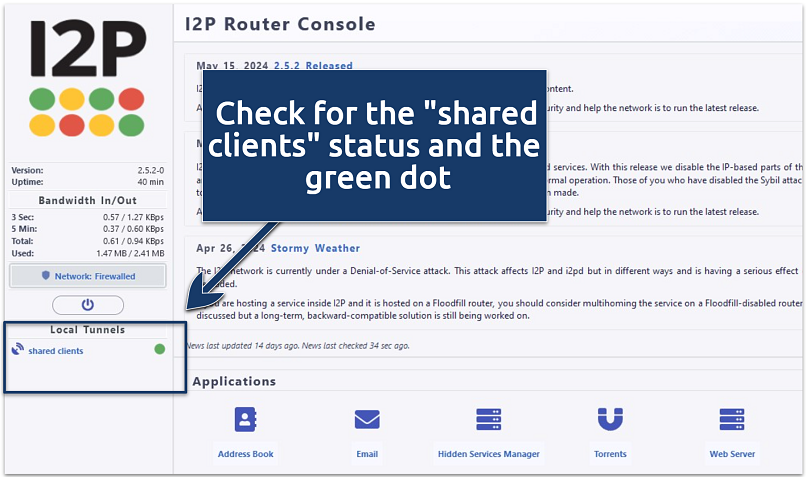
Youre all set to get started with I2P.
Heres how:
FAQs about the I2P internet
Is the I2P internet legal?
Is I2P safer than Tor or a VPN?
Eventhe underlying working mechanisms between I2P and other dark web networks differ slightly.
I2P uses garlic routing, which is robust for communications within the connection.
Tor uses onion routing that supports safe browsing in and outside of the internet.
A VPN, on the other hand, secures all your internet traffic including browsers and applications.
Which online window should I use with I2P?
Firefox offers features that integrate well with I2P, allowing you to configure the necessary proxy configs easily.
Extensions like I2P In Private Browsing (on Firefox) also offer more convenient features.
How can I fix the I2P firewalled error?
If not, it could be that your data pipe doesnt allow I2P traffic to pass through.
Tryopening the specific ports used by I2P on your router.
Enable port forwarding for ports 8887 and 8888 (or other ports if you’ve configured I2P differently).
Also, check that any firewall software on your system, like an antivirus, is not blocking I2P.
It has some drawbacks, like limited content (compared to the clearnet) and, sometimes unstable speeds.
Your data is exposed to the websites you visit!
Visit ExpressVPN
hey, comment on how to improve this article.








