Encryption is used nowadays on even the simplest of apps.
Other popular apps, likeWhatsAppand Gmail, also use some sort of encryption.
But, while we use cryptography in our daily lives,most of us dont know how it works.
To help us understand how cryptography works, were going to look at a practical example.
The first implementation isa simple TCP-based communications channel.
Since theres no security,every message users send is open to attack.
Hackers can also alter the messages and reroute them.
This is possible because the default communication channel passes the messages in plaintext.
It does the same withall HTTP communication over open Wi-Fi networks.

Clearly, we need a better system.
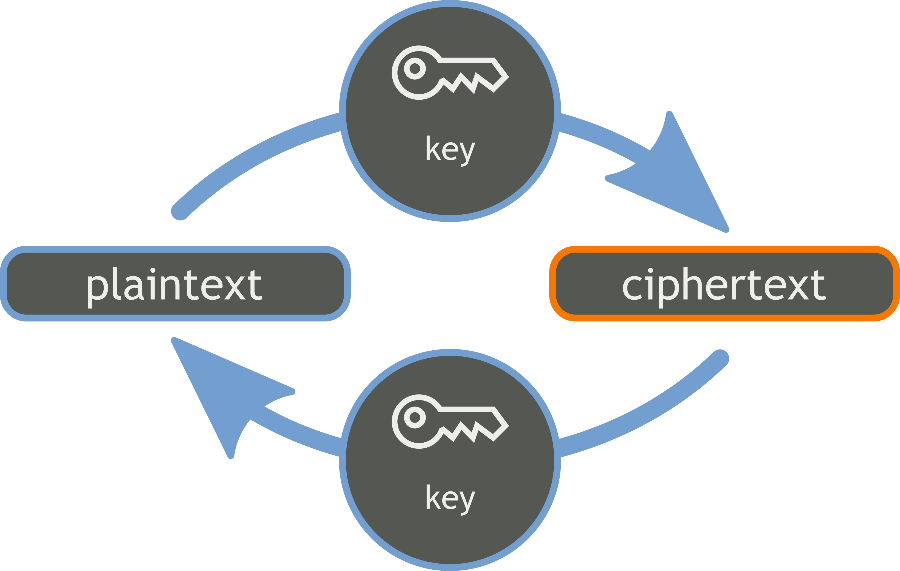
When Alice wants to send Bob a message, she encrypts it with a symmetric key.
When Bob receives it,he uses the same key to decrypt the message.

Without it, attackers cannot reach the encrypted communication between the two users, keeping it confidential.
Typically,a symmetric key is generated per session and is invalid for subsequent communication.
We call it a session key.
However, there are shortcomings to this approach:
So, whats the next step?
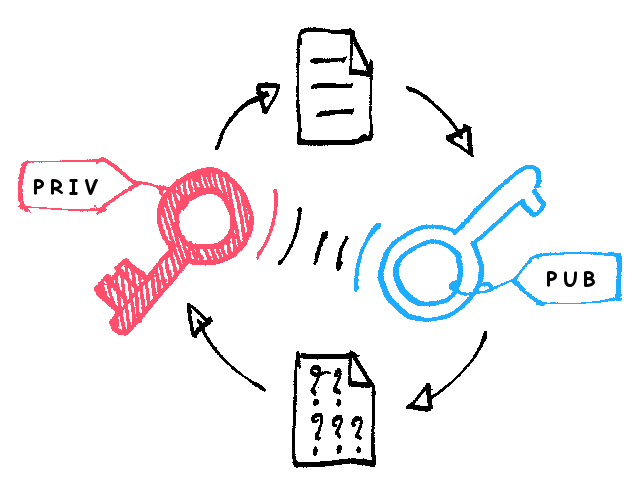
When Alice wants to send a message to Bob,she first creates a symmetric session key.
She then encrypts it with Bobs public key.
Since Bob owns the corresponding private key,only he can decrypt the message and get the session key.
From then on, that session key can be used to encrypt and decrypt messages between the two.
Now the system has improved significantly, but it is still not completely secured.
One root certificate is linked to various child certificates with digital signatures (described below).
Lets call this data packet PART1.
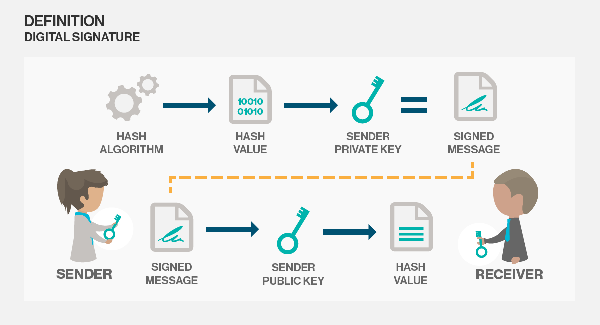
Then, she creates a message hash using one of the many available hashing algorithms (MD5/SHA256).
A message hash is a one-way conversion from a variable length byte to a fixed-length one.
The digital signature and the original message is then encrypted with the session key.
Lets call this one PART2.
Since he owns the private key,only Bob can decrypt PART1 and reach the SESSION_KEY.
Next, he uses this session key to decrypt PART2 and retrieve the message and digital signature.
He then uses Alices public key to decrypt the digital signature and retrieve the message hash.
Bob calculates the MESSAGE hash and compares it to the one from the earlier step.
As you’ve got the option to see, we have now built a completely secure ecosystem.
hey, comment on how to improve this article.



