This is an unorthodox way of making a program do something it isn’t intended to do.
So what is DLL hooking, and how does it actually work?
What Is a DLL?

Every app depends on some files outside its base code to run.
These external files contain code and data a program needs to function properly.
In the Windows operating system, these external files are called DLL or dynamic link libraries.
External files on Windows are known as libraries.
There are two types of libraries: dynamic and static.
Dynamic libraries are loaded at run-time and static libraries are loaded at compile time.
DLL is a dynamic library.
What Is DLL Hooking?
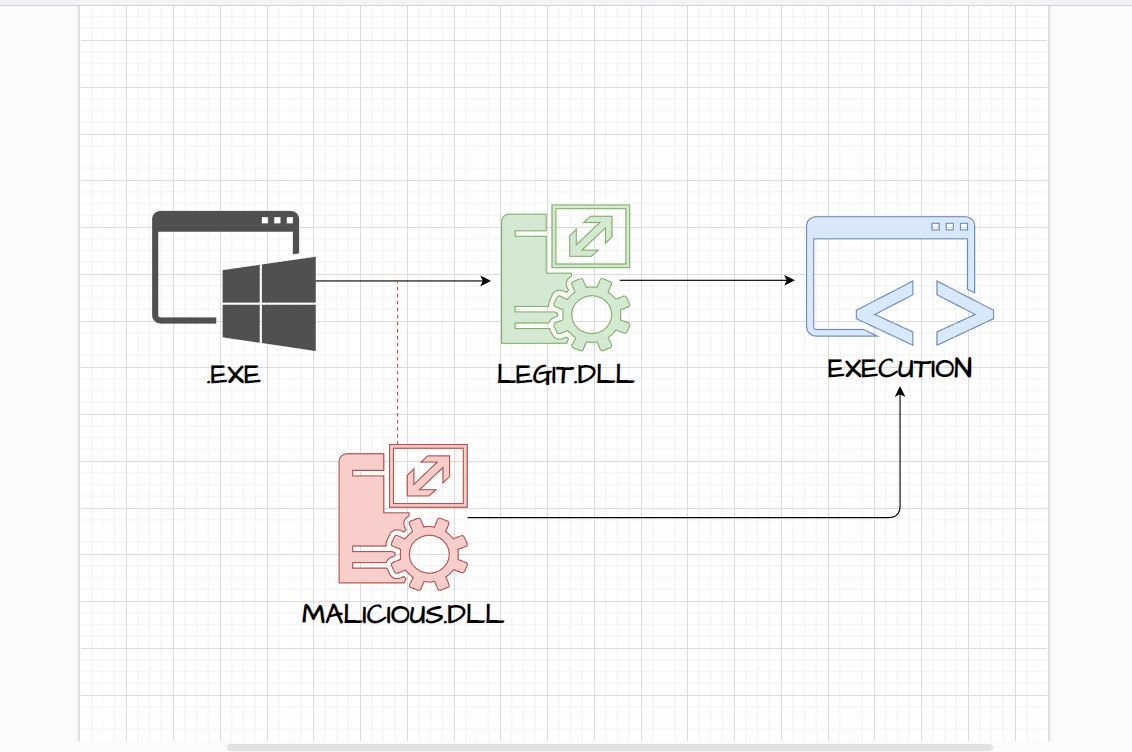
DLL hooking is a technique that includes intercepting and altering function calls programs or processes make to a DLL.
Essentiallya Man-in-The-Middle setupis established where a hook sits in between a program and the DLLs it calls.
All or targeted function calls are then traced and altered.
How Does DLL Hooking Work?
Before diving into implementing DLL hooking, it’s important to clear up the basics.
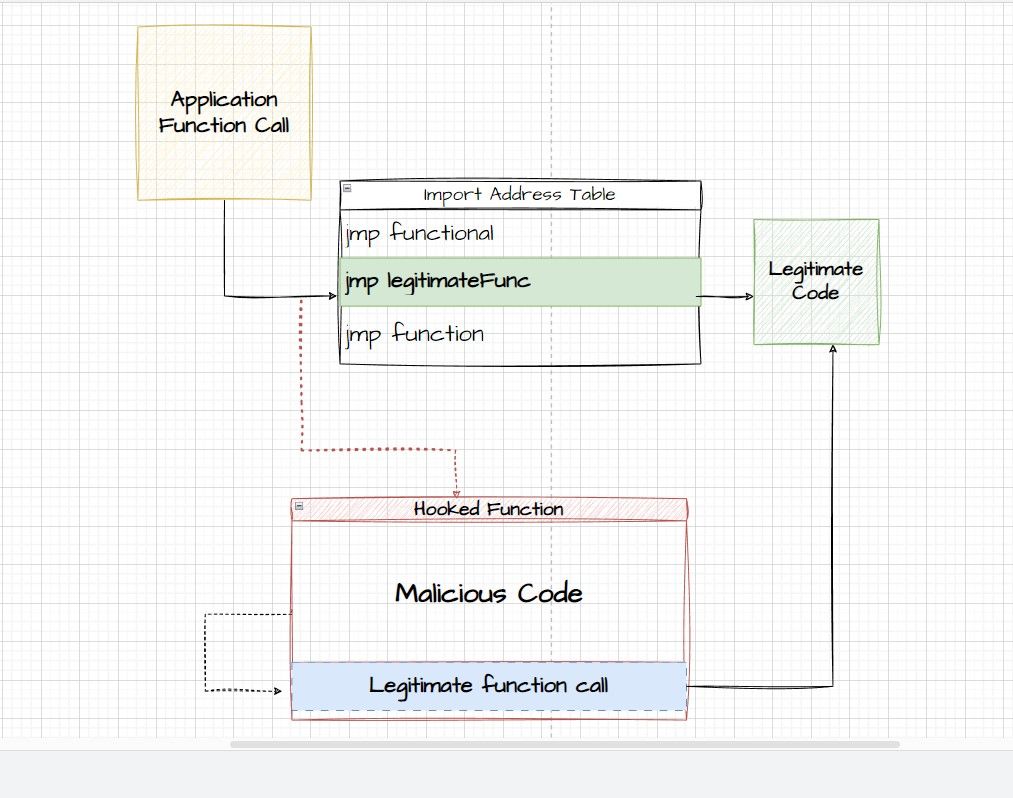
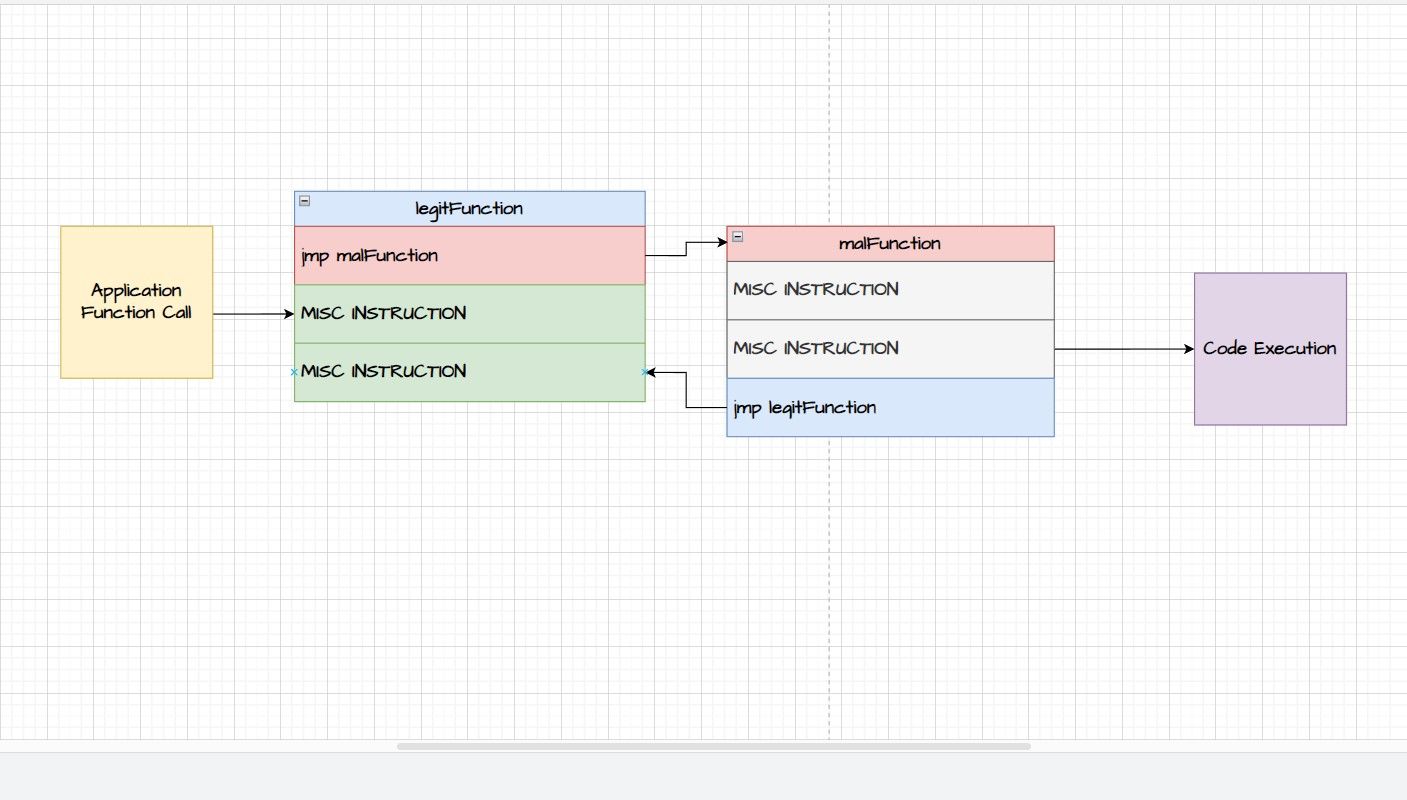
DLL hooking revolves around intercepting this process and redirecting the function call to a different function.
There are several ways to implement DLL hooking.
Let’s look at the most commonly used techniques for implementing it.
IAT contains the names of all the imported function calls and their memory addresses.
It is a data structure where all the functions exported by the DLL are mapped to their memory addresses.
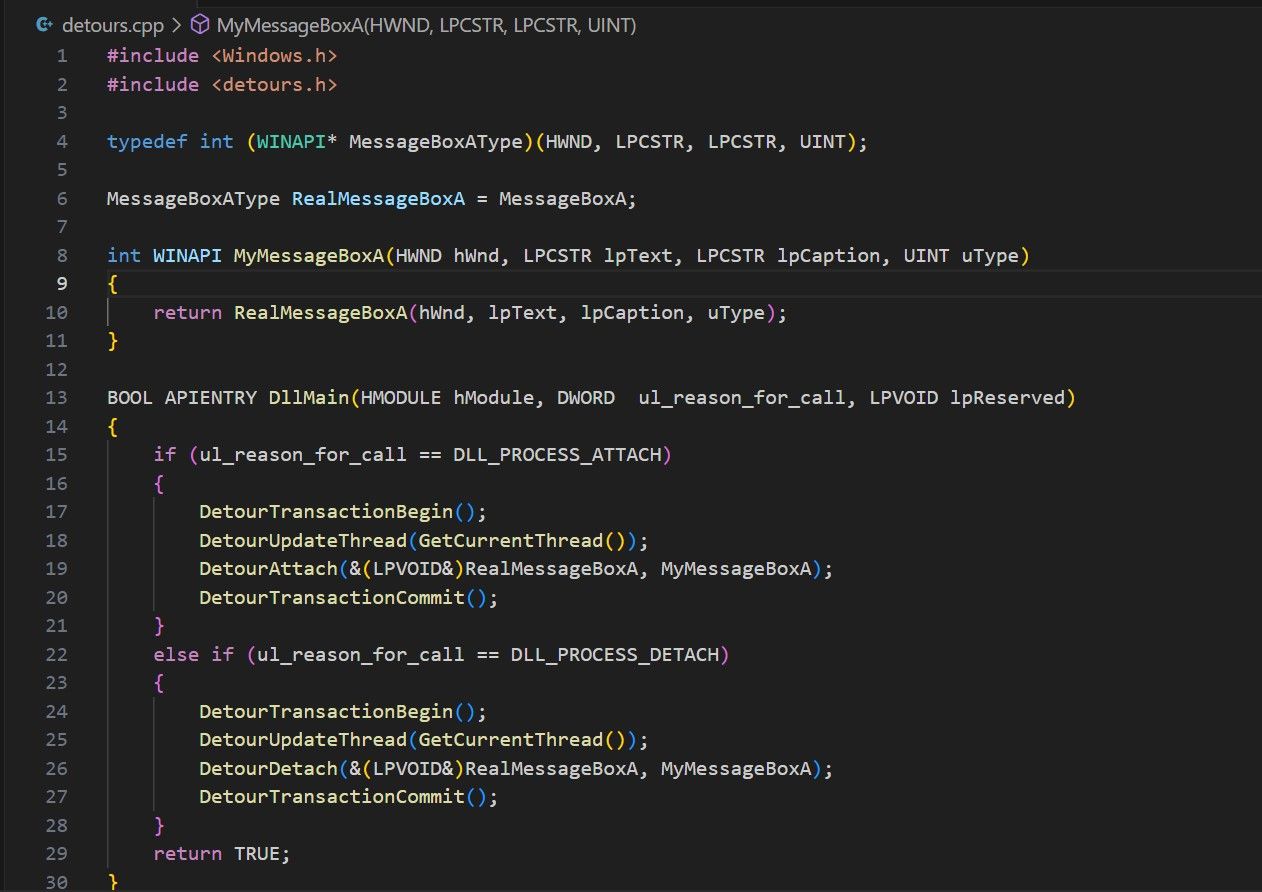
Microsoft Detours
Microsoft Research has developed an in-house DLL hooking package, Detours.
It enables programmers to track and alter function calls made by a program.
it’s possible for you to learn more about the Detours package on theofficial GitHub repository.
Unfortunately, hooking is more commonly seen in use as an adversarial technique rather than a development one.