The cybersecurity landscape has seen a significant escalation in threatsover the past year.
This highlights how widespread and damaging these exploits can be.
What Is a Zero-Day Exploit?

What Is the Difference Between a Zero-Day Exploit, Attack, and Vulnerability?
On the other hand,zero-day exploits target unknown vulnerabilities.
This makes zero-day exploits especially difficult to defend against in real-time.
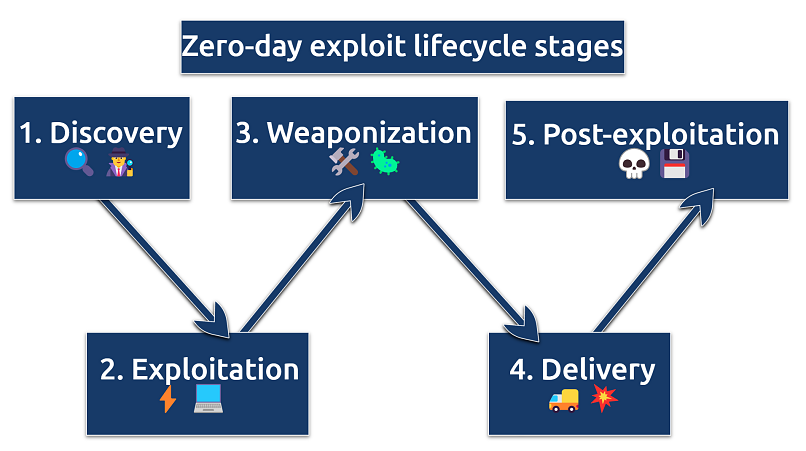
These stages highlight the rapid and stealthy nature of zero-day exploits
Why Are Zero-Day Exploits Dangerous?
Hackers may use various methods to deliver the exploit, such as phishing emails or malicious downloads.
Who Performs Zero-Day Exploits?

These stages highlight the rapid and stealthy nature of zero-day exploits
How Zero-Day Attackers Find Vulnerabilities?
Reverse engineering involves deconstructing software updates or patches to uncover weaknesses in the code.
Vulnerability scanning tools automate the process, searching for flaws the vendor has not yet discovered.

Government agencies are also high-value targets for espionage or political gain.
How to Detect Zero-Day Exploits?
Traditional detection methods, like signature-based tools, work by spotting known patterns or signatures of malicious code.
But with zero-day exploits, theres no existing pattern to recognize, making these methods ineffective.
Instead,behavior-based detection focuses on monitoring activity within a internet and flagging anything unusual.
This approach helps organizations spot potential threats even when no clear signature exists.
How to Protect Yourself Against Zero-Day Exploits?
However,combining antivirus tools with additional security measures is essential for stronger protection.
How long does it take for a zero-day vulnerability to be discovered and patched?
However, it’s important to note thatzero-day vulnerabilities may remain undetected and exploited for extended periods before discovery.
Are zero-day exploits only a risk for large organizations?
What should I do if I think Ive been affected by a zero-day attack?
If you’re part of an organization, notify your IT team or a cybersecurity professional.
Taking steps to strengthen your security can also help prevent future incidents.
How does a zero-day vulnerability differ from malware?
What is the difference between a zero-day bug and a backdoor?
What is the difference between a zero-day attack and ransomware?
References
Your data is exposed to the websites you visit!
Visit ExpressVPN
c’mon, comment on how to improve this article.


