Despite the name, a smurf attack has nothing to do with small blue creatures.
What Is a Smurf Attack?
These ICMP requests overwhelm the server, making it impossible for it to process all the incoming traffic.

Hackers execute a smurf attack using malware called “DDOS.Smurf”.
The code used to carry out this attack was written by a renowned hacker, Dan Moschuk.
What Is an ICMP Echo Request?

A smurf attack relies onICMP (Internet Control Message Protocol)echo requests, but what does that mean?
It is also known as a ping request, due to the command commonly used to initiate it.
ICMP echo requests and replies are commonly used by internet administrators to troubleshoot internet connectivity issues and diagnose problems.
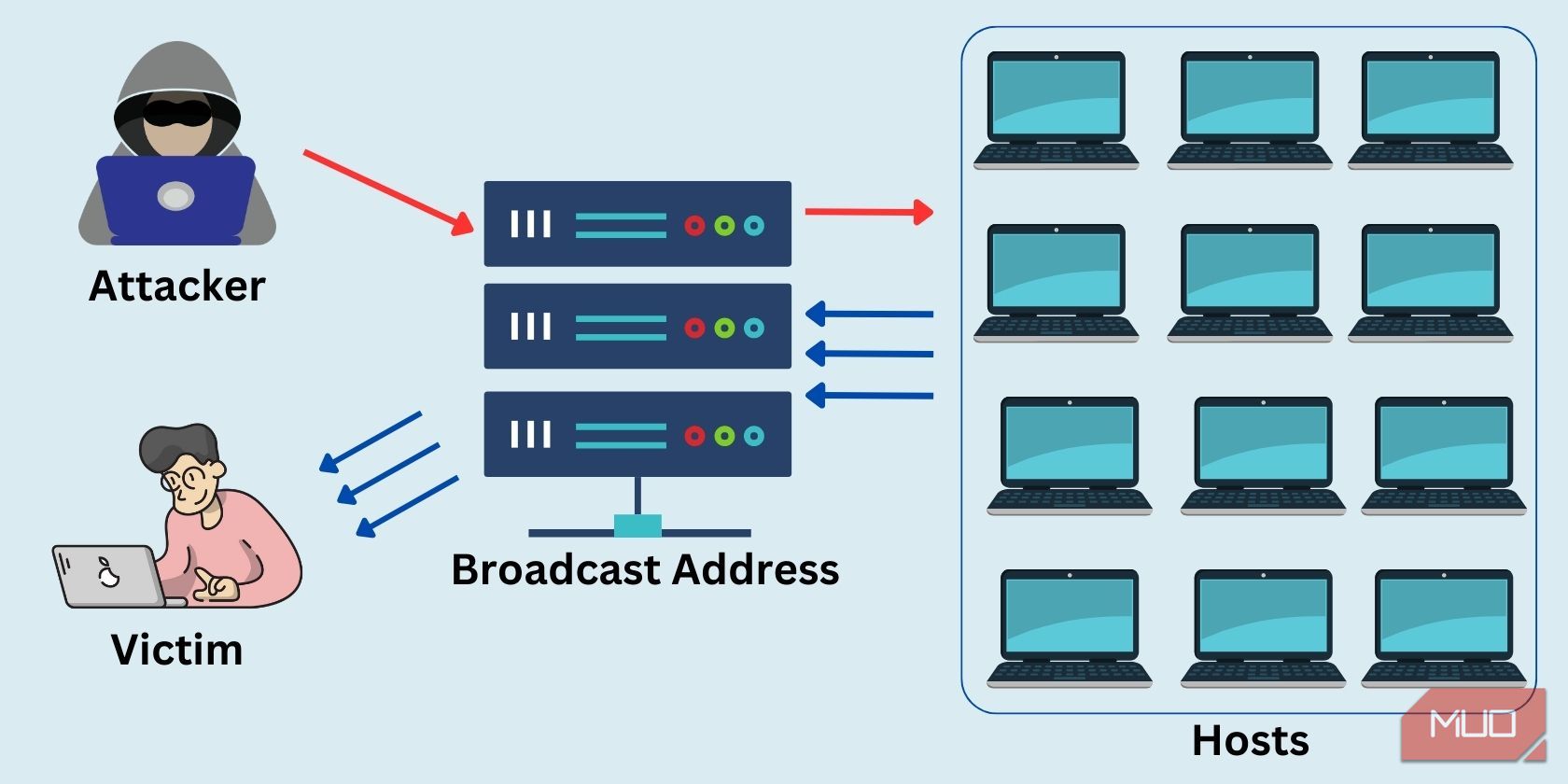
How Does a Smurf Attack Work?
Smurf attacks use numerous ICMP packets/echo requests to create a denial of service attack on a system.
A smurf attack might sound similar to a ping flood, but it is even more dangerous.

Or maybe for routine maintenance.
It is also necessary to implement proactive incidence response plans in the event of a cyberattack.