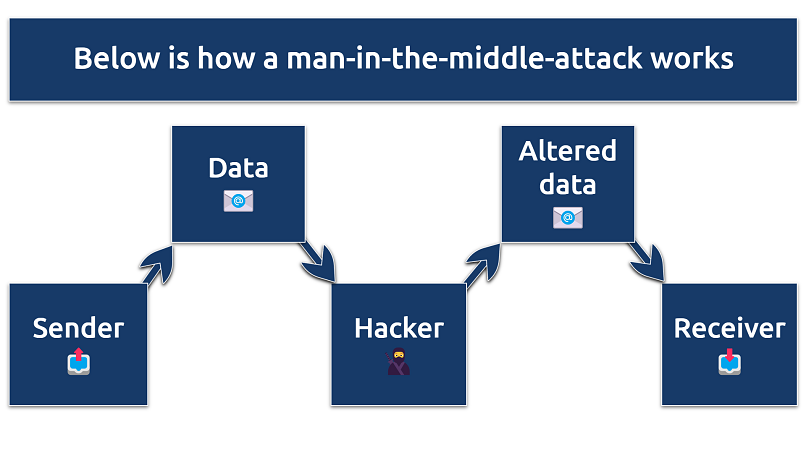
Understanding and preventing MITM attacks is essential to ensuring your privacy and security online.
These attacks often target users of financial apps, SaaS platforms, and e-commerce sites.
Below is a step-by-step guide to help you protect yourself against MITM attacks by using a VPN.

Step 1.
Choose a Reliable VPN Provider
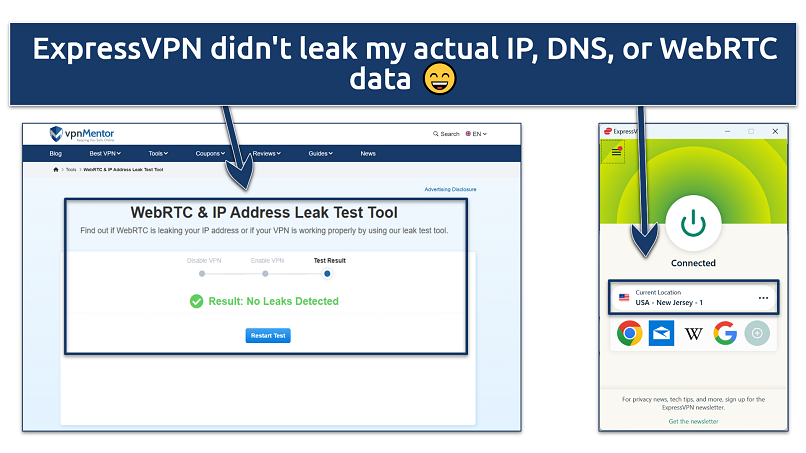
My top recommendation is ExpressVPN.
It’s the most reliable and fastest VPN we’ve tested, allowing secure browsing from any location.
Additionally, this VPN is very user-friendly across all devices.
Step 2. launch the downloaded file and follow the on-screen installation instructions.
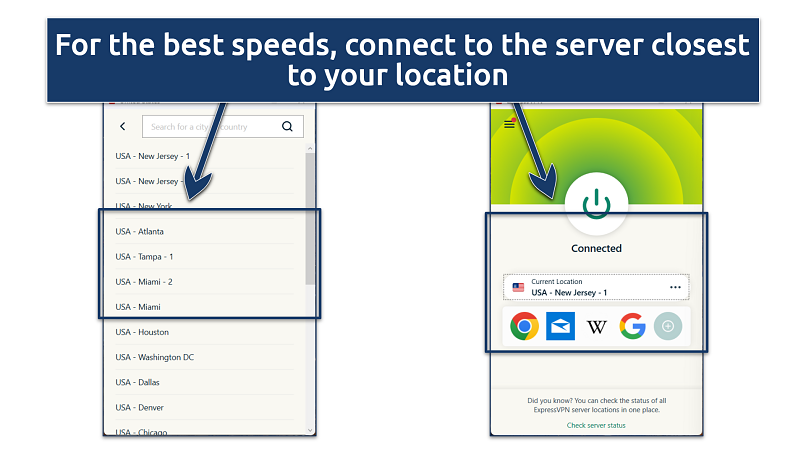
Step 3.
For the best speeds, choose a server close to your physical location.
Click theConnectbutton to establish a secure connection.
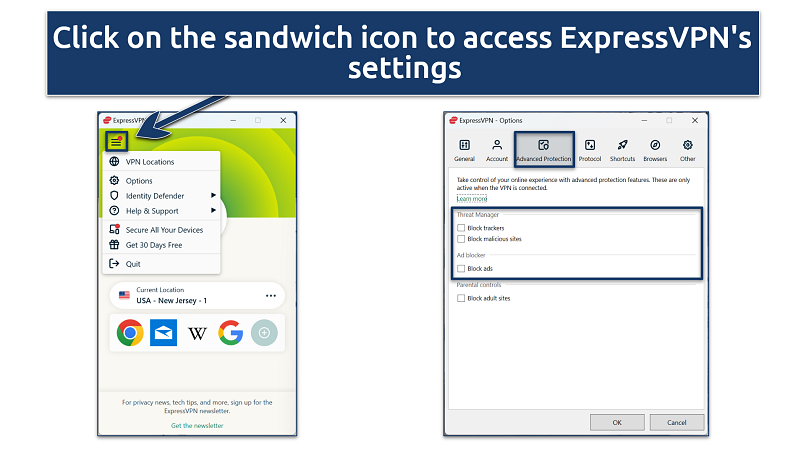
Step 4.
Turn On Extra Security configs
Access ExpressVPNs app configs.Locate theAdvanced Protectiontab, then toggle all theThreat ManagerandAd Blockerboxes.
If necessary, you’ve got the option to also enable parental controls.
Step 5.
They are also compatible with all major devices and operating systems.
My only issue with the service is its expensive pricing.
That said,ExpressVPN frequently offers generous discounts that bring the price down to just$4.99/month.
Plus, with a 30-day money-back guarantee, you might try it risk-free.
A downside is that monthly plans are pricey and offer only a 14-day refund period.
One issue is that apps might appear complex for beginners.
However,the service is pre-configured for secure browsingright from the start.
Plus, all PIA apps are open-source and available on GitHub, enhancing their transparency.
you might get PIA for as low as$2.03/month.

Our evaluation covered encryption protocols, no-logs policies, and leak protection to provide maximum data security.
Additionally, we performed speed tests across various server locations to determine how each VPN affects performance.
Lastly, avoid unsafe WiFi whenever possible.Public WiFi networks are often a common starting point for MITM attacks.
If it’s crucial that you connect in public, use a secure VPN.
By combining these tools, you’re able to build a more complete defense against cyber threats.
Such breaches may also entail legal repercussions, further complicating the aftermath for affected entities.
However,specific signs and methods can help identify potential MITM activity.
By unknowingly connecting to this fake connection, you allow the attacker to intercept all communications exchanged over it.
MITM vs Replay Attack
A MITM attack involves intercepting and potentially altering communication between two parties.
This tactic is a targeted approach within the broader category of MITM attacks.
Protecting against MITM attacks is crucial to prevent more advanced threats like APTs.
FAQs on the Man-in-the-Middle Attacks
Can HTTPS prevent all MITM attacks?
Who are the three main participants in a man-in-the-middle attack?
What is the difference between man-in-the-middle and meet-in-the-middle?
Can I use a free VPN to protect from a MITM attack?
However,youre better off using a premium VPN with a money-back guarantee.
Free VPNs pose risks, such as data logging and unreliable privacy policies, which could compromise your security.
Plus, many free VPNs dont work on more niche operating systems, like Kali Linux.
To summarize, these are the best VPNs for preventing MITM attacks…
Your data is exposed to the websites you visit!
Visit ExpressVPN
yo, comment on how to improve this article.









