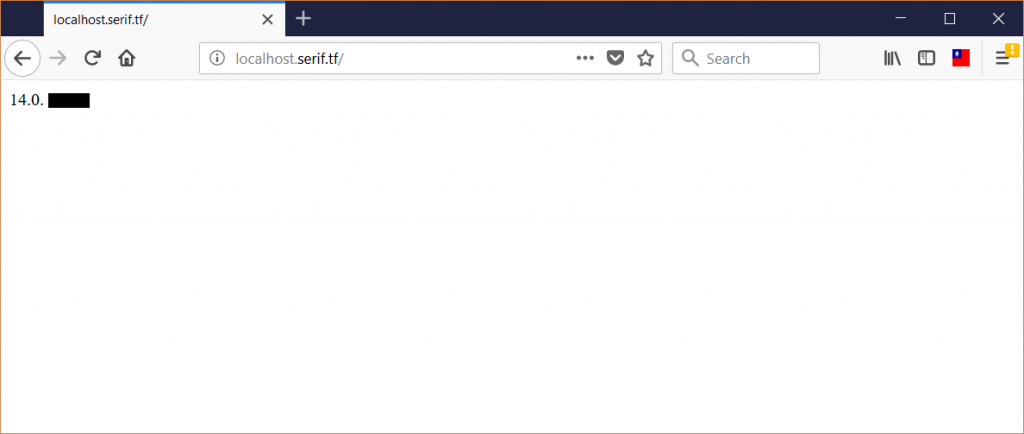
While we hoped to find zero leaks, we regretfully found thatall of them leak sensitive data.
His work was mentioned in ZDNet, SlashDot, and other media sources.
Therefore any URL with the aforementioned parameters will have the traffic routed to the specified proxy.

It would be worse if the connection is on HTTP.
How do we prove it?
A simple check in https://www.dnsleaktest.com/ reveals your DNS server.
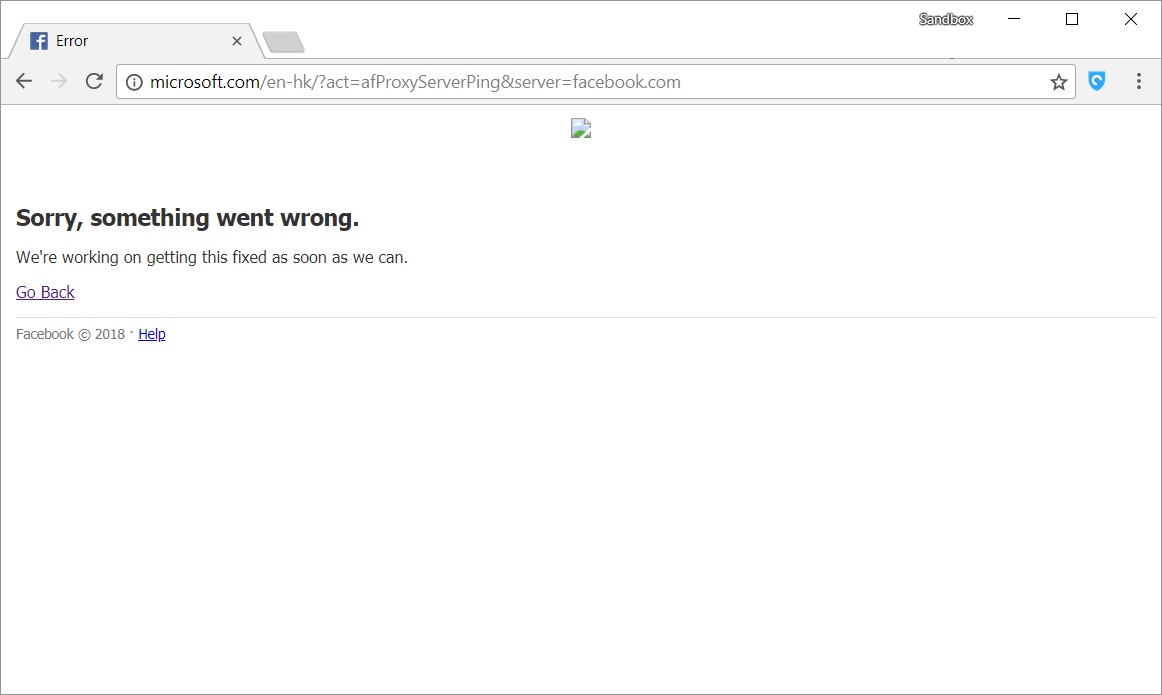
This is a result of the proxy hijack.
This example shows the leak we found with HotSpot Shield.
This website serves as a tool designed to assist you in verifying such occurrences.
CVE-2018-7880 IP leak
What we found is thatthe whitelist for DIRECT connection is just too loose.

This is a result of the proxy hijack.
While they are not exactly like HotSpot Shield’s vulnerabilities, they are similar.
The vulnerabilities they reported werepresent only in the free Chrome plug-in.
Neither mobile nor desktop users of the Hotspot Shield app were affected by these vulnerabilities.

Moreover, we also mention that on the description of the extension in the Google Chrome Webstore.
Many services rely on P2P realtime communication to function properly, e.g.
Google Hangouts would stop working if WebRTC would be disabled.
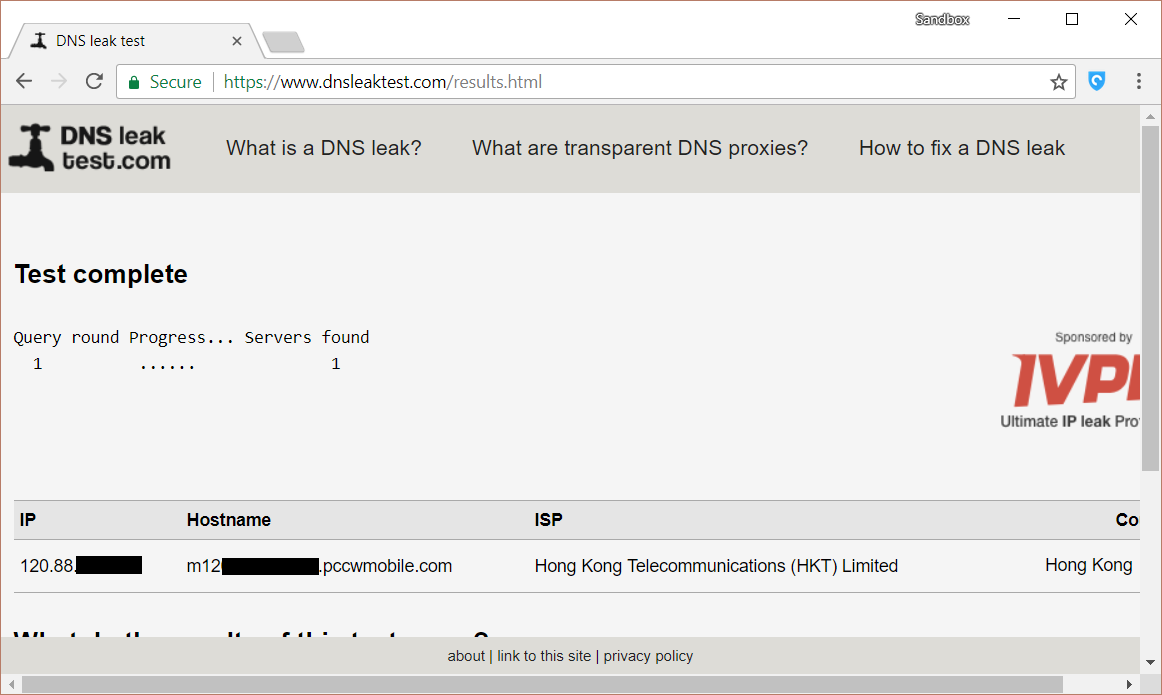
Our intention was to allow users the freedom to access all local domains conveniently while using our extension.
What does this mean to a VPN user?
VPNs are not as safe as many may think.
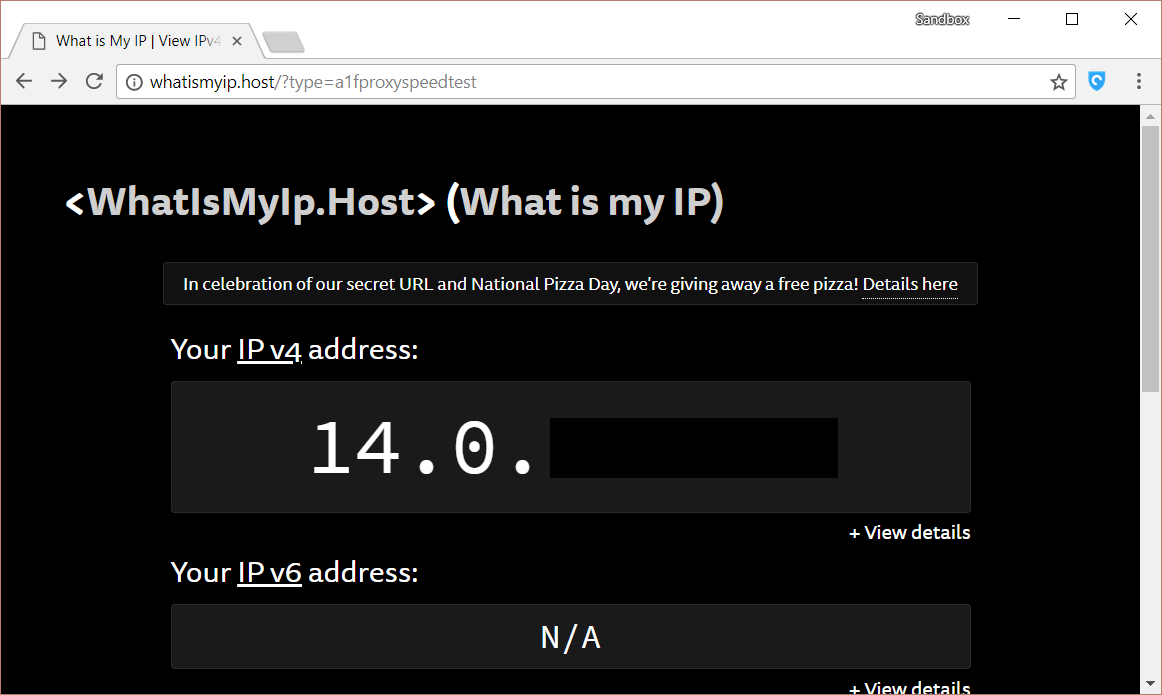
The fact that we found leaks in all the VPNs that we tested is worrying.
If you use Hotspot Shield or PureVPN user ensure you have updated your app.
Share these results on Facebookortweet about this.
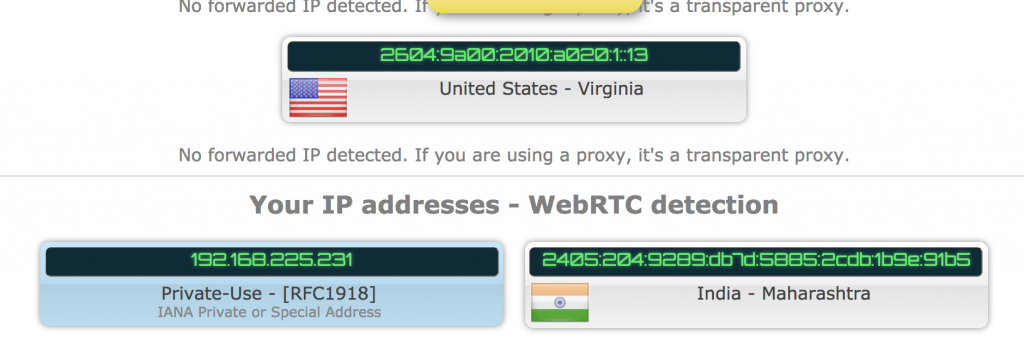
A simple check was able to determine that ZenMate’s VPN leaked our location.
like, comment on how to improve this article.