When was the last time you thought about your WiFi router?
These vulnerabilities provide them a master key to millions of homes.
You would think that the company that gives you secure internet access is also protecting your privacy.

But it isn’t.
The ISP router comes with default keys and passwords that turn on the company to spy on you.
They may say they need your information to maintain their quality of service.
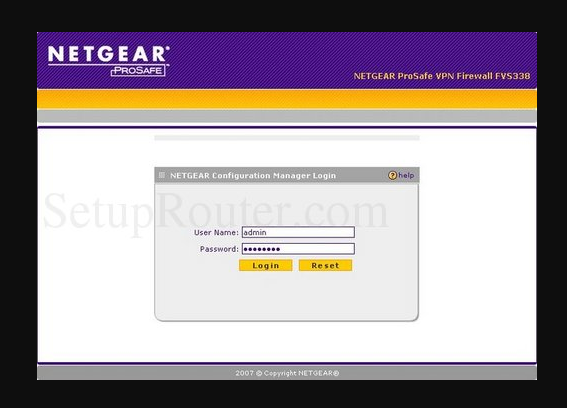
Netgear login screen
But your ISP is also in the money-making business of keeping your data accessible for target-marketing purposes.
But Im also a family man - with a deep devotion to protecting my home.
Some of my tactical tips to take control of your router may require some special tools and services.

Netgear login screen
However, the vast majoritywill cost you NOTHING, and you’re able to do it yourself.
To control these, you should probably get into your router’s interface its console.
The idea is to let you or your ISP technician set up your router by using universal administrative credentials.

These credentials are public knowledge.
However, suppose you keep these defaults to access your router.
How to Access Your Routers configs
Your router consists of embedded service software that controls it firmware.
A router’s firmware consists of a console of commands that is your router’s interface.
The screen will look something like this:
Sometimes, however, routers use a different IP address.
However, dont worry only the router youre using on-site at your home will accept these defaults.
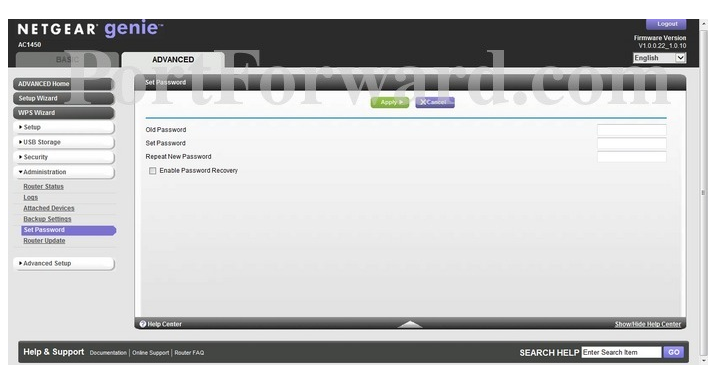
So, change the user name and password that you use to access your router.
Note that all routers have a specific way of changing their default administrative credentials.
Important Note: Not all Routers were created Equal!
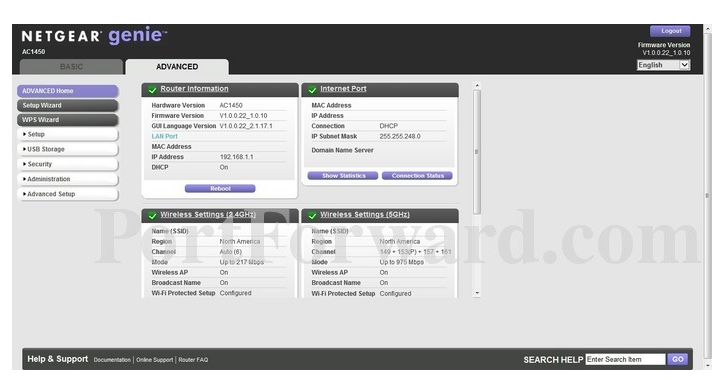
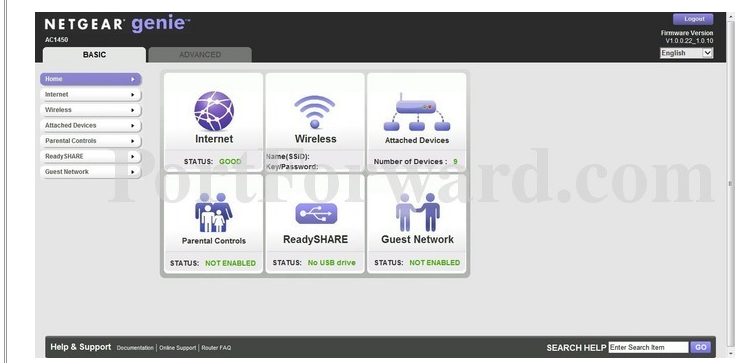
The Basic tab give you information about the router and your internet access stats.
The Advanced tab give you the options for changing the parameters.
You might want to punch all of the available tabs to see what your router offers.
Most people are usingboth the password and the SSID your ISP gave them as default codeswith the router.
The problem is, your ISP probably doesnt provide each consumer a unique password.
For instance, it may assign stormynight 465 to one user while assigning stormynight327 to another.
Thats when they begin brute-force attacking - inputting all possible combinations of alphanumeric codes to locate a password.
Why would you let anyone else assign you a personal password?
punch Repeat New Password and re-put in your new password.
How do I choose the right password?
Wow, so much to remember.
You might become password-weary.
It simply means that you use a combination of the same alphanumeric codes over and over again.
This is the most archaic, most well-known password since “Open Sesame.
Perhaps with less creativity, users will choose their phone number.
It would be best if you choose the right password.
But lets say your residence is near a public WiFi hotspot - like a cafe.
Any intruder may press that internet and also see the other nearby internet names.
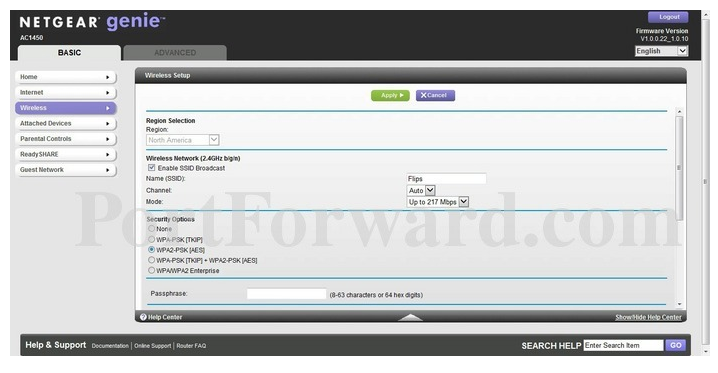
Its important that, as with your router password, you change the web link name to something secure.
,strong.One last tip: Your ISPs manual may caution you against changing the web connection setting.
Your router controls the encryption standards for your WiFi access.
However,ISPs dont always turn on these protocols by default.
Why not?Well, some fear it will impact performance or just not aware of its importance.
But don’t worry;it’s possible for you to easily switch on the necessary protocols yourself.
The most common WiFi security types areWEP, WPA, and WPA2.
WEPstands for Wired Equivalent Privacy.
It was the initial wireless encryption protocol to emulate the encryption available on traditional wired networks.

WPA- or WiFi Protected Access - debuted in 2004 and fixed many of the security gaps of WEP.
The WiFi Alliance fixed that problem a couple of years later with the release ofWPA2 (AES).
Instead, it provides several WPA security options for WPA2.
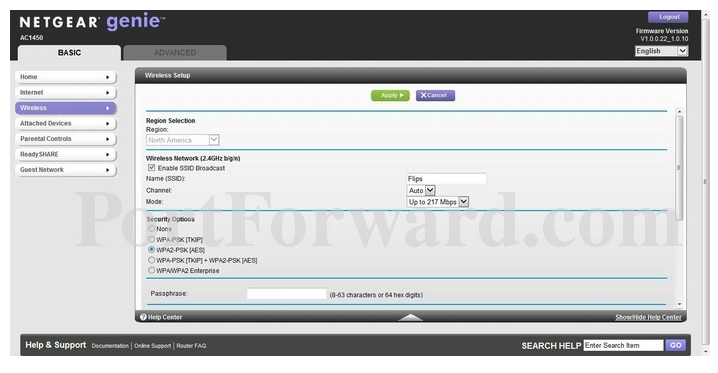
On the Netgear AC1450 - Go to the main page of the router console.
So now set your AC1450 encryption standard:
You may see other options.
TKIP is a legacy key that would unlock the router to go beyond WEP if necessary.
Enterprise means only that the security option is one that a company, not a residence, would use.
While youre at it, shut down WPS on any router; WPS means WiFi Protected Setup.
Not all of the routers provide this feature, depending on their age.
Those that do have this feature may not have this box checked as a default setting.
Just go to the firmware section and turn it on.
In any case, the inevitable question will be: Whats your WiFi password?
You’ve probably given your password without even a second thought.
But do you know if your friends' devices are free of malware and other bugs?
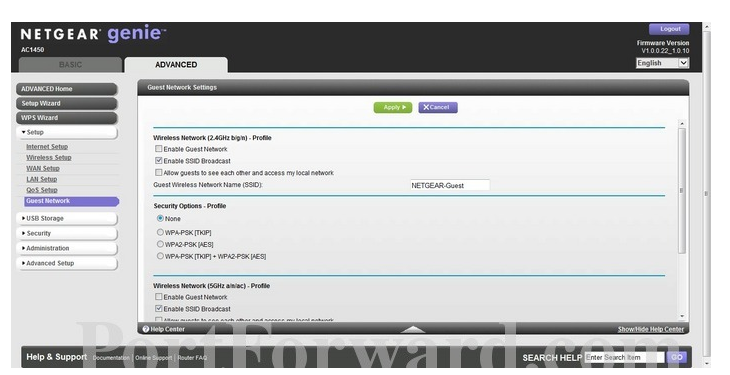
Fortunately, most routers offer guest networks that you might isolate from your regular home connection.
Not all the tabs are displayed.
If you scrolled down, youd find the one for creating your guest data pipe name.
The tab for Parental Controls will also likely be on your Home page, under Basic.

you could see that the status box for Parental Controls is not enabled.
The Parental Control status icon will now indicate enabled”.
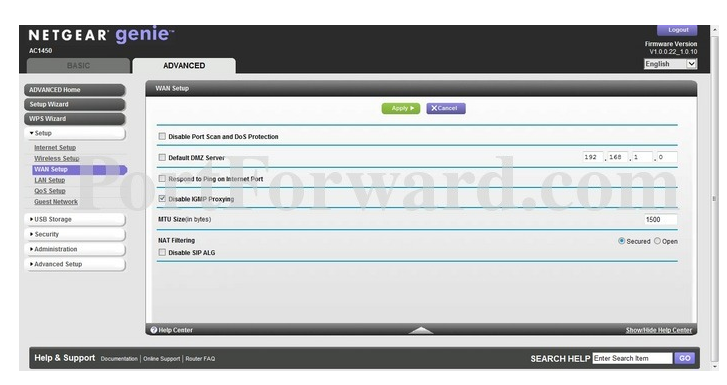
Ping is a component of the Internet Control Message Protocol (ICMP).

It consists of several error codes.
However, Ping is not an error - Its basic function is merely to indicatewhether a server is online.
Ping consists of two codes - echo request and echo reply.

Some users apply Ping to test their connection speed.
The Ping function resides in the Wide Area data pipe (WAN) interface of a router.
Look intothe following private browsers for better, more secure browsing.

You may also consider the option of proxy servers.
A proxy server acts as a clandestine portal between your rig and various websites.
It further encrypts data inquiries and transmissions.

However, this alternative possesses fewer supplementary security features and necessitates some technical proficiency.
Therefore, many experts insist that you purchase your own router for better security.
Most of the routers that ISPs rent to you are not top of the line models.

Some experts suggest that you choose a commercial-grade router that small businesses would use.
hey, comment on how to improve this article.







