Can hacking ever be a good thing?
What is ethical hacking and how is it different from other kinds of hacking?
How can you be an ethical hacker and why would a company willingly say yes to being hacked?

What is Hacking?
The impact of malicious hacking can be very powerful.
Cybercrime is projected tocost nearly $100 trillionbetween 2018 and 2029.
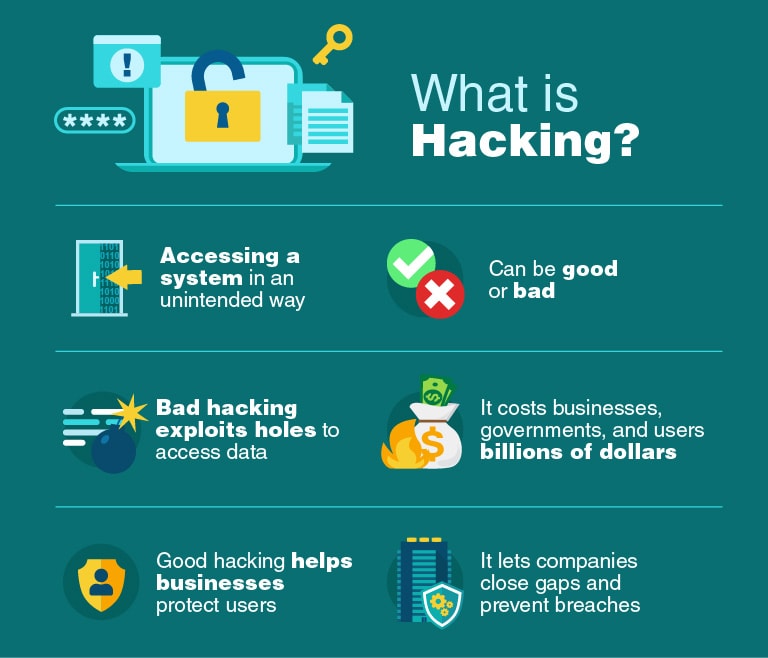
Given these statistics, its no wonder that the word hacking makes many people nervous.
What is Ethical Hacking?
Sounds like any other kind of hacking, right?

A black hat hacker uses hacking skills to exploit weaknesses for personal gain.
An ethical hacker only starts hacking after receiving explicit permission from the owner.
Consider the following examples.

They avoid detection by sneaking in at the perfect time while the security guards are changing shifts.
The group manages to steal several rare and expensive paintings and get away without being caught.
They make a large amount of money by selling the paintings on the black market.

Its pretty obvious that this scenario describes illegal and malicious activities.
Example 2: White Hat Hackers
A museum wants to know how well its security systems function.
The museum director hires a security expert to help detect vulnerabilities in the system.

The security expert will recreate a real-life scenario by trying to break into the museum.
The security expert and the museum director both sign a written agreement.
We call these people gray hat hackers.

The security expert writes a letter to the museum director but receives no response.
The security expert is worried that valuable paintings will be stolen if the museums security isnt improved soon.
To prove his point, the security expert disables the museums security alarm and sneaks into the museum.
The security expert doesnt break or harm anything.
There are a wide range of hacking tools and techniques that are commonly used by white hat hackers.
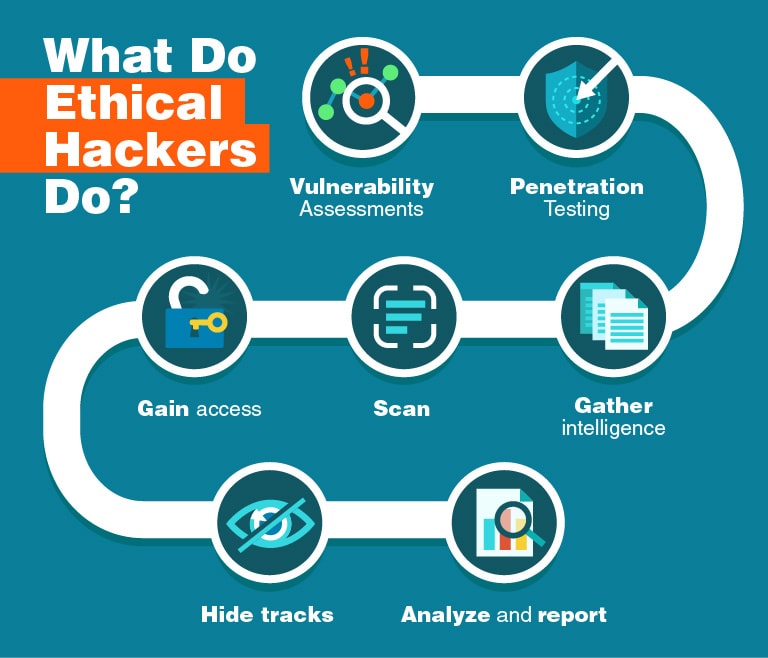
Vulnerability assessments, penetration testing, and red teaming are three terms that are often confused with one another.
They actually represent three completely different approaches that ethical hackers can take.
We will discuss them in more detail below.
Each one of these domains can take years to master, and like the cyber world is constantly evolving.

No software is perfect, and with every update or new release there are bound to be some bugs.
Because of this, most reputable software and hardware development companies recognize the value of frequent vulnerability assessments.
If a software vulnerability isnt quickly addressed and dealt with, the consequences can be catastrophic.
In a VA approach, the client and the ethical hacker usually work closely together throughout the entire process.
Another way to find vulnerabilities is by analyzing the source code.
A popular way to find vulnerabilities is via a technique called fuzzing.
Penetration testing is what most people think of when they picture an ethical hacker.
The ethical hacker has to get into the mindset of a black hat hacker and simulate a real-world attack.
This information will help you design and execute your attacks in the subsequent phases.
Good intelligence gathering enables you to determine what entry points and potential weaknesses exist in a system.
Entry points can be physical (e.g.
service door), electronic (e.g.
login prompt), or human (e.g.
John M. the receptionist).
This involves misleading or manipulating people, typically employees of the company, to infiltrate the environment.
Red Teaming
Red teaming is similar to a standard penetration test, with a few important differences.
A red team tries torecreate a real-world invasionas much as possible.
The test often takes place over a longer period of time than other methods.
Red teams usually use a combination ofsoftware tools, social engineering techniques, and exploits of the physical environment.
This leaves the company at a constant disadvantage.
Imagine that an IT company is designing new software for the market.

They are on a tight schedule, but skipping security testing could have serious consequences in the future.
What Do Clients Look For in an Ethical Hacker?
It is a role that comes with a lot of responsibility.

Ethical hackers have a responsibility tofully inform the companyof everything that they discover during testing.
Is Ethical Hacking Legal?
Ethical hacking can be a legal gray area.

In some jurisdictions, laws on ethical hacking are ambiguous, unclear, and dont cover all possible scenarios.
In others, ethical hackers have to stay within strict legal frameworks that outline whats acceptable and what isnt.
Both hackers and companies must take steps to protect themselves and confirm no laws are broken.

One of the main differences between legal and illegal hacking is whether the hacking was authorized or unauthorized.
Organizations may be breaking the law byasking hackers to access confidential customer datawithout getting customers permission.
Okay, so a written agreement is great and all.

But what about situations that arent so black and white?
While doing so, sheunintentionally gains accessto the websites confidential database.
Unfortunately, there have been multiple real-world examples of this very scenario.

Even though the hackers intentions were good, the law doesnt always take intentions into consideration.
Things get complicated when you consider the fact that not all ethical hackers are directly hired by a company.
Instead, some white hats act as vigilantes.

They spend their time trying to find and report security flaws that companies have failed to fix themselves.
They often have noble intentions, with their main goal being to make the world a more secure place.
In legal terms, this is sometimes calledgood faith hacking.

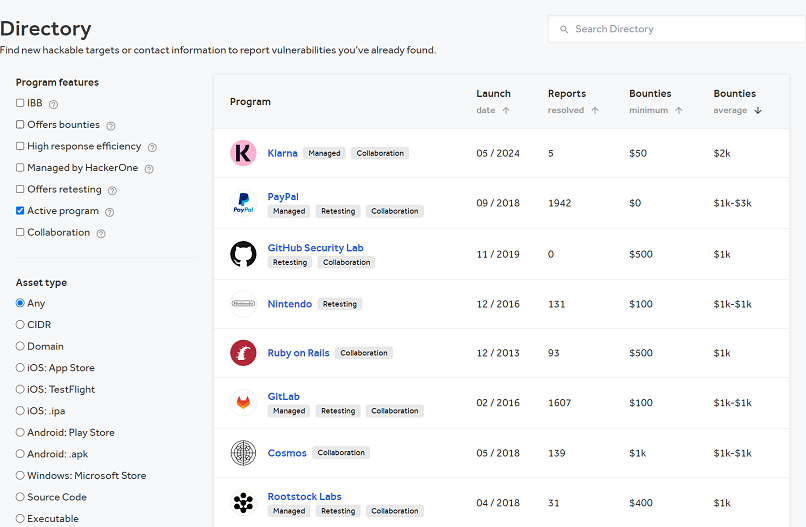
Bug bounty programs and vulnerability disclosure programs (VDPs) can offer somelegal protectionto ethical hackers.
Typically, bug bounty programs are explicitly defined and outlined by the company to the public in writing.
Vulnerability disclosure programs(VDPs) are similar to bug bounties, but dont offer financial incentives.
They create a secure channel for white hat hackers and security researchers to report vulnerabilities discovered in good faith.
These examples help explain how ethical hacking can be legal or not depending on the circumstances and context.
His research sometimesforced him to access personal informationfrom account holders with compromised systems.
Dittrich frequently speaks about how his hacking activities could have landed him in serious legal trouble.
Even though his intentions were good,some of his actions could have been viewed as unauthorized intrusions.
The researcher tried to betransparent and communicativewith all of the DDoS attack victims involved in his research.
He also informed government authorities of his activities and all of his research findings.
Dittrich is now a big advocate of ethical hacking to combat malicious hacking tools.
In 2011, Mangham noticed some security vulnerabilities in the Yahoo!
Using hacking techniques, the software development student explored the vulnerabilities in more detail.
He put together a report on his activities and findings, which he then sent to Yahoo!
along with recommendations for how to improve the security.
However, Manghams luck changed later that year when he tried the same routine with Facebook.
Encouraged by his previous success, this time he took more extreme actions on his hunt to find vulnerabilities.
He claims that he was trying to put together a report similar to the one he created for Yahoo!
so that help Facebook improve their security.
Unfortunately, Facebook saw things differently.
A growing number of companies around the world are realizing the importance of investing heavily in cybersecurity.
This rising awareness means that the field of information security is growing faster than ever.
Many ethical hackers are hired by businesses or consulting firms.
These hackers usually make their money through bug bounties.
The legal protections for bug bounty programs are discussed in more detail earlier in this article.
Bug bounties can be a great way for talented ethical hackers to earn money.
There is no single correct way to become a great hacker.
In fact, some of the most famous ethical hackers have beencompletely self-taught.
Keep in mind that no one becomes a talented hacker overnight.
Learning hacking skills takestime, effort, and dedication.
Even experienced hackers need to constantly learn new skills because technology changes so rapidly.
Any degree that involves learningprogramming languages and software developmentwill be the most relevant for ethical hackers.
There are a few different credentials that ethical hackers can get.
The CEH is anentry-level certification.
The exam lasts aboutfour hours.
This is anintermediate-level certification.
To pass the OSCP you willperform a penetration test against a live simulatednetwork with vulnerable devices.
You’ll be hacking in conditions that mimic reality.
This is anadvanced certification, but obtaining it proves that you’re an outstanding ethical hacker.
There are many excellentfree online resourcesfor both beginner and advanced hackers to improve their programming skills.
Here are a few examples:
Programming Resources
Codecademyis an interactive site that is great for beginners.
You get to learn the basics of different programming languages in a practical way.
Codewarsis a fun, interactive way to learn basic and intermediate coding in several popular programming languages.
Free Code Campadvertises itself as a coding bootcamp.
It teaches how to write professional reports on vulnerabilities for bug bounty programs.
Hacksplainingis a fun, interactive site that teaches lessons on different hacking techniques.
yeahhuboffers security ebooks available for free on GitHub.
They cover everything from Hacking for Dummies to Advanced Penetration Testing.
EnigmaGroupis a resource for potential ethical hackers to develop their penetration testing skills.
