I am the CEO of Teramind, which I founded in 2014.
At Teramind we develop state-of-the-art applications for user behavior analysis, insider threat prevention, and session recording.
What are some examples of insider threats?

Insider threats come from employees through malicious activity or just negligence.
Not every threat is a user who is evil or has bad intentions.
For instance,a person with legitimate access may inadvertently respond to a phishing email and expose their credentials.
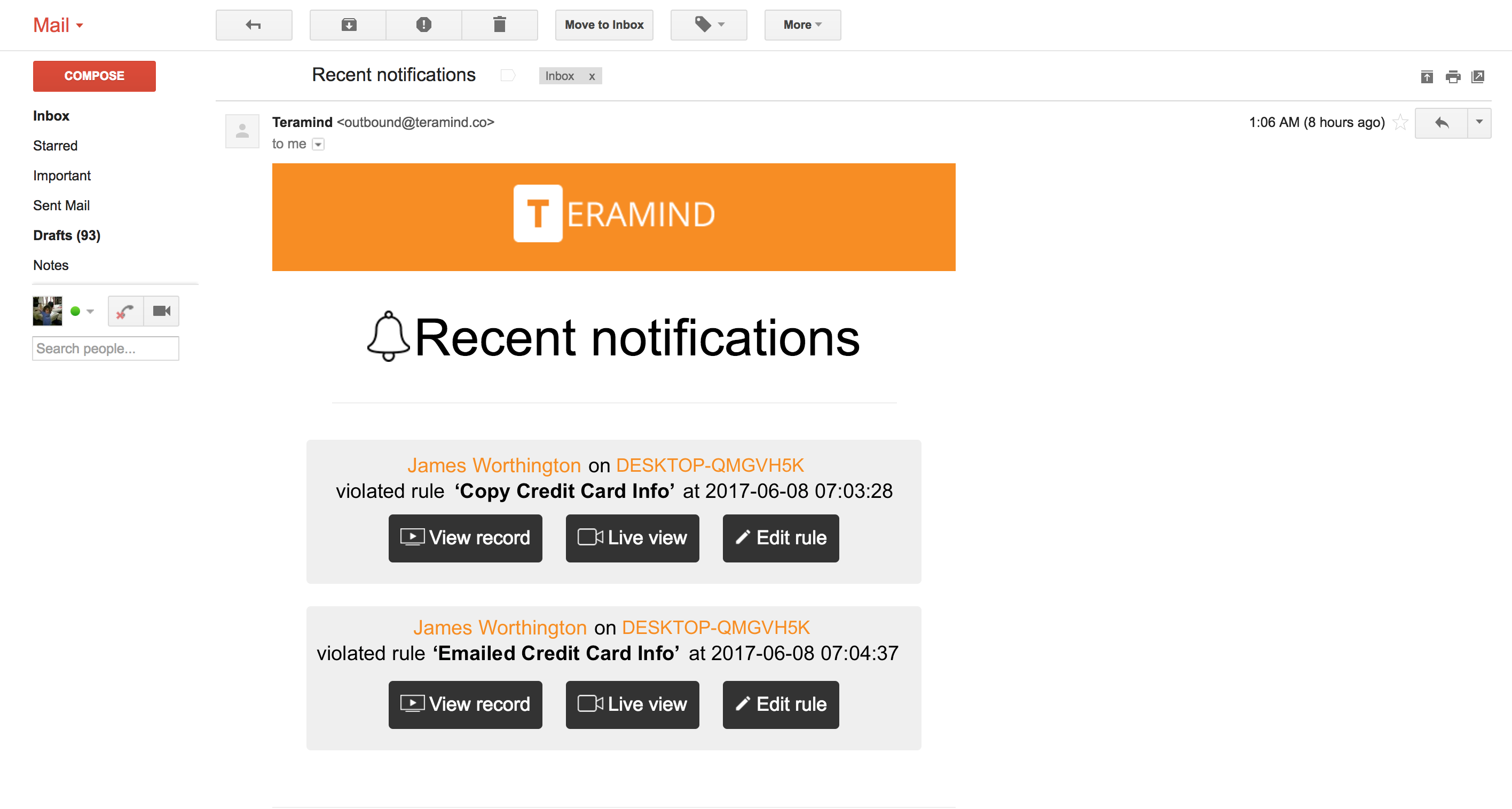
We had an interesting case with a company that was concerned about the radicalization of their employees.
How does Teramind monitor and react to employee activity that is deemed threatening?
Teramind is one of the most complete tools for monitoring employee behavior in the sense that it monitors everything.

Another example would be health records, which today are worth more than financial records.
In addition,by learning the baseline of a user or group we can detect anomalies.
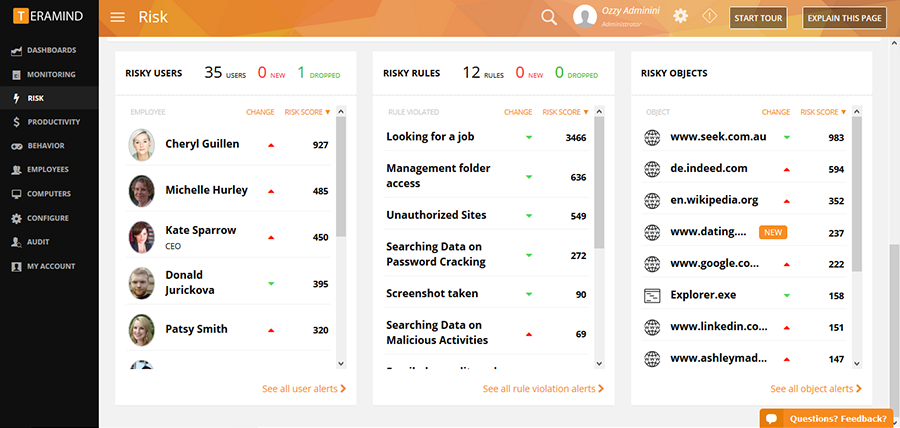
Can an organization set rules within Teramind as to which employees to monitor?

It can, but that may be overmining.
We find thatwhen you generalize a bit, you get more quality alerts and less false positives.
Can Teramind be used to monitor employees or freelancers who work off-site?
How does Teramind respond when it detects rule violations?
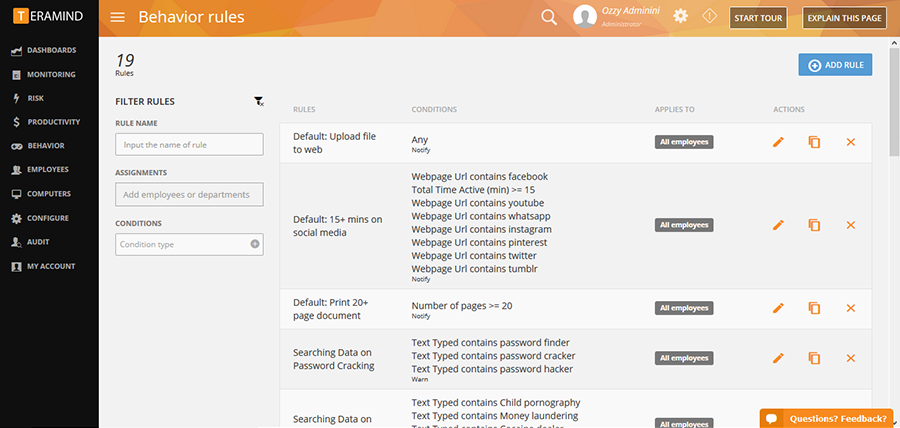
It is up to each company how they configure the rules to best suit their concerns.
making it a user education thing.
you could also choose an action that will close an tool after a certain amount of time.
Depending on the rule,it’s possible for you to also redirect users.
it’s possible for you to even kick a user out completely lock them out of their workstation.
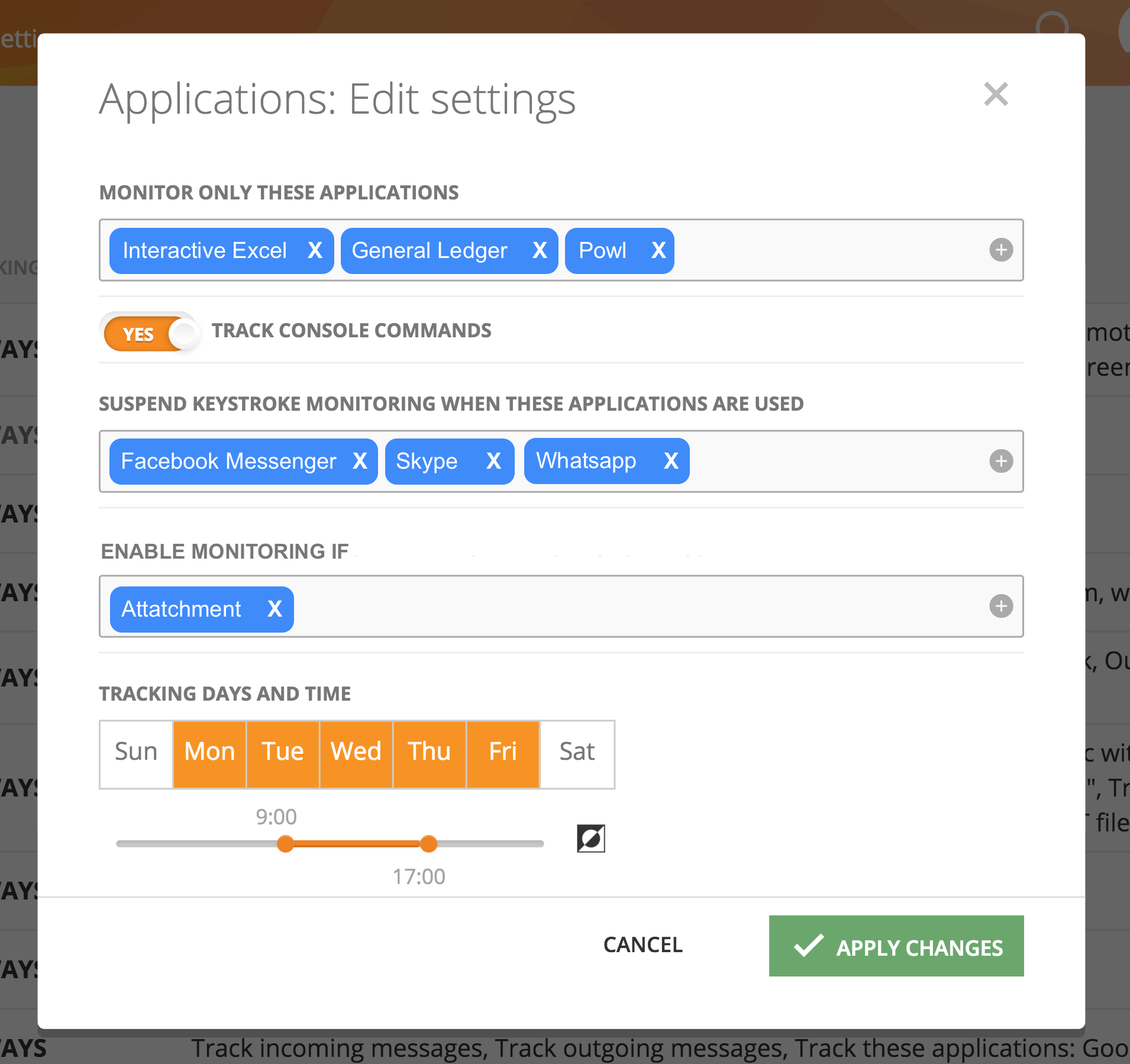
So, the actions really depend on the context and the rules that each company sets.
Is user activity and behavior constantly being captured?
In fact, some clients use us for compliance.
Lets take, for example, the case of a clerk who looks at sensitive data all day.
So, we fill that gap as well.
So yes, it is constantly recording, but it is constantly overwriting except for that 5-minute buffer.
Thats what makes Termamindproactive, and not just reactive.
How does Teramind calculate “productivity”?
you might also automatically assign tasks to qualify what the user is doing.
like, comment on how to improve this article.





