Your Risks as a Teacher
Your students are more tech-savvy than you might possibly imagine.
it’s crucial that you know how to protect both yourself and your students from cyber attacks.
They may not be savvy enough to spot every cybersecurity risk that they encounter.

After all, knowledge is power.
In this section, well describe these hazards and explain how you might avoid them.
They probably know how to use every feature of the most popular online programs and digital devices.

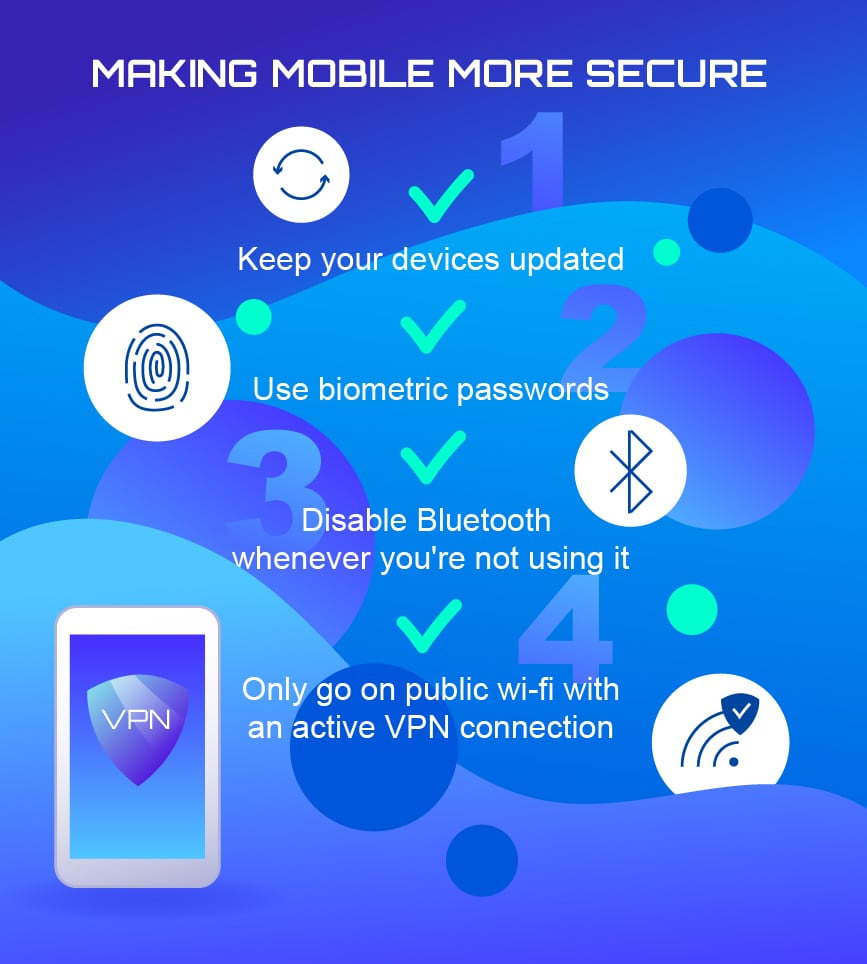
An infographic on making mobile more secure.
This could give them an enormous advantage over you if they wanted tohack into your accounts.
Your first instinct might be to completelyban digital devices in your classroom.
Fighting digital devices in the classroom will most likely be futile and frustrating.

An infographic on making mobile more secure.
Whos Using Your User Accounts?
As a teacher, you probably have numerous online accounts.
Now,imagine if your students had access to all the information stored on those accounts.

Hacking into your accounts probably isnt very challenging for your students.
Below, we provide our suggestions forkeeping your user accounts secure.
This advice applies to your online teacher portals, personal accounts, emails, and social media platforms.
We recommend that you:
This should help keep your accounts safe from students and other potential hackers.
You may even use a mobile unit to assign and grade homework or conduct research for your class.
Smartphones are incredibly convenient and useful, but theyre also very vulnerable to student hacking.
Your smartphone may be expensive, but the data stored on it is even more valuable.
They can also protect you from other potential hackers anywhere else you take your smartphone or tablet.
magazine, privacy matters more to Generation Z.

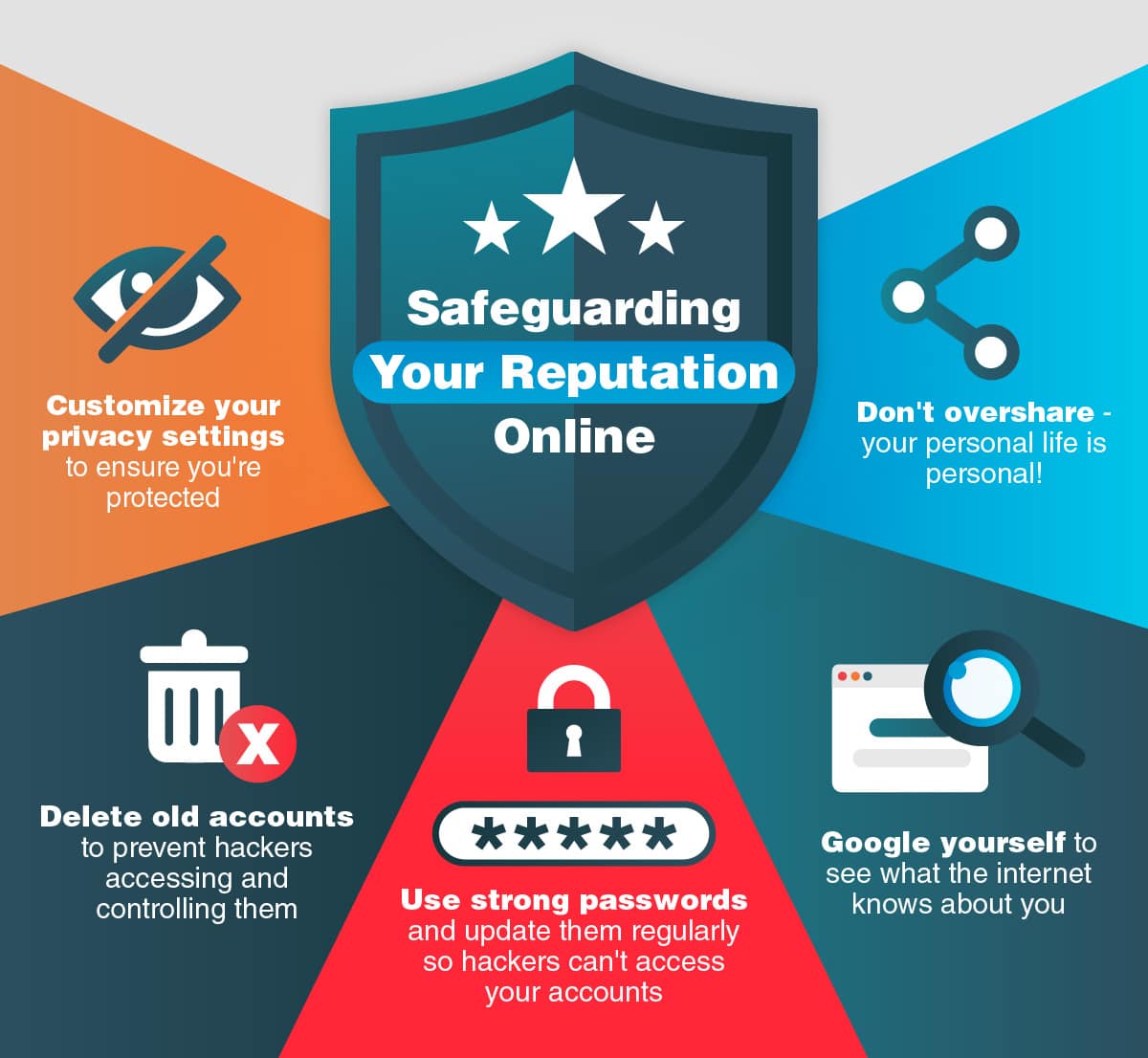
As their teacher, you need tobe careful about what your students can find out about you online.
Its important that youremain a trusted, respected figurein their lives.
Many teachers are tempted to delete all their online information, but thats not necessary.
Below, we explain how.
Is Your School web link Safe?
Your school web connection is probably the primary way you and your students reach the internet.
It can also be a good way to block certain unsafe or inappropriate sites and improve your schools cybersecurity.
Unfortunately, it could also bevulnerable to breaches, which could put you and your students at risk.
These tools could allow them to unblock websites and load inappropriate online content while theyre in your classroom.
This could be dangerous and disruptive.
you’re free to alsobe on the lookout for unsuitable online contentstudents might bring into your classroom.
This could leave you, your students, and school administrators susceptible to malicious attacks.

Clearly, both you and your students face cybersecurity risks if your school web link is unsecured.
We recommend adding a password to your schools wi-fiand changing it every three months.
Unfortunately,cyberbullying is epidemic in many schools.
The study found that 90% of teens believe online harassment is a problem that affects people their age.
As you might assume,cyberbullying can have a devastating long-term impact on children and adolescents.
Like other forms of bullying, it can lead to real-world consequences that affect a victims whole life.
Kids may experiencedepression, anxiety, and low self-esteemas a result.
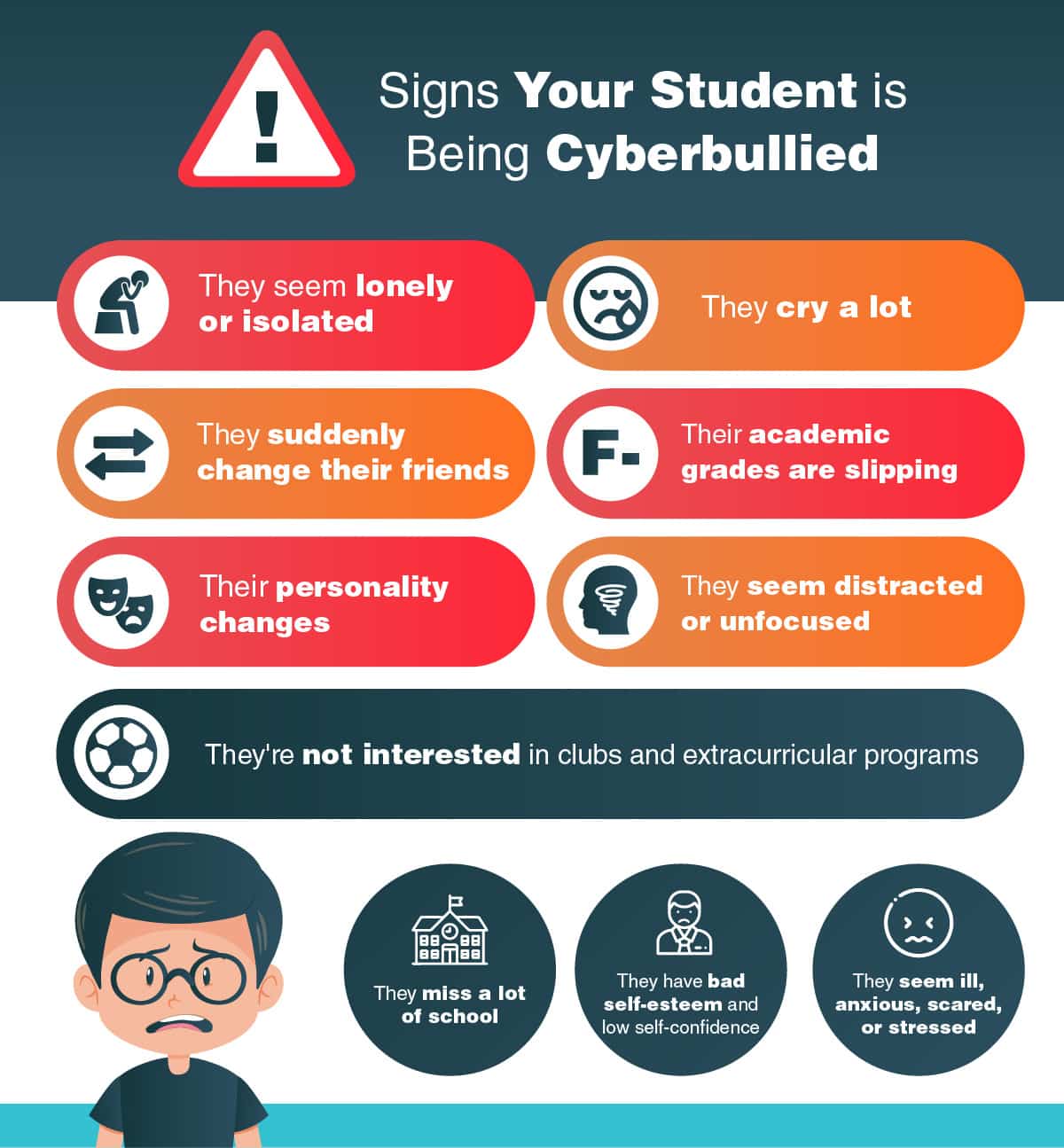
As a teacher,you may be an adult onlooker when it comes to cyberbullying.
Children and teenagers who are cyberbullied often exhibitsigns of general bullying or distress.
The earlier you might intervene and stop this harmful behavior, the better.
An Educational Solution
One of the best ways to prevent cyberbullying is to teach students about it.
See our tips and lesson plans for instructing your class about cyberbullying.
Your students are generally tech-savvy, but they may not understand thedangers of the internet.
We highlight a few other things your students need to know about cybersecurity below.
However,you also need to teach them about the dangers of public wi-fi outside of school.
Although it can be convenient,there aremany reasons to avoid public wi-fi.
These include malware, worms, unencrypted websites, and more.
Fortunately, you’re free to help teach your students how to combat these risks.
Fighting Phishing
Your students devices are filled with valuable information.
This could include private photos, credit card information, personal messages, bank data, and more.
Additionally, some hackers, cybercriminals, and cyberbullies simply want to mess with victims lives and cause chaos.

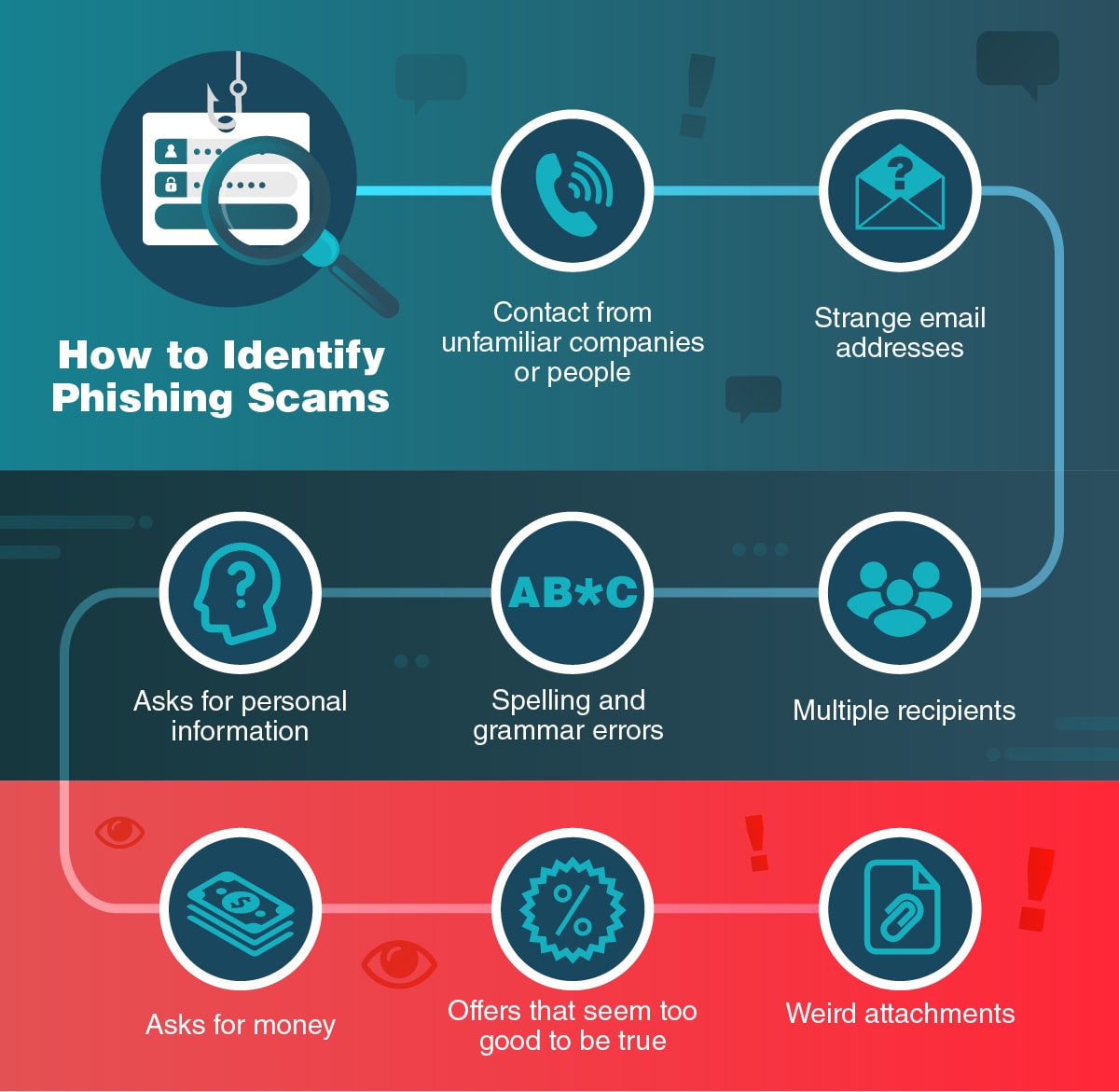
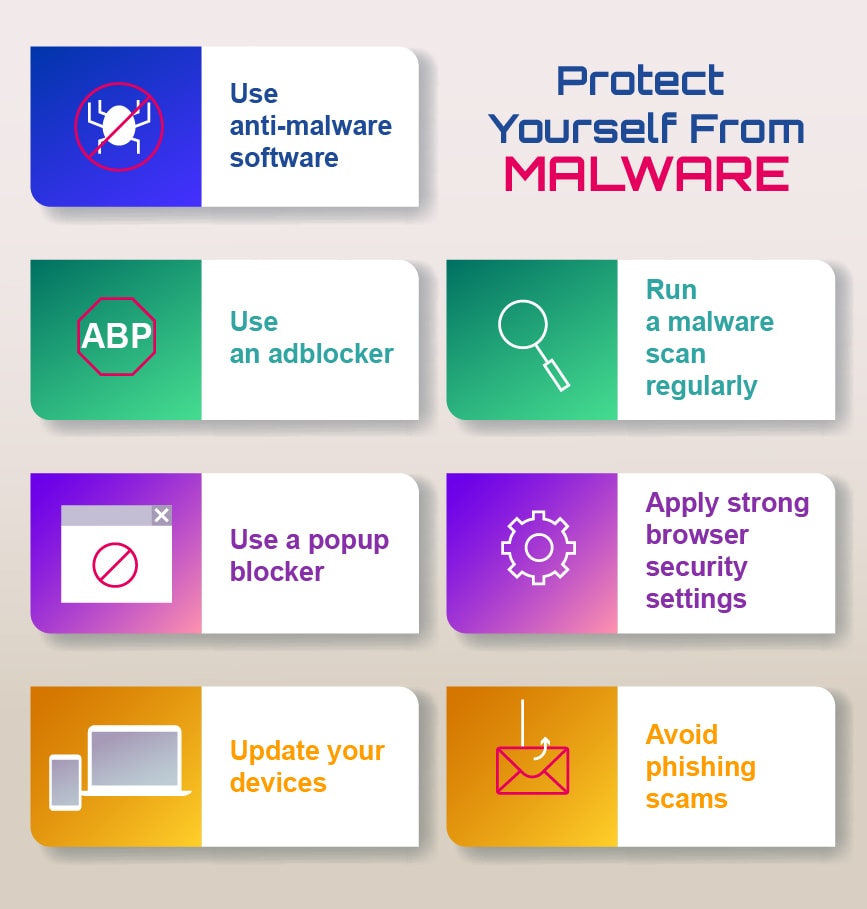
Knowing more about how phishing and malware work can help you and your students identify and avoid them.
These websites may alsoinfect devices with malware(which we explain below).
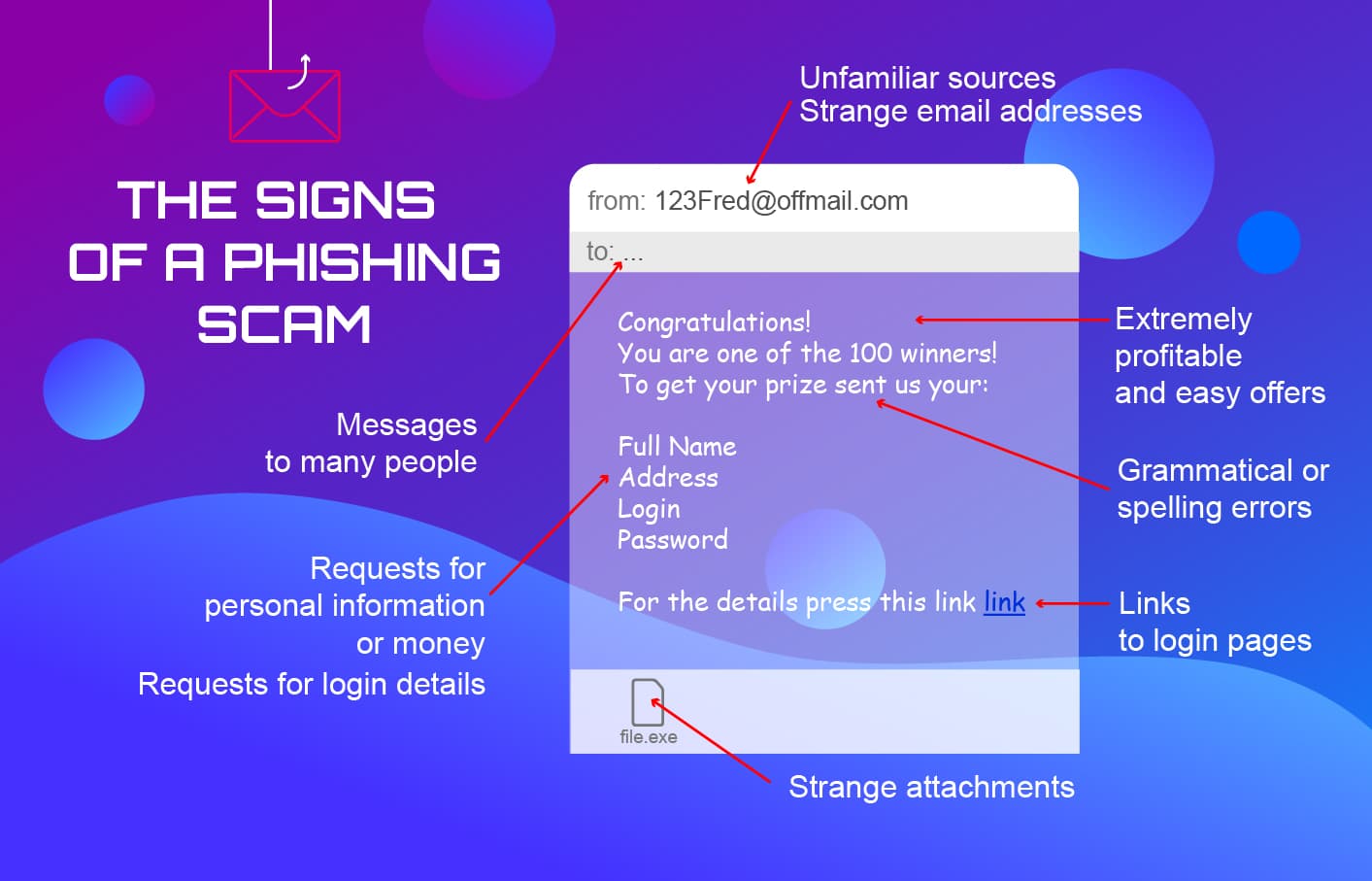
To protect your students, you could teach them to identify the signs of a phishing scam.

Students shouldonly open email attachments if they are truly sure the message is authentic and safe.
Since anyone can be phished, you should also educate your fellow teachers and administrators about phishing.
Malware candestroy a equipment or make it extremely difficult to use.

It can also steal private or critical data users need to access.
Malware may also cause a gear to run very slowly or poorly.
Malware can be included with seemingly trustworthy applications.

For these reasons,users should always research and understand exactly what theyre putting on their devices.
AsMicrosoft Windows Security Supportpoints out, infected removable drives could also be to blame for malware.
The malware can be automatically installed when you connect the infected drive to your PC.

Some worms can also spread by infecting PCs connected to the same internet.
Students should never use a drive or connection they cant completely trust.
Pirating software, music, or movies may also make a unit susceptible to malware,according toComputer Hope.

This dynamic can make the consequences of malware exponentially worse.
However,internet-enabled tools can also be dangerous.
Many cybersecurity risks that affect normal internet-enabled devices can impact the Internet of Things.

They hadpoor security and couldnt effectively protect their users data, especially since they had no password strength rules.
Some teens seem to know instinctively thatposting personal data online could hurt their reputations.
Explain to your students thatsharing their location and activities in real time on social media can create cybersecurity problems.

A cyberstalker might also use location information to track down a student and harass them.
This process is called geotagging, asyour equipment labels your location on the image.
This process is called geolocation.

Google, Yelp, and other applications also use geolocation to tell exactly where students are.
These apps can potentially share that information with others.
Later in this guide, we describe various techniques you might use to teach your students about cybersecurity.
What begins as an anonymous online connection can turn into something much more dangerousin person.
Furthermore, cyberbullies might use these platforms to harass, shame, or embarrass young people.
AsHealthfullyputs it, chat rooms are a place where bullies can have free reign over potential victimswhile enjoying anonymity.
In addition, unfortunately,anonymous users may also use chat rooms…to post links to pornography.
Your students may choose a link and be taken to an offensive site, either intentionally or by mistake.
Well provide further advice about teaching your students about cybersecurity in the next section.
How to Begin
We recommend that youbegin with an online safety quizto test your students knowledge.
Talking about this is important becausestudents who struggle with cyberbullying may not open up about it on their own.
Next,show students the consequences of cyberbullyingso they fully understand how serious it is.
You might also ask students to imagine how they would feel if someone harassed them online.
Often, students do not see how harmful teasing, shaming, or insulting a classmate online can be.
However, if they do,following these steps can help minimize the damage of this harmful online activity.
These types of online platforms are widely used and very vulnerable to cybersecurity issues.
Sample Lesson Plan: Go Phish
Below, weve included asample cybersecurity lesson plan on phishing.
You may use this as a modelfor planning your classes.
Sincerely,Netflix Customer Service
Ask them why they would or wouldnt respond to this email.
Describe how phishing scammers use these emails to collect personal information.
Tell them to send their phishing emails to you so you might choose the best, most convincing one.
Share the winner with the class and explain why it is a good example of a phishing email.
Phishing Homework
For homework,have students write a five-step plan for avoiding phishing attacks.
you’re free to search online for similar opportunities in your local area.
yo, comment on how to improve this article.
