We were fortunate to receive contracts from BSI and ISO.
What can you tell us about your product, Ascema?
The partnership between Jaguar Land Rover and the University of Surrey gave rise to Ascema.
So, we created a collaboration between the three parties.
That’s how Ascema was born.
Since then, we have developed and patented new algorithms.
Thats unstructured content which actually needs protecting within systems.
In particular, we were looking at how to enable cloud adoption by de-risking it.
How doesAscemawork?

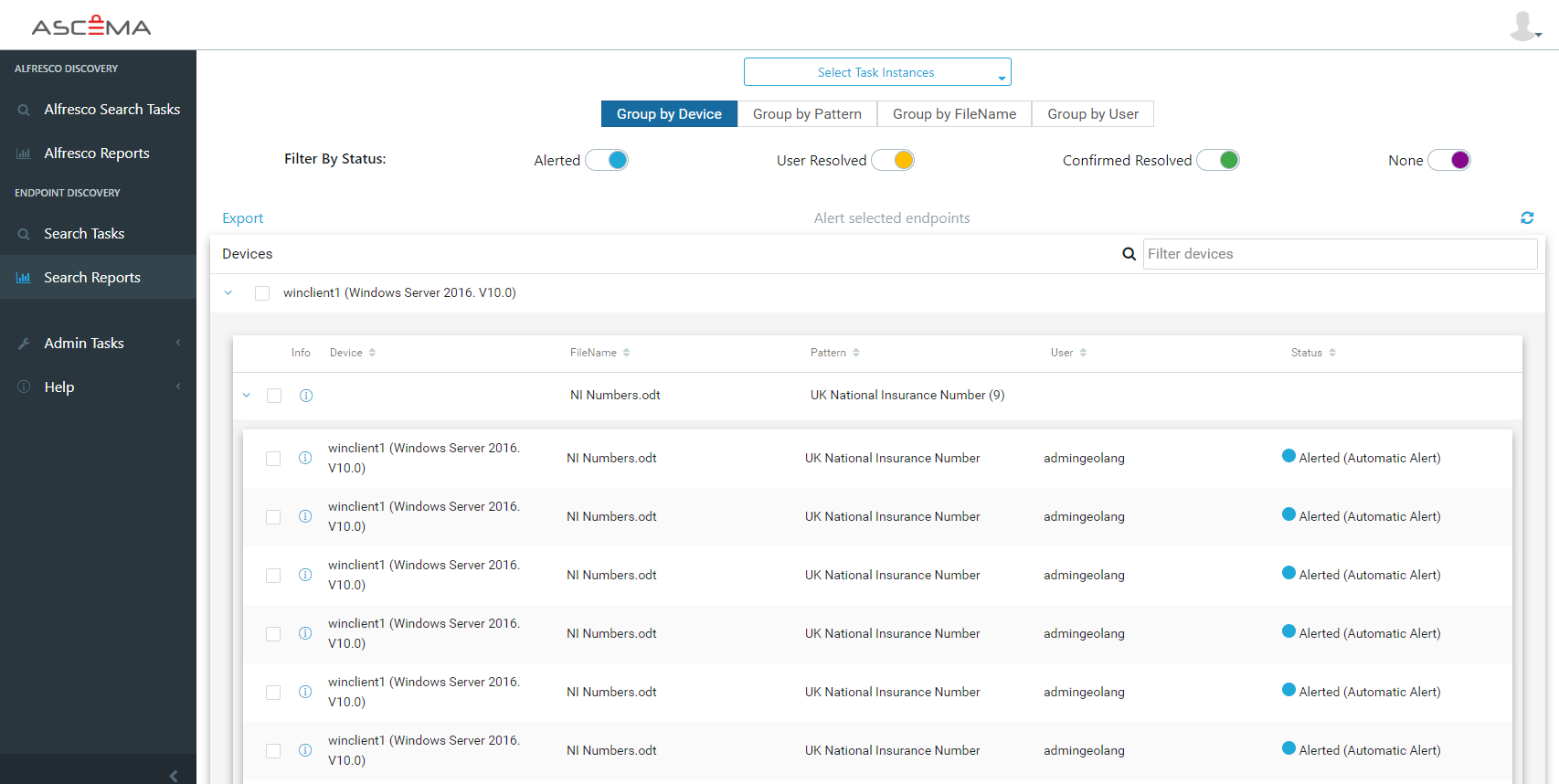
In addition we have developed data discovery solutions for endpoints and server.
The premise for this was looking at enterprise data and looking at the risks to that data.
Can you describe the profile of an insider threat?

But thats not what insider threat is all about.
Insider threat may be categorized as three distinct actors.
What happens once Ascema is activated?
Depending on what you wish to do, its generally a 3-step process.
Organizations such as Jaguar Land Rover, follow template processes which often hold sensitive data.
Again, a 3-step process.
All that happens in real time.
How do you balance the conflict between security and ease of use?
It doesnt affect ease of use because it is an API integration with no latency whatsoever.
The end user will be guided in appropriate behavior.
If they are behaving appropriately, they will not see anything.
The system also educates end users on data protection policies for the various data and different types of documents.
This is what I term generally as after the horse has bolted technology.
But within that reporting, we offer contextualization, which is what our competitors dont do.
We give the event in context and give a little bit of the content around it.
In April 2018 we were acquired by the Shearwater Group PLC who are supporting our scale up plans.
kindly, comment on how to improve this article.

