Secure Channel uses real-time encryption to protect data, rendering it useless to unauthorized access.
My main goal is to encourage our company toembrace change and innovation that will lead to disruptive technology breakthroughs.
Our patented breakthrough products meet these needs for a wide range of small and midsize businesses.
It represents a significant enhancement over AES-256, and is offered within our ParaDoxBoxTM and Superencipherment Engine solutions.
XOTICTM is our state-of-the-art streaming cipher protocol that is considerably more flexible and faster than any other available protocol.
Itenables in-flight streaming encipherment on any bang out of data, in real-time.
XOTIC Encipherment strength can be dialed-up or dialed-back depending on the use case.
This question is a classic cryptography problem.
Its why the Germans Enigma code failed in World War II, and why we cant use one-time password.

Our ParaDoxBox solution explicitly addresses the core problem of key distribution by safely moving information around among multiple stakeholders.
What are social engineering attacks and how does ParaDoxBoxTM eliminate them?
Not to mention the data thats flowing over the airports public Wi-Fi.

Thats the access point, the willingness of people to offer up such information.
Our solution ParaDoxBox looks to improve any software thats vulnerable to social engineering attacks.
So, they essentially only get a small piece of the access puzzle.
How do you mitigate the security risks to your clients Internet of Things (IoT)?
What are the vulnerabilities associated with password-based authentication?
What more secure method(s) do your products use?

Password-based authentication is generally fully exploitable.Single-factor authentication can no longer hold up to todays sophisticated attacks.
The problem is not the passwords complexity, but the length.
Even password with a mix of symbols, upper and lower, etc., are just not long enough.
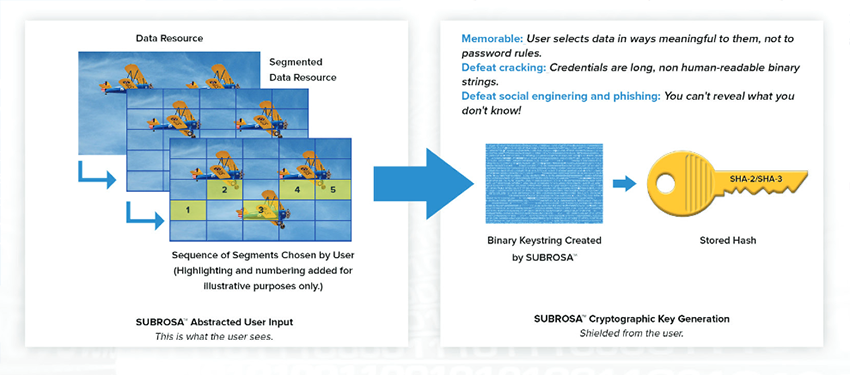
Its very easy for the user, as they create a personal interaction pattern that generates keys securely.
HITECH pertains to the security issues related to the transfer of health data like medical records.
ParaDoxBox encrypts data while the user is active, and the machine is operating.
It isnt disruptive at all to the individuals workflow and provides very impactful protection.
The principal concern is the theft or unauthorized viewing of pre-release content.
Its not visible to humans, but is trackable through forensics.
c’mon, comment on how to improve this article.




