How can we characterise Cybersecurity?
How do data breaches, hacks, system exploits and computer intrusions happen - and why?
What pops up if Cybersecurity really works effectively, and can we systemise it?

Or will the clever hacker always break into any networked unit, sweeping all defences aside?
The upshot is a wholly original, astute and fearlessly honest - yet practically oriented - treatise on Cybersecurity.
Further volumes are planned for which Alan intends to collaborate with other authors.
Science of Cybersecurityis on Amazonhere.
Below is the first chapter of the book, brought here exclusively for vpnMentor readers.
In sum, this book is a characterisation of said axioms.

We begin with a simple questionwhat is security in-and-of-itselfand especially in terms of digital information sharing?
social accessibility (or privacy) status) [Axiom 2].
A communication system is a system or facility for transferring datum(s)/patterns-of-meaning between persons and equipment.

Prior to the widespread adoption of the Internet information assurance concerned reliable data storage/processing.
open-datums) and social networks whereby the information transfer is one-to-many, many-to-one or many-to-many (i.e.
Facebook / Twitter).
To access an item, we:
A.
Next we:B. Cybersecurity is a general term that can be used regardless of the form the data may take (e.g.
Our exposition defines (for the first time) a comprehensive set of cybersecuritydefinitionsand axiomatic first principles.
Let us now establish some logical truths.
Security= Protect accessibility status of item.
Access= Find, contact and/or know an item.
Posses= Find (see/locate) plus contact (reach/grasp/hold) an item.
it is access-controlled).
Hence the sender and receiver/viewer are the same person; and the system simply memorises the datum.
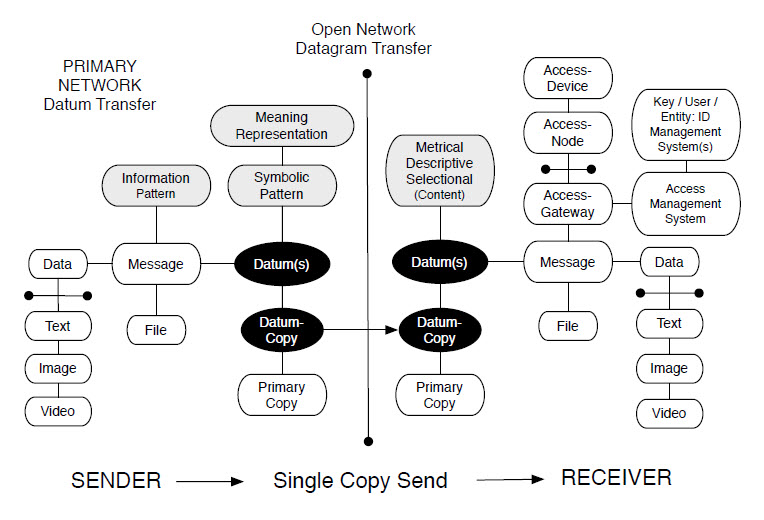
Single-Copy-Send
Communication of a datum (+ meta-data) with guaranteed social security.
Where are the copies?
Who can see, know and/or change a copy?
How long do copies hang around?
a transatlantic data pipe) [Axiom 11].
Strangely absent is any kind of top-level theory, and missing are fundamental definitions and/or first-principles etc.

Ergo, the system-designer’s job becomes one ofcollecting partial formalism(s)before somehow stitching them together.
The net result ispartial truth(s) and/or sub-optimal approachesor at least major difficulties.
Notes
1.
MacKay, Donald., Information, Mechanism and Meaning, The MIT Press,1969.2.
Gombrich, Ernst., Art and Illusion, 1960.3.
Radley, A., Self As Computer, 2015.4. c’mon, comment on how to improve this article.
