It was only a matter of time until that solution became a commodity.
What makes this new approach unique?
It’s a very narrow, closed parameter of things users are doing at work.

It’s as quick as an antivirus, with no latency.
The CDR process produces no false positives, because there’s no need for detection.
How does it work?
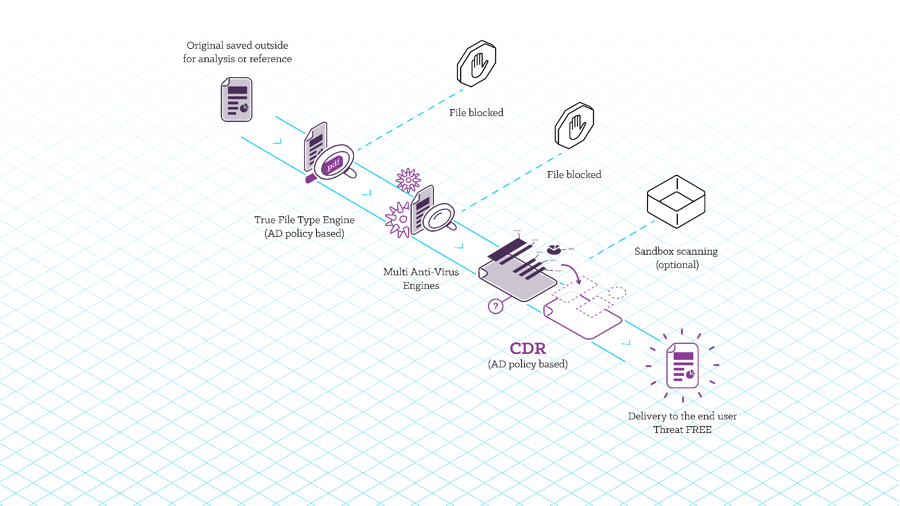
We integrate with active directory to allow policy management per groups.
These will be regenerated according to a set of rules determined by the organization.
Let’s say a PDF contains a url for example.

We are able to check and modify it, erase it or turn it into text.
This is a specific example of regeneration.
After that, the file is transferred to the user safely.

What happens when malicious content is identified?
CDR does not identify malicious content.
Rather, it clears elements which have the potential to be malicious.
It’s a prevention method that doesn’t rely on detection.
How easy is it to deploy ReSec, and does it integrate with existing systems?
ReSecure can also integrate with FTP or as a directory watcher.
Thousands of files can be transferred per hour.
Deployment can also be done to integrate with existing detection solutions like sandboxes.
This helps structure specific work flow in the way the organization decides.
Management is also relatively simple.
We define a set of rules and a group of users that the rules apply to.
Typically, we see four types of policies depending on the enterprise’s needs.
We integrate with SIEM systems, which generates all information for the monitoring tool.
Users can simply log into their dashboard and view information about traffic going by in real time.
Do you have any new features planned in the near future?
Using CDR in this fashion will allow us to create insights about the content being processed.
We currently have about 40+ enterprises using our solution.
What is your personal perspective on cyber security?

The cyber security market is thriving, with many vendors doing amazing things to battle the ever growing risks.
CISOs and IT managers need to constantly reevaluate the threat landscape and the organizations weaknesses.
My tip for those individuals is: Determine exactly what is it you’re looking for.
If you need a connection solution, how will you implement it?
What is your goal?
What are the powerful tools you will use to enable identification and more importantly, prevent the threats?
There are no silver bullets so be skeptical of those who have a go at sell you one.
kindly, comment on how to improve this article.
