Data Breach Summary
Company Profile
Fleek was launched in 2016 by developers Squid Inc.
But rare are these times.
Most often, we need days of investigation before we understand whats at stake or whos exposing the data.

We quickly identified Fleek as the party likely most responsible for the breach.
However, we always conduct a thorough investigation to confirm a database or S3 buckets owner.
Also, since the app was deleted from most online databases, we could not directly ping the developers.

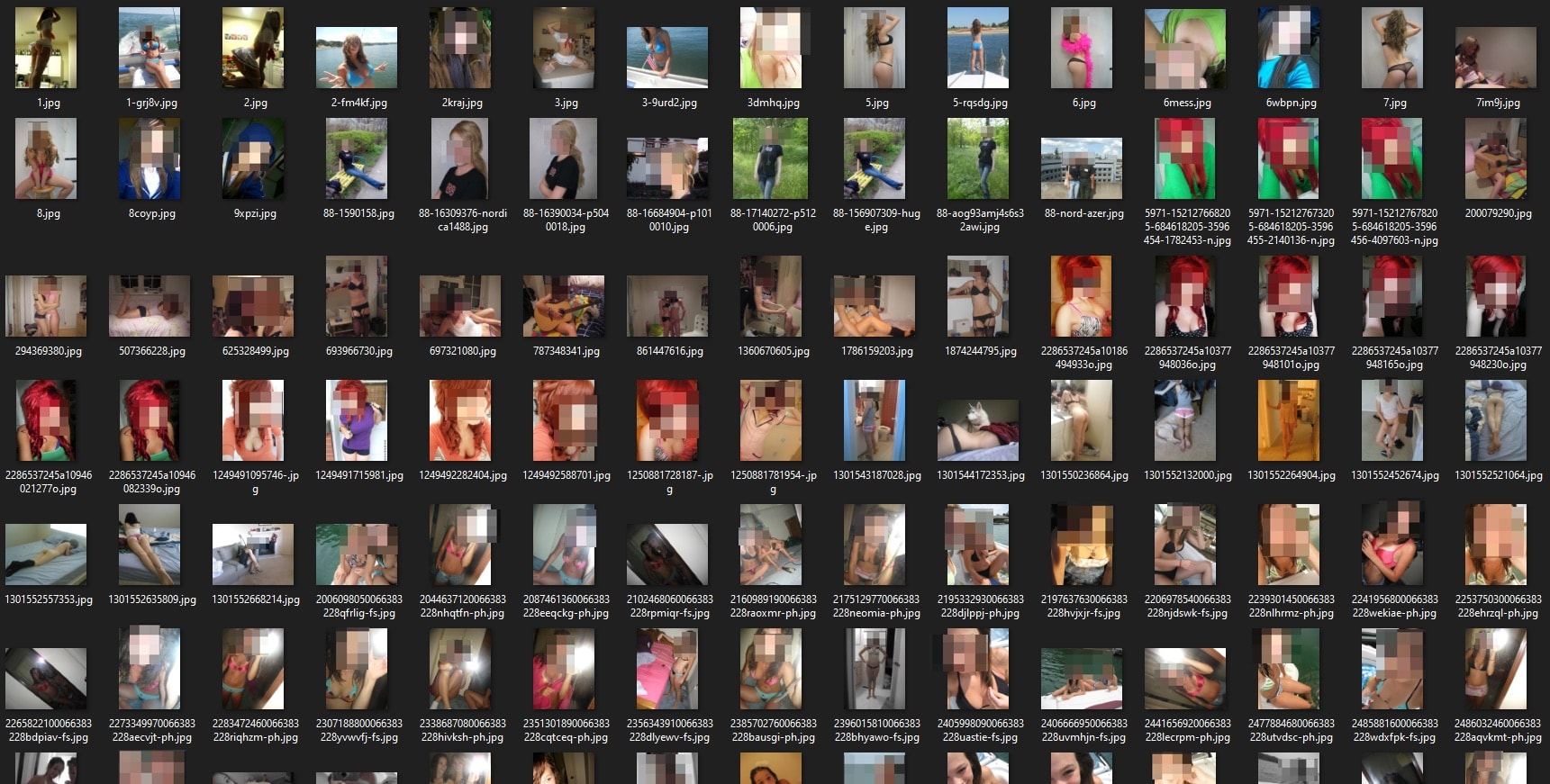
Fleek user account avatars
Eventually, we also found the contact details of Squid Incs founder and contacted them directly.
However, despite reaching out twice, we didnt receive a reply.
One week after we discovered Fleeks S3 bucket, it was secured.

Fleek user account avatars
Most of the data in the S3 bucket consisted of images uploaded by users, including their account avatars.
Many of these were sharedin folders given offensive and derogatory names like asianAss by the apps developers.
Unfortunately, most of the accounts were still fake.

In fact, it appears they’d been created by Fleek to trick users.
Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.

It shows you the many ways cybercriminals target internet users and the steps you might take to stay safe.
They examine each weakness for any data being exposed.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.

These ethics also mean we carry a responsibility to the public.
Fleek users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is tohelp make the internet safer for all users.

We never sell, store, or expose any information we encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
Help Us Protect The Internet!