The origins of the database and how the fraudsters were targeting Spotify are both unknown.
But rare are these times.
Most often, we need days of investigation before we understand whats at stake or whos leaking the data.

Some affected parties deny the facts, disregard our research, or play down its impact.
So, we need to be thorough andmake sure everything we find is correct and accurate.
This included:
There were also numerous server IP addresses exposed in the leak.
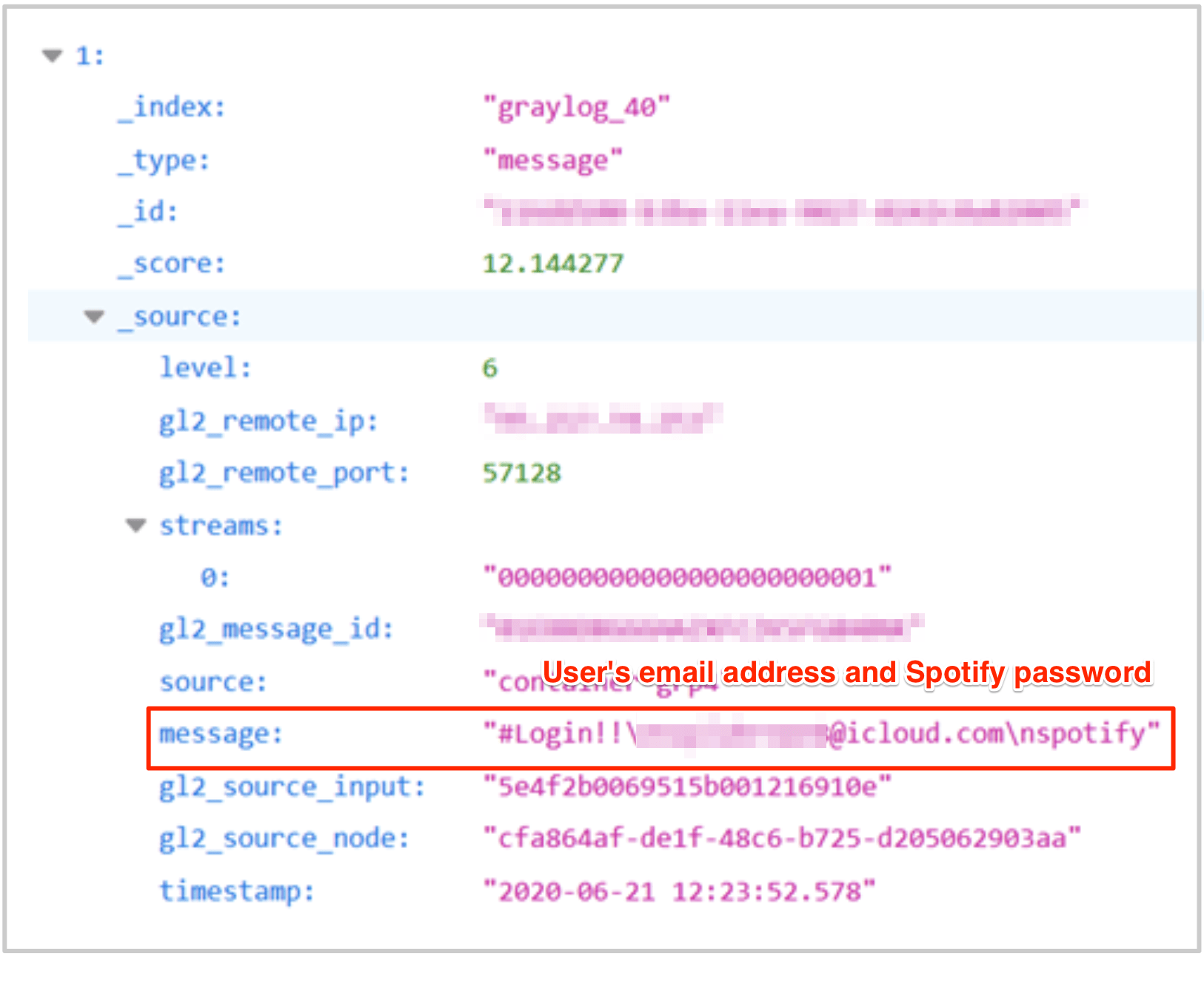
With this information,criminals could pursue several activities to defraud and hack Spotify users.
you’ve got the option to also use our password meter toensure your current passwords are strong enough.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.

It shows you the many ways cybercriminals target internet users and the steps you might take to stay safe.
Each discovered weakness is then meticulously inspected for potential data leakage.
Our team was able to access this database because it was completely unsecured and unencrypted.

The fraudsters were using an Elasticsearch database, which is ordinarily not designed for URL use.
The purpose of this web mapping project is to helpmake the internet safer for all users.
We never sell, store, or expose any informationwe encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
Help Us Protect The Internet!

