The data in question was stored on a misconfigured Microsoft Azure cloud storage account.
The owner of the data (presumably Microsoft) failed to adequately secure the files.
As a result, they wereeasily accessible to anyone with even the most basic hacking skills.

Many of the pitchesincluded the source codes for software products- some of which were eventually released to the market.
The company then integrated each of these separate products into a single product line.
But rare are these times.

Screenshots from leaked pitches made to Microsoft
Most often, we need days of investigation before we understand whats at stake or whos exposing the data.
Some affected parties deny the facts, disregarding our research or playing down its impact.
So, we need to be thorough andmake sure everything we find is correct and accurate.

Screenshots from leaked pitches made to Microsoft
After an initial investigation,we identified two potential owners, starting with Canadian consulting firm Adoxio.
As KPMG now owns Adoxio, we contacted KPMG to notify it of the breach.
KPMG replied, confirming it didnt own the data and suggested it belonged to Microsoft.

We also suspected Microsoft was responsible.
While we received only automated responses from the company, the Azure Blob account was secured in the meantime.
Companies whose pitches were exposed include Adoxio (now Adoxio KPMG),Adobe, and more.
Data in the Blob storage account can be broken into two categories:
1.
Theseincluded products that the company eventually adopted, such as Package Deployer.
Thepartnership between Microsoft and Adobewas announced publicly before the discovery of the data breach.
Source codes
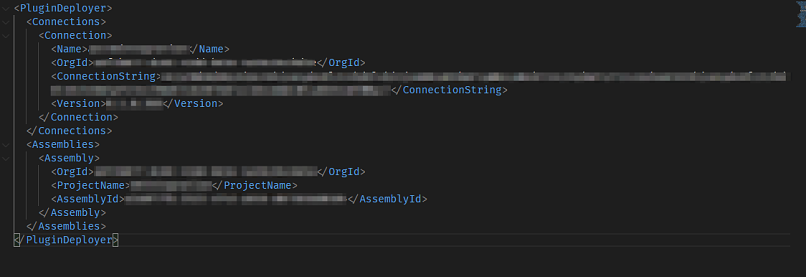
Some of the pitches were accompanied bysource codes for the products being presented to Microsoft.
The following screenshot shows a configuration file with passwords and addresses of databases and internal information about the tool.
Data Breach Impact
This breach could have hadsevere consequences for the companies exposed.
This data breach exposed the source codes for 10-15 software products belonging to numerous companies.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
They then examine each data store for any data being leaked.
Our team was able to access this Azure Blob account because it was completely unsecured and unencrypted.
As ethical hackers,were obliged to inform a company when we discover flaws in their online security.
The purpose of this web mapping project is to helpmake the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included a group offree VPNs secretly tracking their users activityand data and leaking it online.
Weve also uncovered potential criminal activities and scams targeting users onSpotify,Instagram, andFacebook.
You may also want to read ourVPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Check the Leak Box here »
just, comment on how to improve this article.




