But rare are these times.
Most often, we need days of investigation before we understand whats at stake or whos leaking the data.
Understanding a breach and its potential impact takes careful attention and time.

We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact.
So, we need to be thorough and check that everything we find is correct and accurate.

It is also worth noting that Mailfire is not responsible for the activity of the customers using their service.
Most of the websites using the tool were adult dating websites.
However, the database also contained data from e-commerce websites.

It also appeared that many of the websites shared common owners.
This is an absolutely massive amount of data to be stored in the open, and it kept growing.
Tens-of-millions of new records were uploaded to the server via new indices each day we were investigating it.

Its also possible older data had been stored before this time.
These often revealed private and potentially embarrassing or compromising details of peoples personal lives and romantic or sexual interests.
The following screenshots, taken from the database, show how people worldwide were exposed by this data leak.
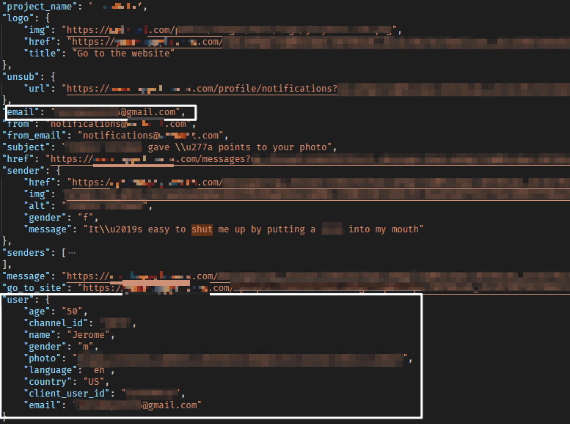
Fraud and Identity Theft
PII data exposed in the leak could be used in several fraudulent activities.
They could then offer their services as a safer alternative.
Furthermore, had the database been leaked publicly, competitors could have gone one step further.
Cyberattack
The server responsible for this data leak has already been successfully attacked once.
With access to the accounts, hackers could lock out users and exploit their account in numerous ways.
We found throughout several websites that disingenuous accounts were a huge issue.
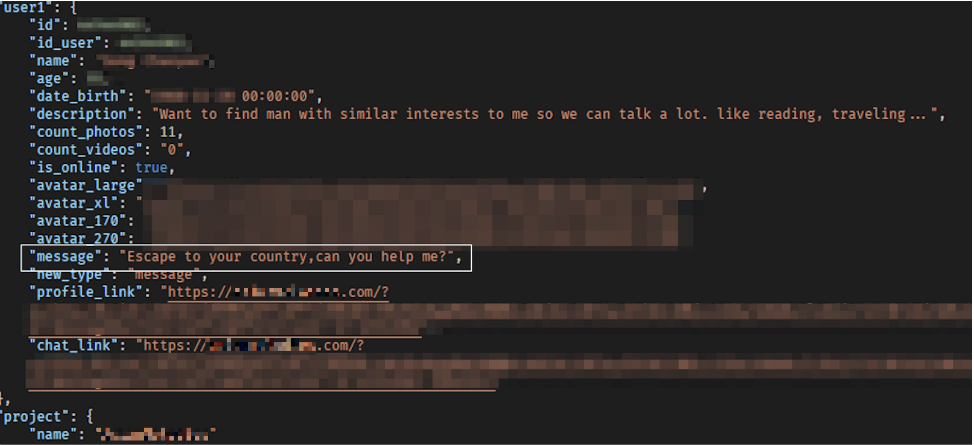
Many profile photos used were registered on scam databases or reused across accounts.
Some were simply photos of celebrities found online.
On some, man seeking man was not a working option.
Many of the sites had complicated, difficult to understand payment structures and some refused to offer refunds.
We verified this by asking topical questions about current affairs that the chatbot wasnt programmed to answer.
Furthermore, always review the amount of customer PII data being shared with 3rd party tools.
Check its payment and refund policies, to ensure youre not getting ripped off.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
When a vulnerability is reported to us, we rigorously test the relevant systems for weaknesses or vulnerabilities.
We also examine each weakness for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
The data was being stored on an Elasticsearch database, which is ordinarily not designed for URL use.
Asethical hackers, were obliged to inform a company when we discover flaws in their online security.
These ethics also mean we carry a responsibility to the public.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
We also revealed howa group of free VPNs exposed the internet activity of over 20 million users worldwide.

You may also want to read ourVPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Alternatively, anyone can submit a breachhere on vpnMentorany time, from anywhere, without compromising your privacy.


