Key Ring allows users to uploadscans and photos of membership and loyalty cards onto a digital folderon ones phone.
Company Profile
Key Ring offers users a One-Stop Shopping Solution.
Founded in 2009, Key Ring claims to have14 million users storing 60 million cards in 2019.

The app also includes more features designed to make shopping and participation in loyalty/membership programs easier.
Thecompany no longer operates within the EU,as it was unable to comply with GDPR.
Understanding a breach and its potential impact takes careful attention and time.

We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
In this case, Key Ring was storing the files on an AWS S3 bucket.
S3 buckets are a popular storage solution on AWS and offer robust security features.

The buckets were secured shortly after.
Anybody with a web web app could have viewedover 44 million images uploaded by Key Ring users.
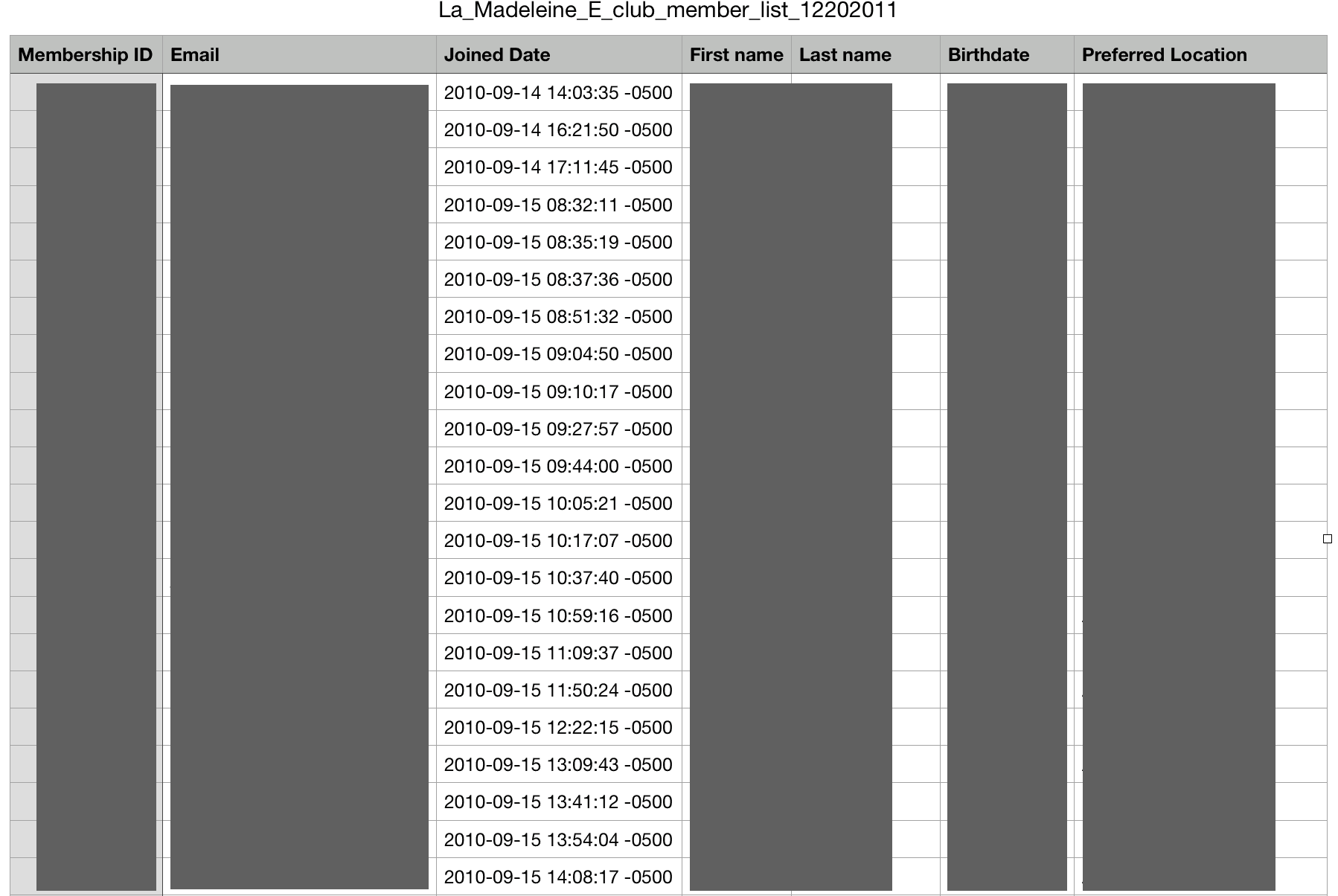
As such, the bucket also containedCSV files detailing membership listsand reports for many of these businesses.

These listscontained the Personally Identifiable Information (PII) data of millions of people.
Example 6:Patient ID for a medical cannabis program
Combined, they offered criminal hackers an absolute goldmine.
Key Rings database could have facilitated massive fraud and identity theft schemes targeting millions of peoplein America and Canada.

Account Takeover:Criminals gain access and take control of your financial, credit, and bank accounts.
Alternatively, they couldsell the data on the dark web to criminals around the world.
The ripples could be felt far beyond the initial target.
For this reason, theyre one of the most popular, oldest, and dangerous forms of online fraud.
The company itself could have been in dangerif this database had criminal hackers discovered the database.
These may be phishing campaigns.

To learn more about data vulnerabilities in general, read ourcomplete guide to online privacy.
Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities.
They examine each weakness for any data being leaked.

Our team was able to access this database because it was completely unsecured and unencrypted.
As ethical hackers,were obliged to inform a company when we discover flaws in their online security.
The purpose of this web mapping project is to helpmake the internet safer for all users.
Wenever sell, store, or expose any informationwe encounter during our security research.
Our ethical security research team hasdiscovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leakexposing the data of 10,000s of American restaurant diners.

[Publication date: 18.02.2020]
just, comment on how to improve this article.









