Pray.com offers daily prayer guidance and similar faith-based audio content and has proven incredibly popular since launching in 2016.
In fact,most people exposed in Pray.coms data breach dont even use the app.
Currently based in Santa Monica, California, Pray.com is available on iOS and Android.

We can confirm the app has been installed at least 1 million times on Android alone.
But rare are these times.
Most often, we need days of investigation before we understand whats at stake or whos exposing the data.
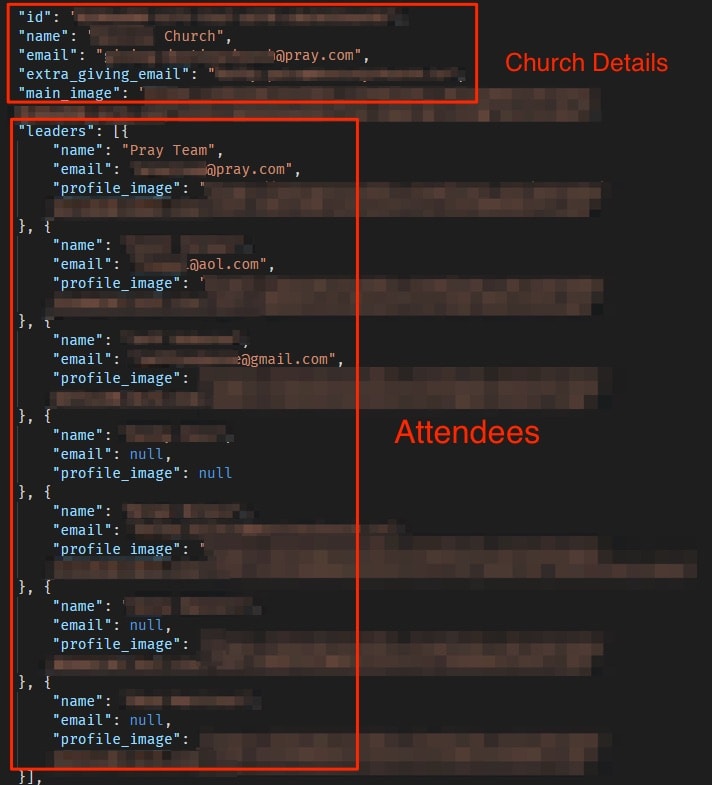
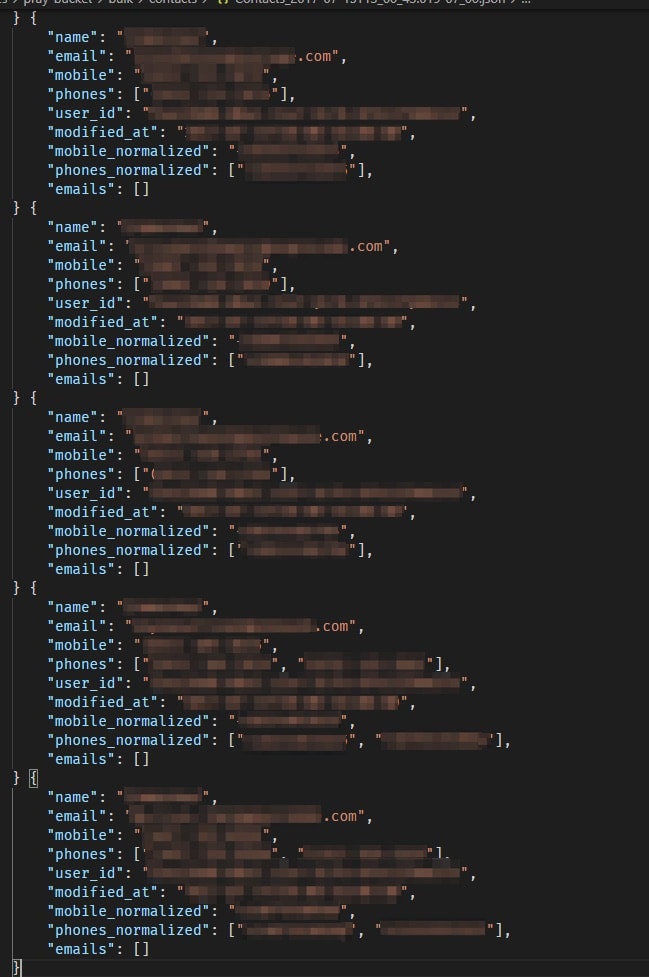
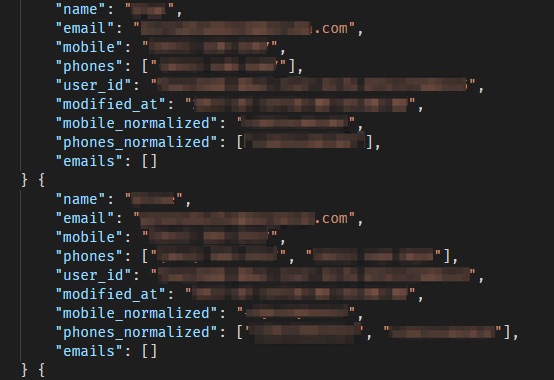
List of church attendees exposes their PII data
Doing so speeds up the apps performance considerably.
Pray.com seemingly overlooked installing proper security measures on its CloudFront account.
Pray.coms developers accidentally created a backdoor that gave complete access to all the files they had tried to protect.

List of church attendees exposes their PII data
Once we confirmed all the details of the breach, we reached out to Pray.com and presented our findings.
Note:Amazon isnt responsible for the misconfigurations in this report.
It provides detailed instructions on how to use AWS products and services.

The owner of the data is the only liable party.
Most of these people didnt use the app, and many werent even living in the USA.
We suspect these were used in social media marketing efforts.

A little over 80,000 files were made private, only accessible to people with the right security permissions.
However, Pray.com failed to replicate these security measures on its Cloudfront CDN, which remained publicly accessible.
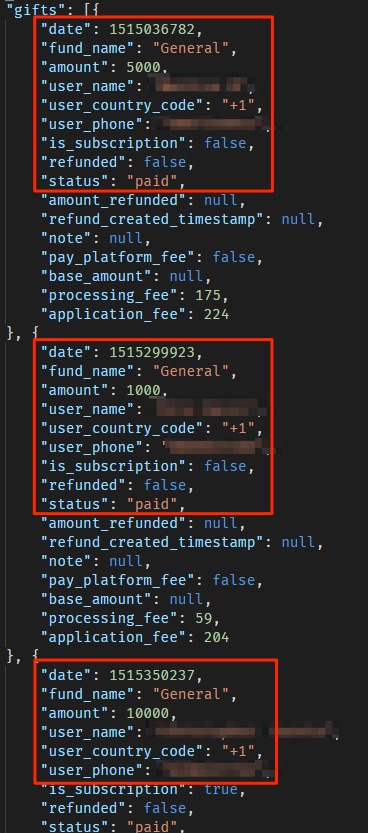
Facilitating church donations feels like one of the most popular features on the Pray.com app.

Users can choose any church that has partnered with Pray.com and donate directly via the app.
All of this information was exposed.
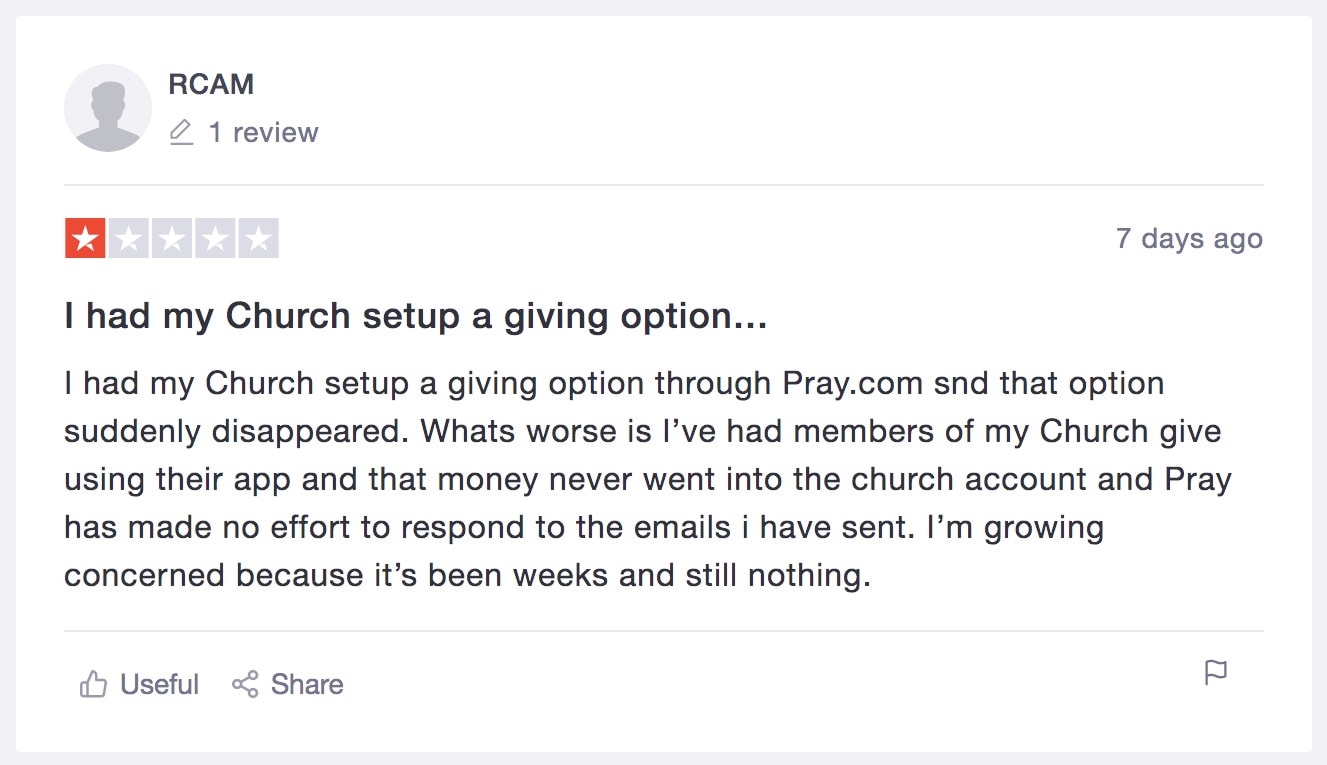
The app also has no records of donations being forwarded to the respective churches.
Pray.com has a built-in social data pipe called Communities.
They were simply people whose contact details had been saved on a Pray.com users machine.
Pray.com inadvertently accessed and exposed these also.
The implications for the app’s users, and the general public, should not be understated.
The impact of a successful attack like this on a victim’s personal and financial well-being could be devastating.
This suggests that Pray.com had harvested the PII data of US government and military personnel without their approval.
If cybercriminals gained access to these contacts, they would likely aggressively target the individuals exposed.
Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
Every weakness detected is scrutinized for any indication of data exposure.
Our team was able to access Pray.coms S3 buckets because they were completely unsecured and unencrypted.
As ethical hackers,were obliged to inform a company when we discover flaws in their online security.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
Help Us Protect The Internet!








