The company was using an unsecured server to store vast amounts of data collected from users on its games.
Their games are a mix of role-playing and fantasy adventures that, combined, have over 1,500,000 downloads.
But rare are these times.

Instead, we often need days of investigation before we understand whats at stake or whos leaking the data.
Understanding a breach and its potential impact takes careful attention and time.
We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
![]()
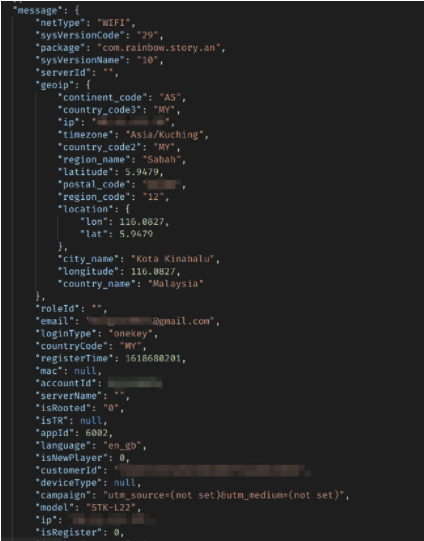
Tracking records for a user in the Philippines
Some affected parties deny the facts, disregarding our research or playing down its impact.
So, we need to be thorough andmake sure everything we find is correct and accurate.
In this case, our team discovered the EskyFun database in early July.
![]()
Tracking records for a user in the Philippines
*
Hong Kong CERT was rapid and proactive in its response, seeking additional information to take appropriate measures.
Most countries have a similar agency to address localized data leaks and hacks.
However, despite only covering 7 days, the server still contained over 360 million records from players.
![]()
This is an enormous amount of data collected from a few small, not well-known mobile games.
The following table shows the various tracking programs connected to EskyFuns games.
But if someone roots their machine, they have bypassed these restrictions.
![]()
Receipts: 148,000+
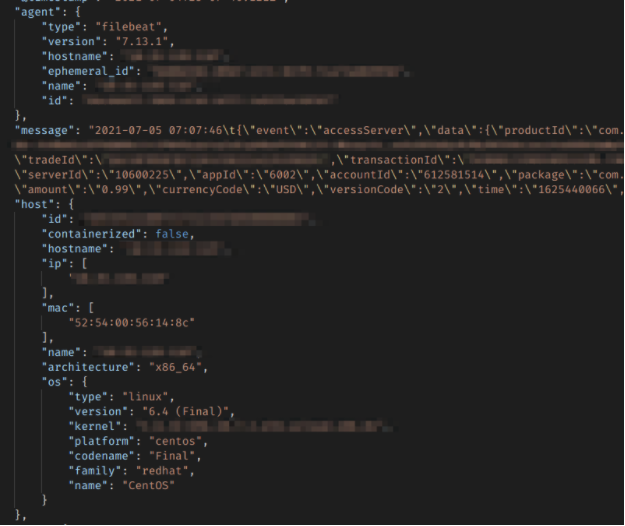
The database contained receipts generated by purchases made in-game over the previous 7 days.
For example, suppose a player is having issues making payments within a game.
By focusing on these users, hackers could reap huge financial rewards from a small group of victims.
However, the more significant risk comes from hackers using these passwords outside of EskyFuns web connection.
This is because most internet users share their passwords across multiple private accounts and devices.
For example, a persons EskyFun account password might be the same as their bank account.
Criminal hackers know this.
The result could be catastrophic.
And worse, it would be almost impossible to trace a successful attack back to EskyFun.
Corporate Espionage
The leak also poses a risk to EskyFun.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldnt be exposed.
They then examine each data store for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
EskyFun was using an Elasticsearch database, which is ordinarily not designed for URL use.
As ethical hackers, were obliged to inform a company when we discover flaws in their online security.
The purpose of this web mapping project is to helpmake the internet safer for all users.
Wenever sell, store, or expose any informationwe encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has includedexposing the growing popularity of cybercrime groups on Telegram.
We also revealed howa data leak by the biggest US baby apparel chainhad compromised 100,000s of customers data.
You may also want to read ourVPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Check the Leak Box here »
kindly, comment on how to improve this article.
![]()
![]()




