21 Buttons mixes online shopping with social media.
Users post photos of their favorite outfits with links to the brands theyre wearing.
Their followers can then purchase their favorite items directly from the relevant brands from within the app.
Users on 21 Buttons Rewards program earn a commission for any purchases made via their profiles.
Had these records fallen into the hands of criminal hackers, the consequences for those exposed would be profound.
The companys flagship app combines fashion, social media, and e-commerce.
Influencers upload photos with their favorite wardrobe pieces to 21 Buttons and link to the stores where theyre available.
Some affected parties deny the facts, disregarding our research, or playing down its impact.
So, we need to be thorough andmake sure everything we find is correct and accurate.

At the time of publication, we are still waiting to be contacted.
And it appears the bucket contained media files from every single user on the 21 Button app.
However, 21 Buttons has over 5 million downloads just on Android and boasts millions of monthly active users.

We believe the bucket contained media files from every single user on the app.
seems as if all this data was already publicly available on the app and 21 Buttons website.
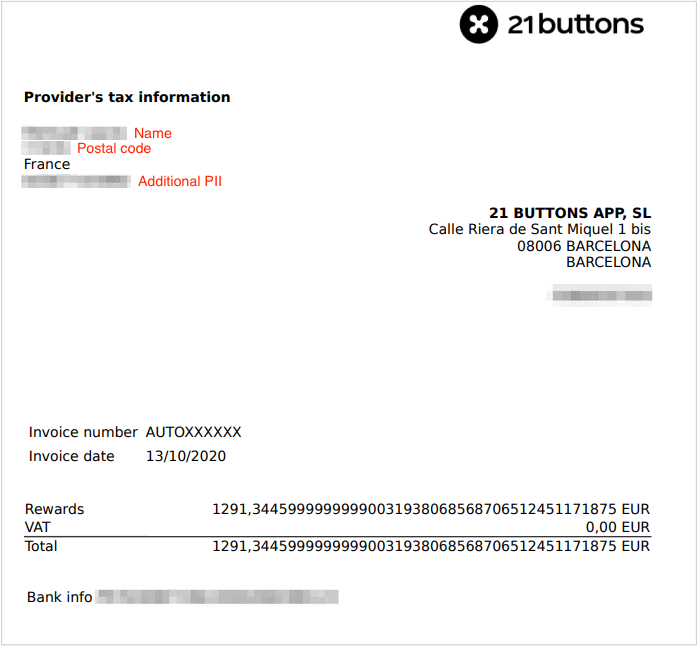
Influencer Invoices
Unfortunately,thats not all 21 Buttons was storing on the S3 bucket.
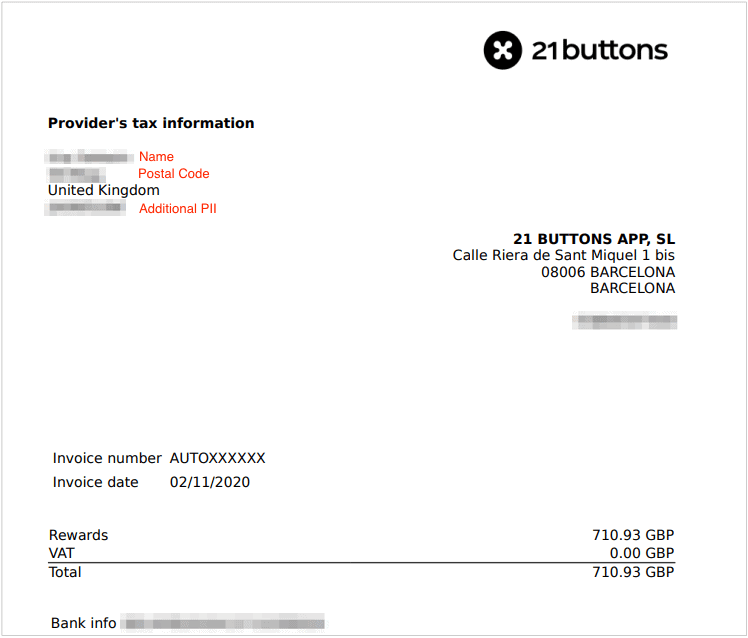
Any time someone purchases an item via their profile, Rewards program users earn a commission.
In a phishing campaign,hackers and cybercriminals send victims fraudulent emails imitating real businesses.
This could include anything from credit card fraud and bank account takeover to wholesale identity theft.
This doesnt just make the people affected vulnerable to phishing and fraud, as detailed above.
All of these outcomes could have asignificant negative impact on 21 Buttons short term revenue and long term growth.
Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
It shows you the many ways cybercriminals target internet users andthe steps you might take to stay safe.
Each detected weakness is thoroughly evaluated for potential data exposure.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
As ethical hackers,were obliged to inform a company when we discover flaws in their online security.
The purpose of this web mapping project is to helpmake the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
Help Us Protect The Internet!


