It specializes in creating SMS solutions for large and small businesses.
Some affected parties deny the facts, disregarding our research or playing down its impact.
So, we need to be thorough andmake sure everything we find is correct and true.
In this case, it was quite easy to identify TrueDalog as the database owner.
Their host ID api.truedialog.com was found throughout.
Once the full extent of what had been exposed in TrueDialogs database was clear, we contacted the company.
The database has since been closed but TrueDialog never replied to us.
When we last looked at the database it included 604 GB of data.
This included nearly 1 billion entries of highly sensitive data, which well detail below.

Example of Exposed Data
Its difficult to put the size of this data leak into context.
Tens of millions of people were potentially exposed in a number of ways.
Its rare for one database to contain such a huge volume of information thats also incredibly varied.

The database contained entries that were related to many aspects of TrueDialogs business model.
The company itself was exposed, along with its client base, and the customers of those clients.
There was also some more detailed user information that was found.
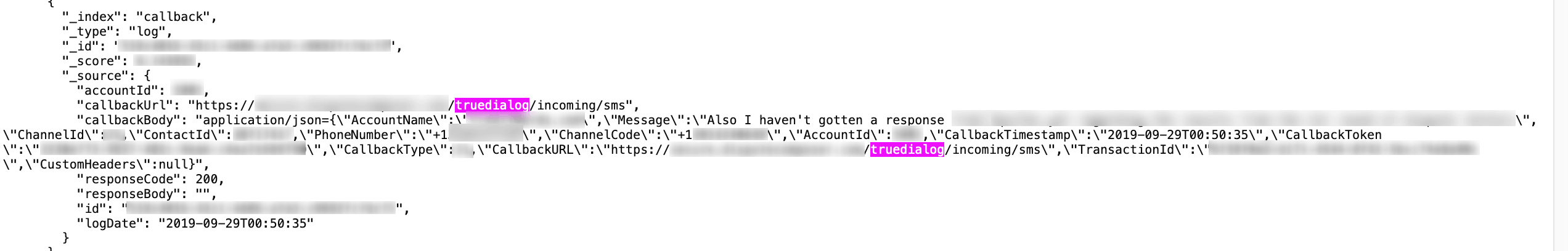
These logs revealed important details as to how the database is structured and managed.
This could by itself had exposed vulnerabilities.
The available information can be sold to both marketers and spammers.

Their competitors could have gotten a look into their backend and seen how the company is run from within.
For Companies Using TrueDialog
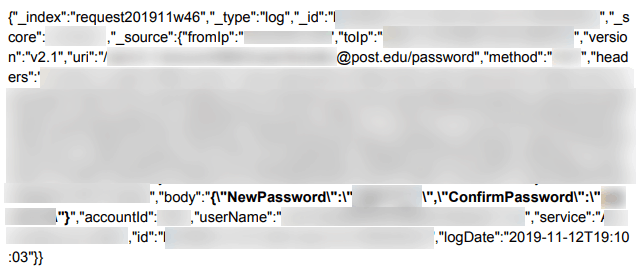
The account credentials were not only left unprotected but in cleartext as well.
This is another fallout of the unencrypted message system that TrueDialog uses.
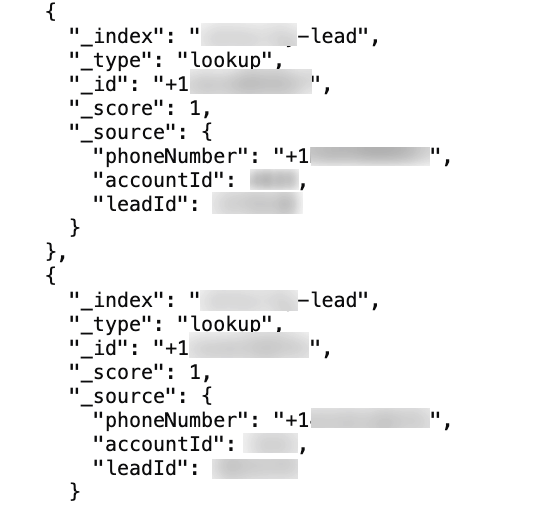
It would be easy for a corporate spy to read confidential messages that were sent by a rival company.
This leak also exposed records regarding sales leads for potential customers of TrueDialog users.
The vast amount of contact details itself is a huge asset for spammers.
Moreover, exposed personal details can prove very valuable so that target individuals to respond to spam and phishing.
With all the message content exposed in cleartext, scammers will have plenty of ammunition for blackmail.
Our investigators utilize port scanning to scrutinize specific IP blocks and inspect system vulnerabilities by testing open gaps.
Each of these gaps is carefully assessed for any indications of data leakage.
When they find a data breach, they use expert techniques to verify the databases identity.
We then alert the company to the breach.
If possible, we will also alert those affected by the breach.
Our team was able to access this database because it was completely unsecured and unencrypted.
The company uses an Elasticsearch database, which is ordinarily not designed for URL use.
The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, were obliged to inform a company when we discover flaws in their online security.
This is especially true when the companies data breach contains such private information.
However, these ethics also mean we carry a responsibility to the public.
TrueDialog users must be aware of a data breach that impacts them also.
hey, comment on how to improve this article.




