The breach originated from a misconfigured Amazon Web Services S3 bucket, exposing private files belonging to the company.
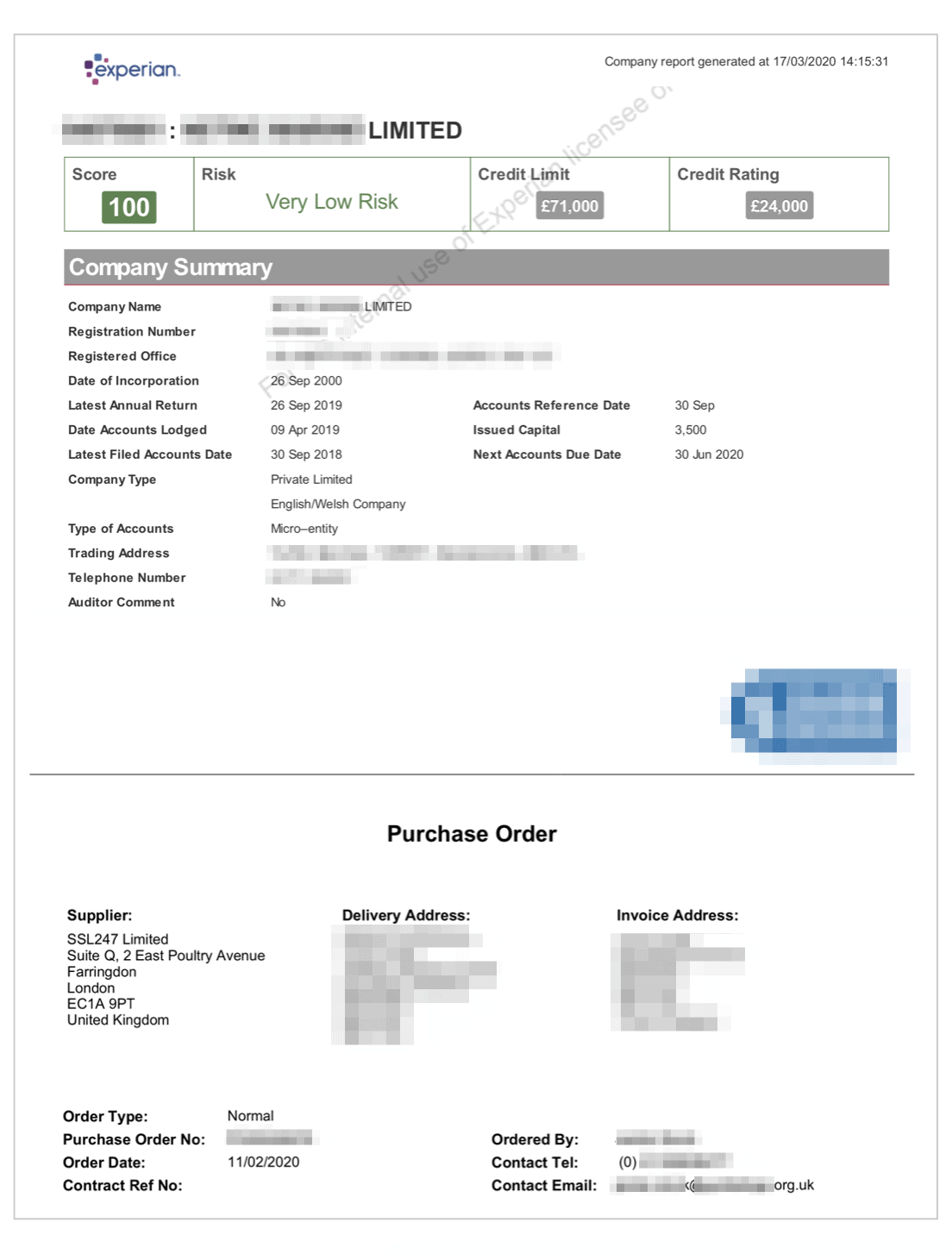
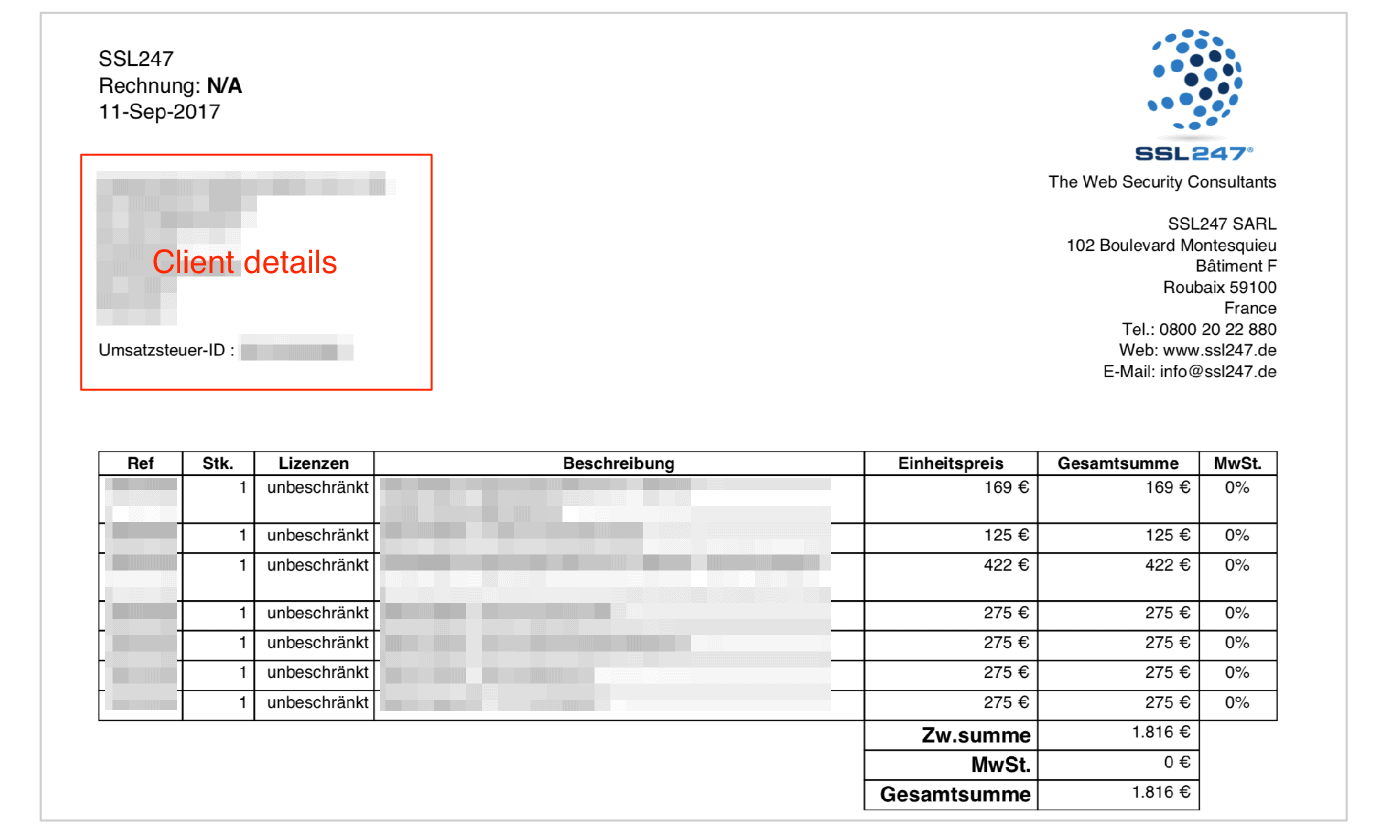
Many of these filesincluded detailed information about customers purchasing security products through SSL247.
Exactly what SSL247 is trying to prevent.

Billed as Europes Leading Web Security Consultancy Firm, SSL247 started as a reseller of SSL certificates.
But rare are these times.
Most often, we need days of investigation before we understand whats at stake or whos exposing the data.

Some affected parties deny the facts, disregarding our research, or playing down its impact.
So, we need to be thorough andmake sure everything we find is correct and accurate.
For such a well-regarded company within the internet security industry to react in this way is surprising and disheartening.

We estimate up to 350,000 people and businesses in total.
Many of these files would have been publicly available, and any risk from them being exposed minimal.
They couldalso trick victims into providing credit card detailsand other sensitive, valuable information used to steal from them.

This privacy is an invaluable asset for many,including activists and political dissidents.
The negative consequences of exposing such information cannot be understated.
This is what happened to Dutch certificate authority DigiNotar in 2011.
All in the space of a few short months.
SSL247 risks losing trust from users and damage to its reputation as a result of the breach.
People may question SSL247s credentials as a result, and look to other providers when purchasing such products.
If it cant provide such information, it may lose valuable corporate relationships.
Finally,competitors will be scrutinizing this breach for an opportunity to exploit it.
Theyre usually the result of an error by the owner of the bucket.
Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
Each identified weakness is then meticulously scrutinized for any indications of data exposure.
Our team was able to dive into the S3 bucket because it was misconfigured and completely unsecured.
As ethical hackers,were obliged to inform a companywhen we discover flaws in their online security.
The purpose of this web mapping project is to helpmake the internet safer for all users.
We then verify and report any submission deemed a legitimate threat to the publics safety.
We never sell, store, or expose any informationwe encounter during our security research.
This includes any information reported to us via The Leak Box.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
[Publication date: 17.06.2020]
just, comment on how to improve this article.




