But rare are these times.
Most often,we need days of investigation before we understand whats at stake or whos leaking the data.
Some affected parties deny the facts, disregarding our research or playing down its impact.

So, we need to be thorough and confirm everything we find is correct and true.
They refused to accept the disclosure of our findings.
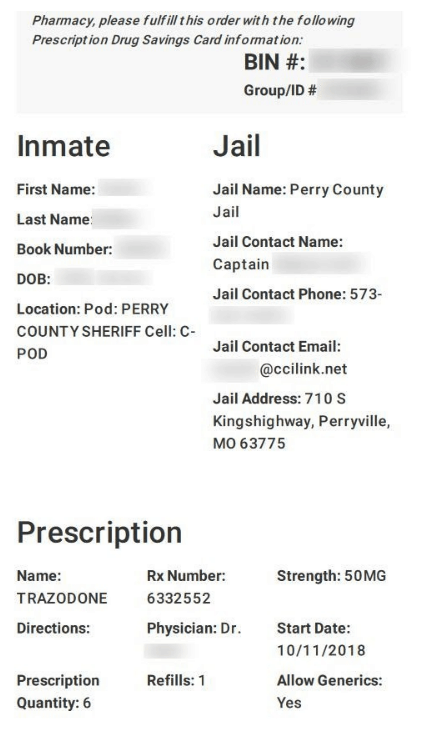
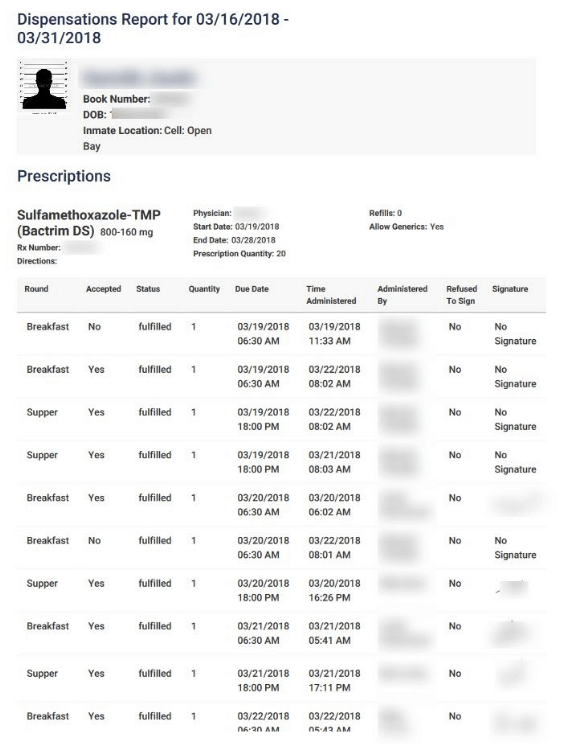
Whats not meant to be available to all is individual specific medication information and additional sensitive data.
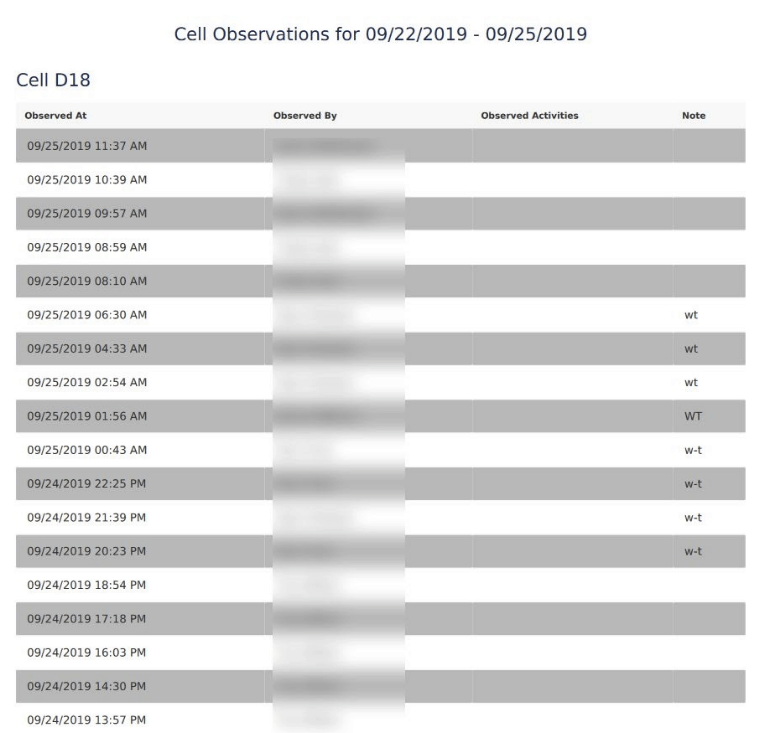
Data Breach Impact
This leak represents a potentially severe threat to those whose data has been exposed.
It has many implications, all of which could very well ruin the lives of those involved.
For many of the apps customers, there is a current inmate roster on their Detention Centers website.

you could alsouse a VPN to hide some of the data collectedby Jailcore.
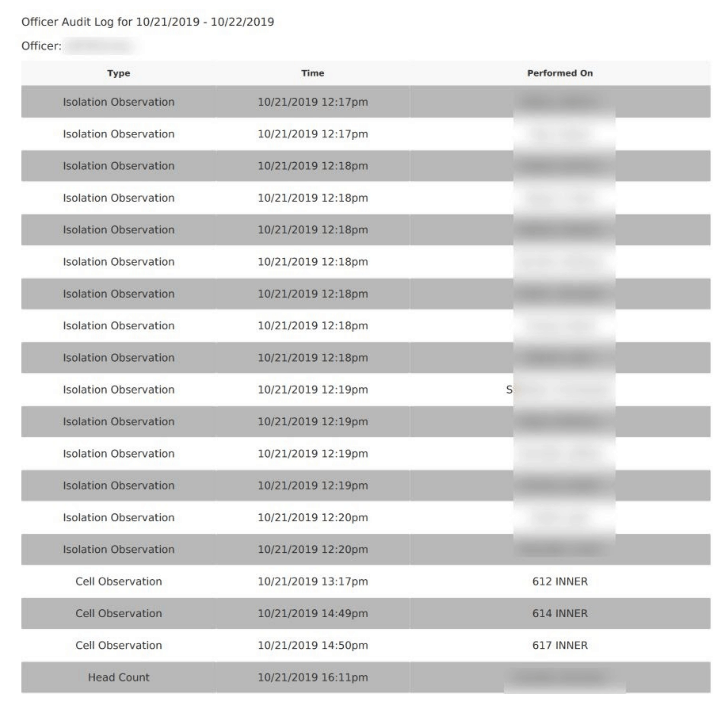
Each of these exposed gaps is closely inspected for any data leakage.
When they find a data breach, they use expert techniques to verify the databases identity.

We then alert the company to the breach.
If possible, we will also alert those affected by the breach.
We were able to access Jailcores S3 bucket because it was completely unsecured and unencrypted.
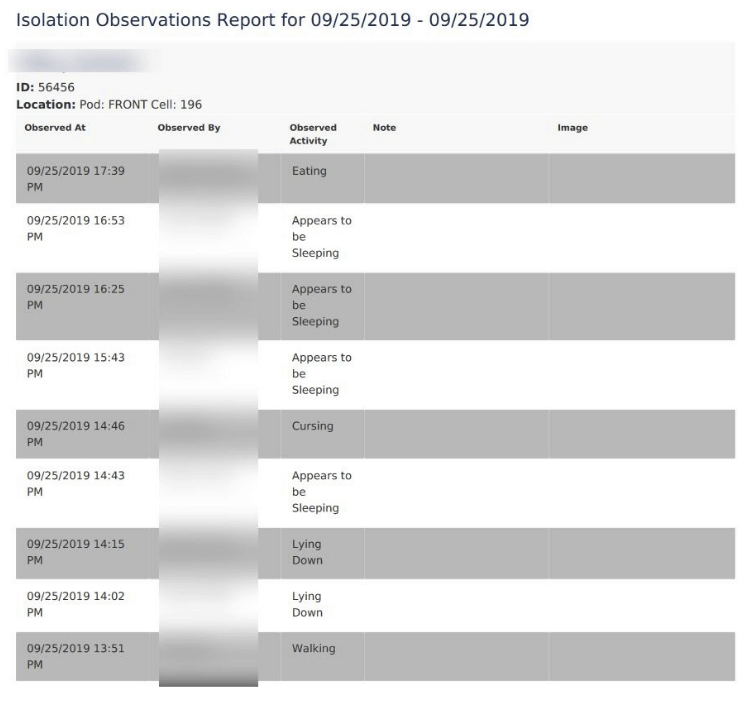
Using a web surfing app, the team could access all files hosted on the database.
The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, were obliged to inform a company when we discover flaws in their online security.
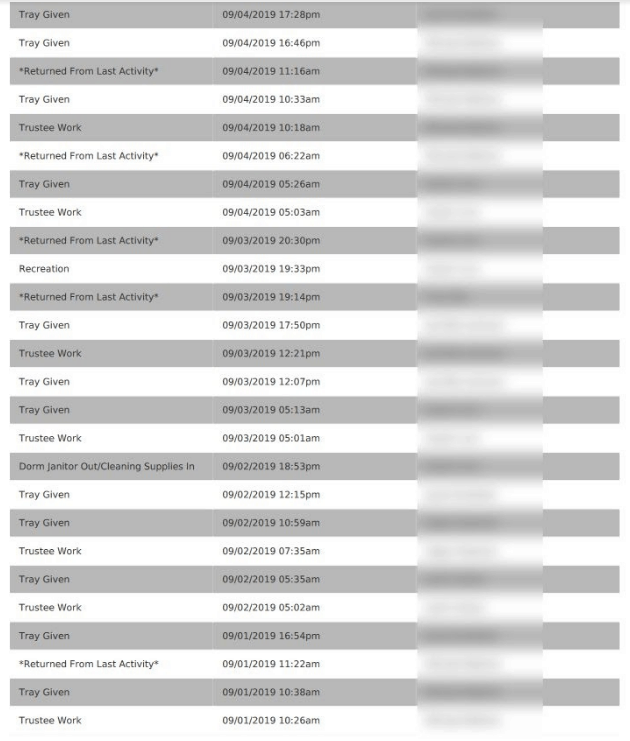
However, these ethics also mean we also carry a responsibility to the public.
This is especially true when the companies data breach contains such a huge amount of private and sensitive information.
About Us and Previous Reports
vpnMentoris the worlds largest VPN review website.
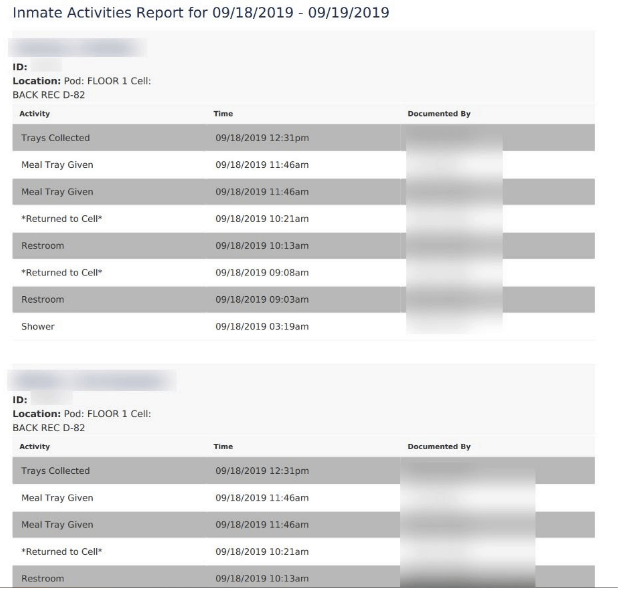
In the past, weve discovered a breach in LightInTheBox thatcompromised the data of its customers.
We also recently revealed that a company owned by major hotel chain AccorHotelsexposed over 1TB of guests data.
You may also want to read ourVPN Leak Report and Data Privacy Stats Report.
JailCore Comment:“1.
We are a startup company that currently works with 6 jails totaling 1,200 inmates.
Not the 36,000 mentioned in an earlier email.2.
Meaning all other reports with any mention of medication were all used for demonstration purposes only.3.
These are incarcerated individuals, not free citizens.
Meaning, the same privacy laws that you and I enjoy, they do not.
I would implore you to get all facts straight before writing/publishing anything.
We have rectified the situation of the data held within a report.
We ensure all of our data is encrypted end to end as well as when it is at rest.

The digital security industry now recommends SHA-256 as the standard signature hash algorithm for SSL certificates.
Data for storage is split into chunks, and each chunk is encrypted with a unique data encryption key.
The data is encrypted when stored in database tables, temporary files, and backups.
Data stored in GoogleCloud Platform is encrypted at the storage level using either AES256 or AES128.”
c’mon, comment on how to improve this article.








