vpnMentor’s research team found a leak in the Fieldwork software database.
Fieldwork offers small business software to manage their operations efficiently.
We contacted Fieldwork when we discovered the leak.
They wereprofessional and efficientafter receiving our email.
Fieldwork closed the leak 20 minutes after speaking to them.
Owned by Anstar, which produces pest control products, the software helps track employees who make house calls.
The customer portal also includes invoice templates, scheduling interfaces, and product tracking.
Even so, it would have been a more complex project.
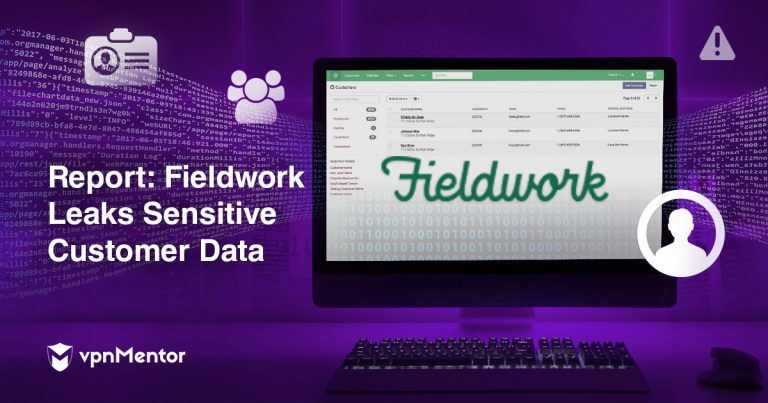
This is a log for an email template about logging in to the Fieldwork portal.

This piece of data includedemail addresses that are not publicly availablefor clients to see.
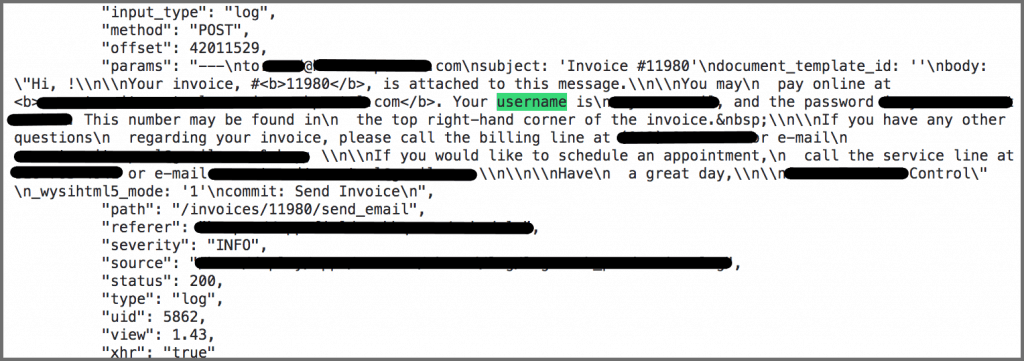
We found an extensive amount ofdetailed communicationin the data logs.
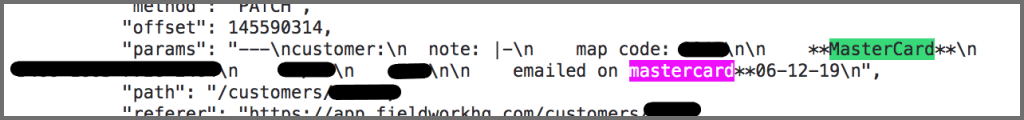
Theclient disclosed the last four digits of their account credit card.

A bad actor could have used this to their advantage.
This log shows that there are alsophotos accessible in the data.
It also exposed a user’sIP address.
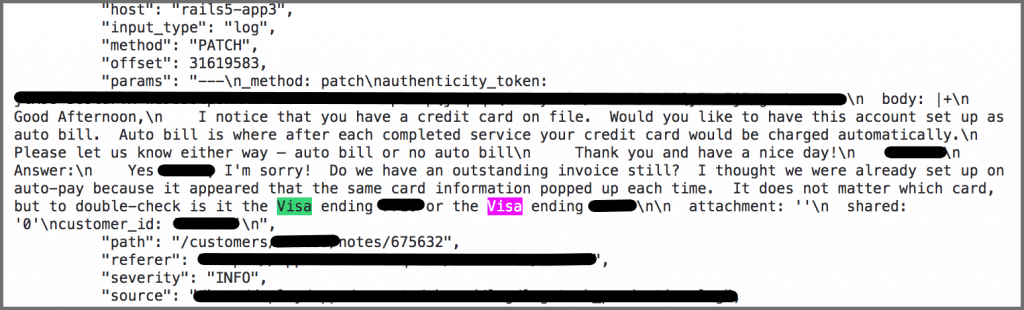
This photo was linked inan open Amazon bucketthat we discovered in the data.
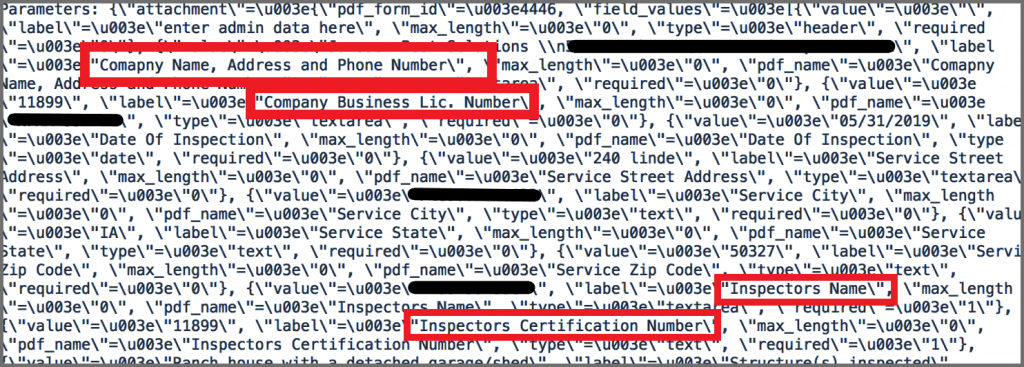
It also provides the company’s license number.
This log does hide the password, but it gives us clearemail addressesassociated with an account.
Even without any customer identification, thefull credit card number, with anexpiration dateand aCVV numberwas visible.
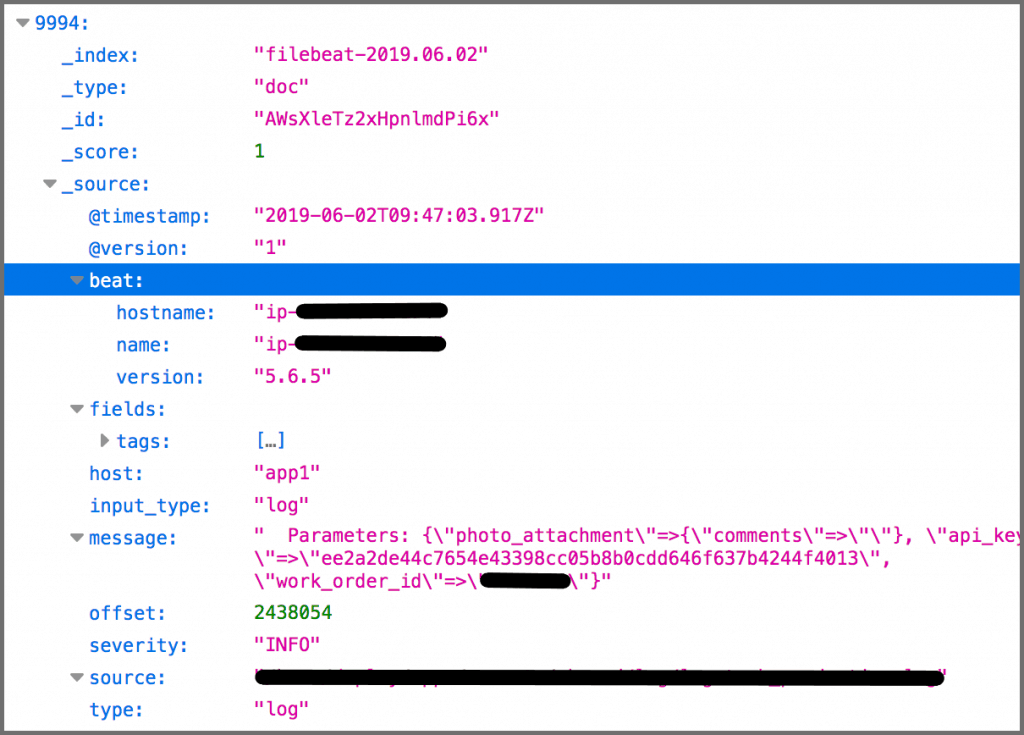
We also had free access to anauto-login linkthat was included in the database.
This allowed access to the customer portal.

Access to the portal is aparticularly dangerous piece of information.
They could alsolock the company out of the accountby making backend changes.
Furthermore, if the login links were easy to organize, someone with malicious intent could easily save them.
In that case, it wouldn’t matter if the database were closed.
This opens up the possibility ofin-person theft or attacks.
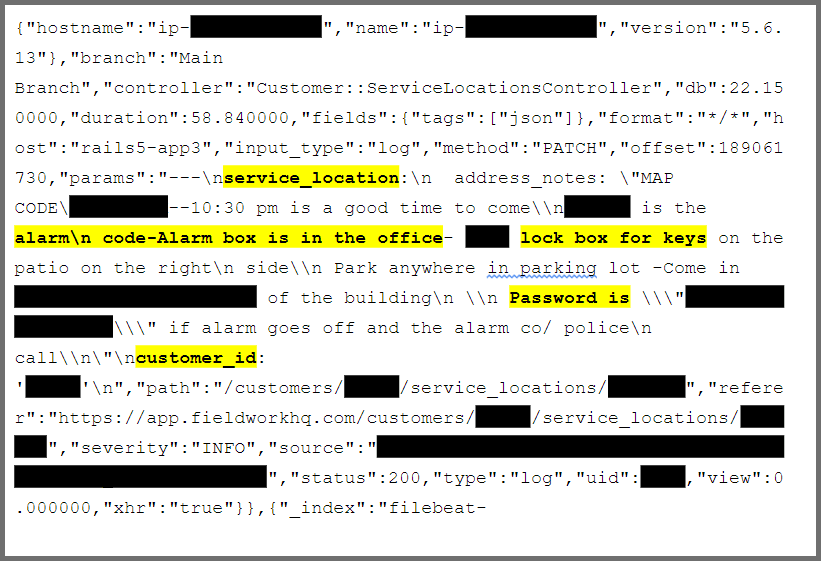
Because clients openly disclosed alarm codes or how to access their keys, there could beinsurance consequencesas well.
Insurance companies couldvoid a policyif policyholder negligence caused a break-in.
The photos that were viewable in the Amazon photo bucket could have served as further confirmation of a location.
They also may havedisclosed that a client had valuable inventory.

With the location information, a thief couldbreak in undetected and make off with client stock.
We had access to all of the credentials needed to place a purchase or even copy a card.
However, portal access makes it simple to determine.
Credentials from one account can often be used to access another account.
Some could even open new accounts in a user’s name.
One danger of exposing email addresses involves malicious playersusing them for phishing attacks.
This cangive hackers direct accessto a system that had no connections to this open database.
Companies have a moral obligation to keep their clients' data secure.
In this case, any company using Fieldwork did not uphold this.
A hacker could also sell stolen data to a competing company.
Lastly, we discovered signatures in the data.
Bycopying the shape of a signature, a bad actor has yet another tool tocommit identity theft through forgery.
Most digital signatures link to an IP address.
Here are a fewexpert tips to prevent or patch a breachin a database.
Led by Ran and Noam, the group performs scans ofknown IP blocks' ports.
This enables them to search forvulnerabilities in the system.
Each time we discover a breach, wecontact the ownerof the database to alert them to the leaking data.
If possible, we will also inform others affected by the openings in the system.
Our goal with this project is to create asafer and more secureinternet for users everywhere.
About Us and Previous Reports
vpnMentoris the worlds largest VPN review website.
We recently discovered a massivedata breach impacting 78 thousand patients taking Vascepa.

Pleaseshare this report on Facebookortweet it.
yo, comment on how to improve this article.







