V Shred sells numerous online and physical products related to dieting, nutrition, and fitness.
The company offers many different products within fitness, nutrition, and dieting.
For a brand thats only two years old, V Shred boasts a massive international audience.

But rare are these times.
Most often, we need days of investigation before we understand whats at stake or whos exposing the data.
Some affected parties deny the facts, disregarding our research, or playing down its impact.
So, we need to be thorough andmake sure everything we find is correct and accurate.
Our team quickly confirmed V Shred as the S3 buckets ownerand contacted the company immediately.
We also reached out to AWS directly to notify them of the breach.

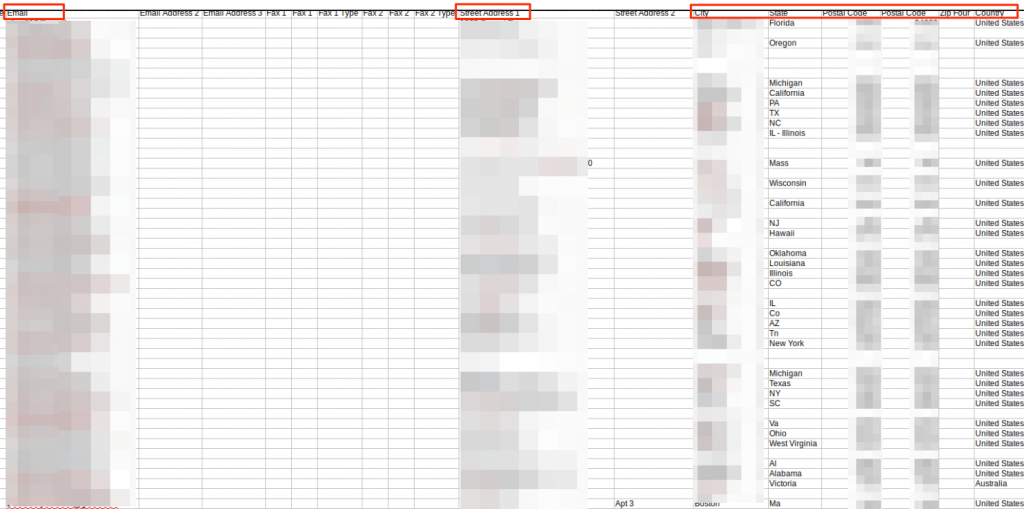
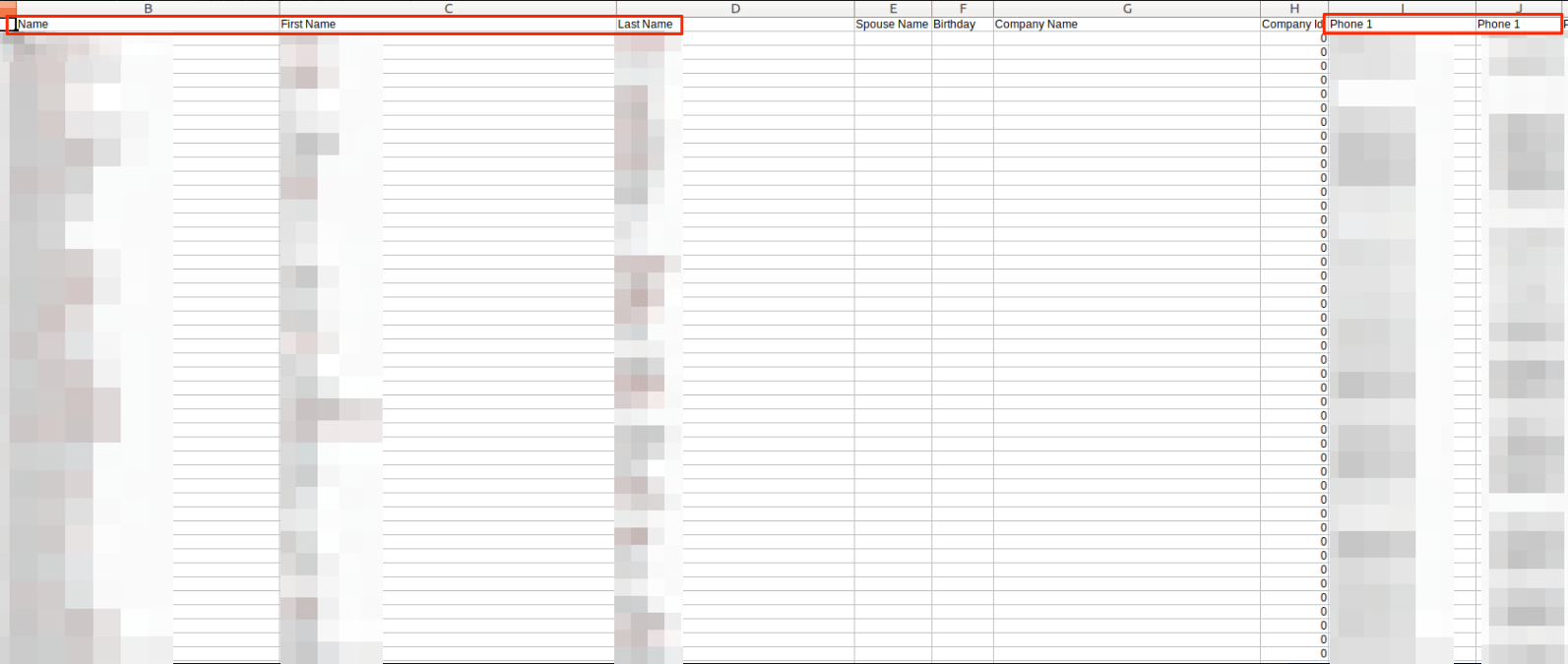
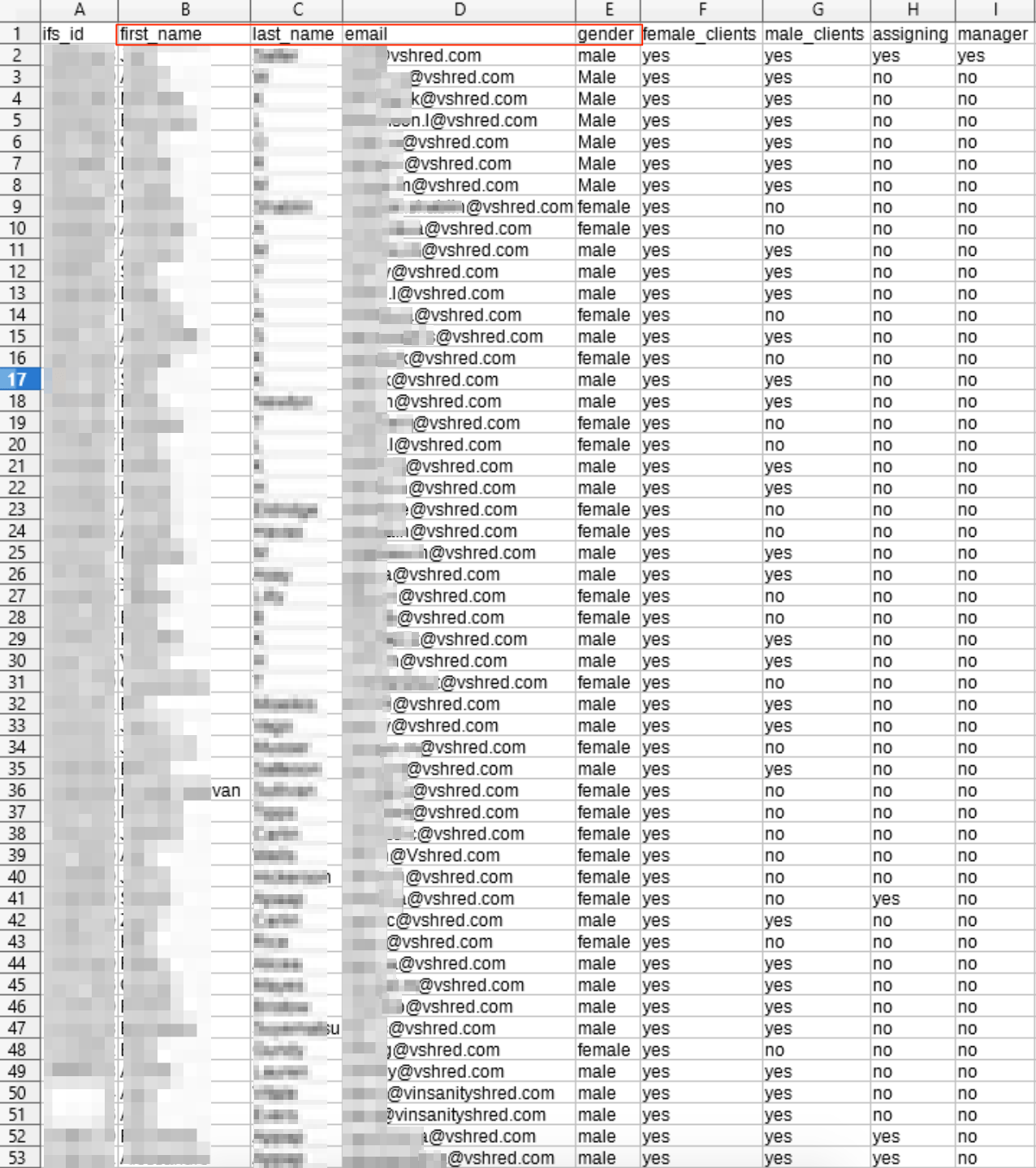
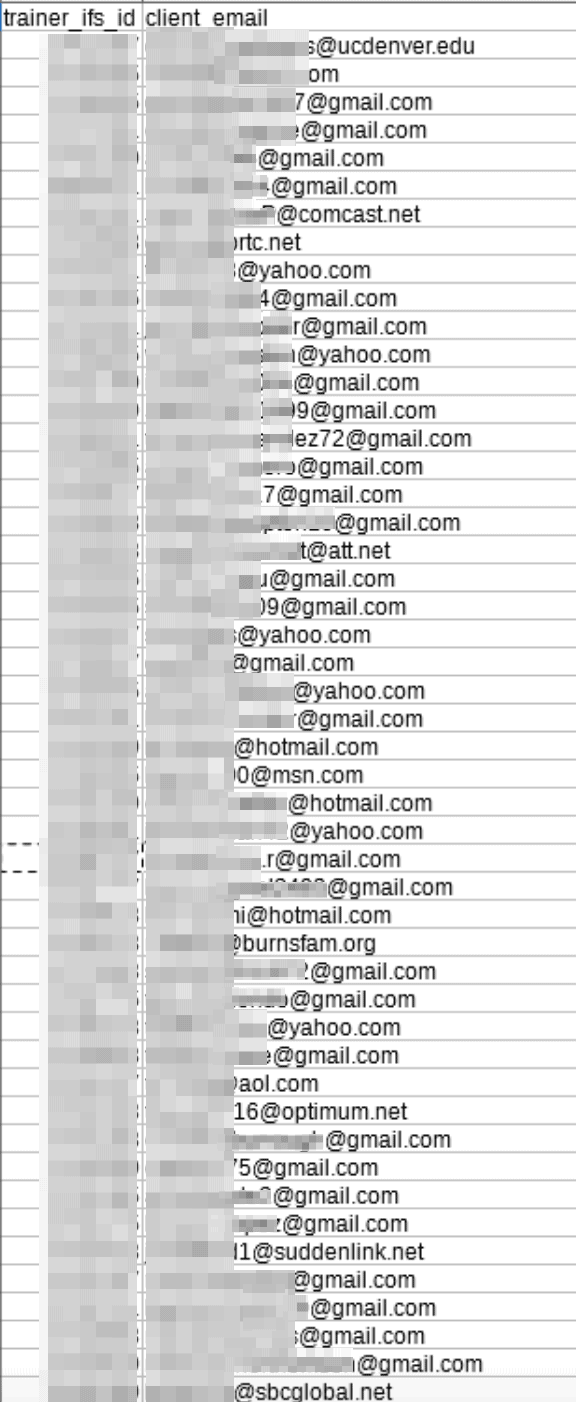
Combined, they containedhuge amounts of PII data for each individual listed.
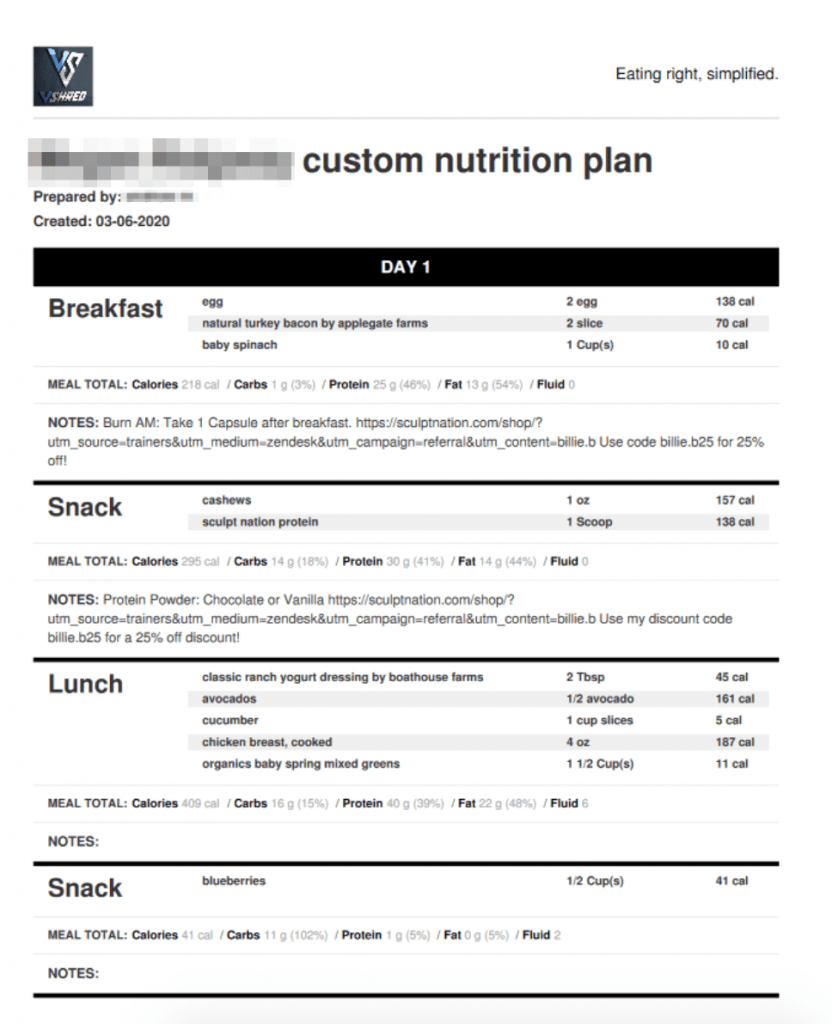
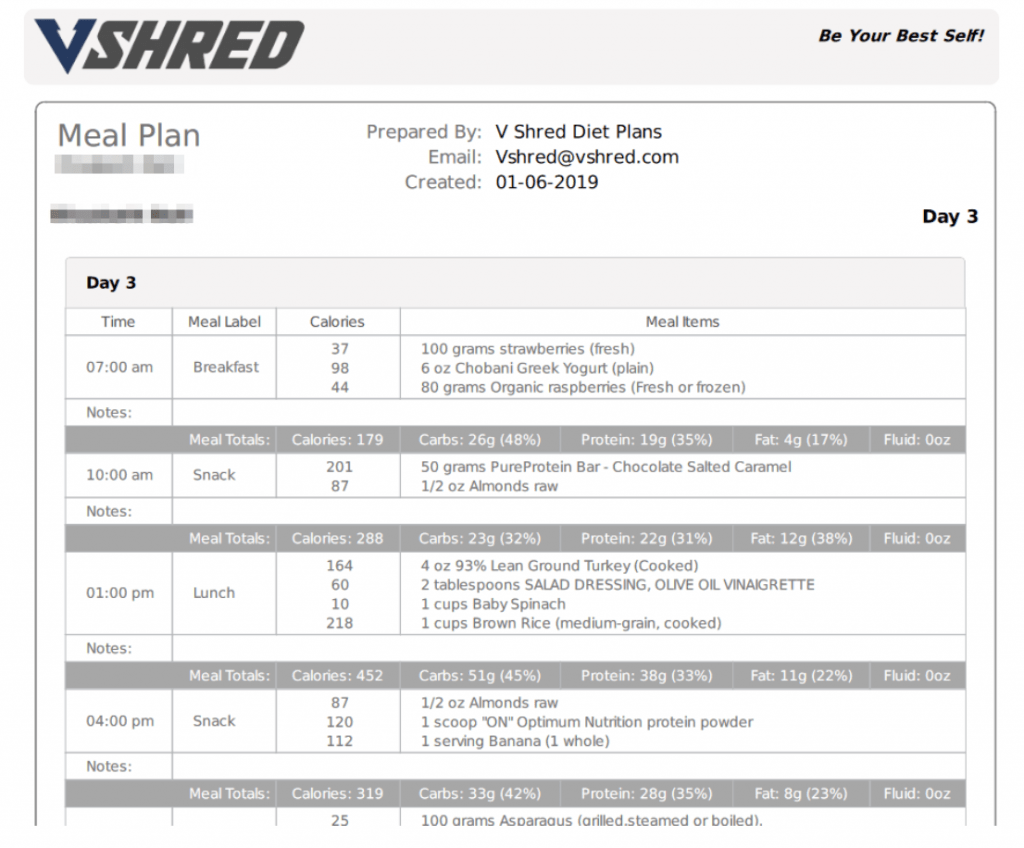
Weve also included some of the meal plans and photos uploaded by V Shred customers.
However, its still responsible for protecting the people using its products and signing up for its services.

A phishing campaign involves sending fake emails to a target, imitating a real business.
People using V Shreds products and membership plans could be incredibly self-conscious and easily susceptible to such blackmail tactics.
As such, the industry it works in will become more competitive - and ruthless.
The exposed meal plans were paid products, for example, customized to each customer.
A slip up like this data breach could cost V Shred dearly in the short and long term.
As a result, the company may face investigations, audits, and even fines.
Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
Each identified weak point is then thoroughly inspected for any signs of exposed data.
Our team was able to access V Shred’s S3 bucket because it was completely unsecured and unencrypted.
As ethical hackers,were obliged to inform a company when we discover flaws in their online security.
The purpose of this web mapping project is to helpmake the internet safer for all users.
We then verify and report any submission deemed a legitimate threat to the publics safety.
We never sell, store, or expose any informationwe encounter during our security research.
This includes any information reported to us via The Leak Box.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
[Publication date: 17th June 2020]
c’mon, comment on how to improve this article.








