They were discovered by different researchers working independently.
After confirming their findings, our team discovered a third flaw, which had also gone unnoticed.
Sophos has already published hotfixes to resolve both of these vulnerabilities.

These are all spread between 120+ countries.
Cyberoam mostly builds technology solutions for large enterprises and international organizations,integrating them into more extensive networks.
This process also provides for high-level control of networks via Cyberoam devices and software.
Cyberoam also sells products designed for use in homes and small offices.
The second was shared with us by an ethical hacker who wished to remain anonymous.
He then discovered that Cyberoam devices support default passwords.

Timeline
First vulnerability discovered and resolved:Late 2019
2nd vulnerability reported to us by anon.
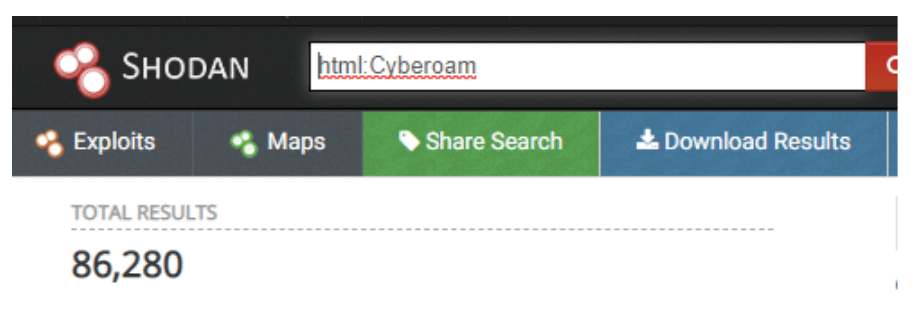
Using Shodan,we could easily filter the IP addresses of roughly 86,000 Cyberoam devices.
*Shodan is just one example of this jot down of search engine.

There are many more tools that provide a similar service without collecting user information.
This makes their users harder to track and more popular with criminal hackers.
This was thenbrought to our attention by a security researcher who wishes to remain anonymous.
Vulnerable and non-vulnerable Cyberoam devices automatically installed a regex-based important patch to fix the previous RCE.
However, this didnt make it any harder to exploit the second vulnerability.
Also,the regex patched used by the first fix would have been insufficient.
Once an attacker gains a shell, it’s usually game over.
Being the most severe form of RCE, it didnt need any authentication to exploit.
It alsoautomatically granted root privileges, was highly reliable, and relatively straightforward to exploit.
How Many Networks Were at Risk?
We cant say exactly but can give estimates.
At least 86,000 Cyberoam IP addresses are accessible via Shodan.
We outlined the nature of each issue, how we discovered them, and how they made networks vulnerable.
Sophos replied promptly and guaranteed the issues would be resolved ASAP.
Sophos hotfix completely disabled the vulnerability, and the firewall now requires user authentication at the login portal.
The hotfix will be included in the latest version of the relevant software, to be released soon.
All Cyberoam customers and partners are being notified to advise of the hotfix and the changes mentioned above.
They will also be advised to change their admin credentials from the defaults.

The products affected with these vulnerabilities are end-of-sale, meaning theyre no longer available for purchase.
They will reach end-of-life after the first quarter of 2022 at the latest.
If someone wanted to, they could haveeasily automated taking over all Cyberoam servers in a matter of minutes.
Had these vulnerabilities been discovered by criminal hackers, theimpact on networks affected could have been catastrophic.
This vulnerability has been resolved.
To learn more about data vulnerabilities and security in general,read our complete guide to online privacy.
We then alert the companies involved in the issue.
And that is what we did as soon as we were made aware of this bypass.
Sophos quickly replied, and the process to handle the issue started immediately.
These ethics meanwe also carry a responsibility to the public.
Cyberoam users must be aware of the previous vulnerabilities that impacted them, as well.
The purpose of our Research Lab is to helpmake the internet safer for all users.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
like, comment on how to improve this article.
