Carters was using Linc to create shortened URLs to travel purchases made on its online store.
But rare are these times.
We often need days of investigation before we understand whats at stake or whos leaking the data.

Some affected parties deny the facts, disregarding our research or playing down its impact.
So, we need to be thorough andmake sure everything we find is correct and accurate.
At this time, wed like to validate and assess impact to our customers.
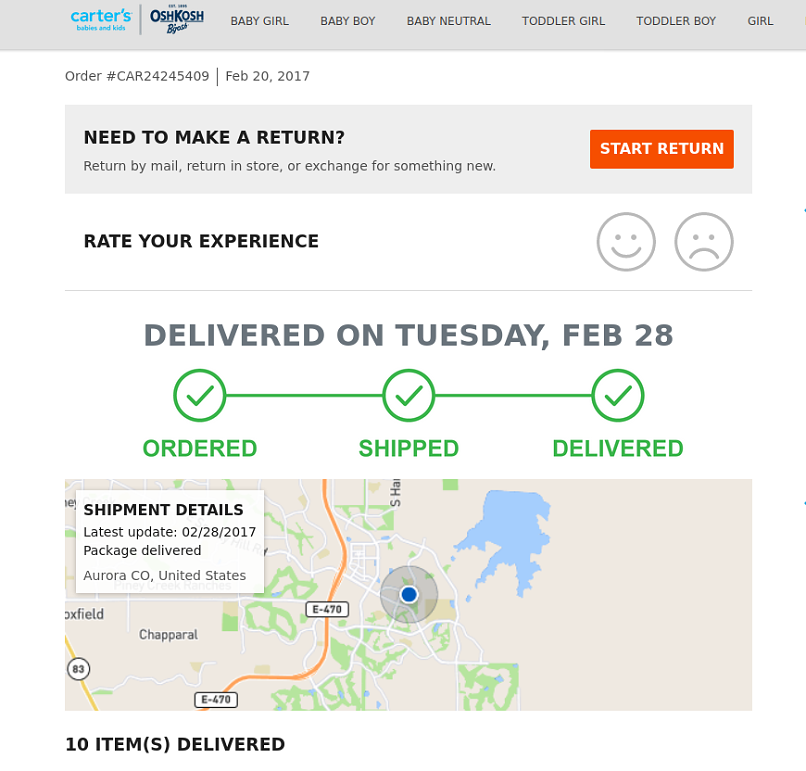
Carter’s delivery confirmation exposed in the data breach
Would you just send us the reproduction steps and more samples of PII data that were exposed?
We will reconvene internally as soon as I receive more information from you.
We hope they implemented the fix for future URL creation.

Carter’s delivery confirmation exposed in the data breach
Any company can replicate the same steps, no matter its size.
To learn about data vulnerabilities in general, read ourcomplete guide to online privacy.
They then examine each data store for any data being leaked.

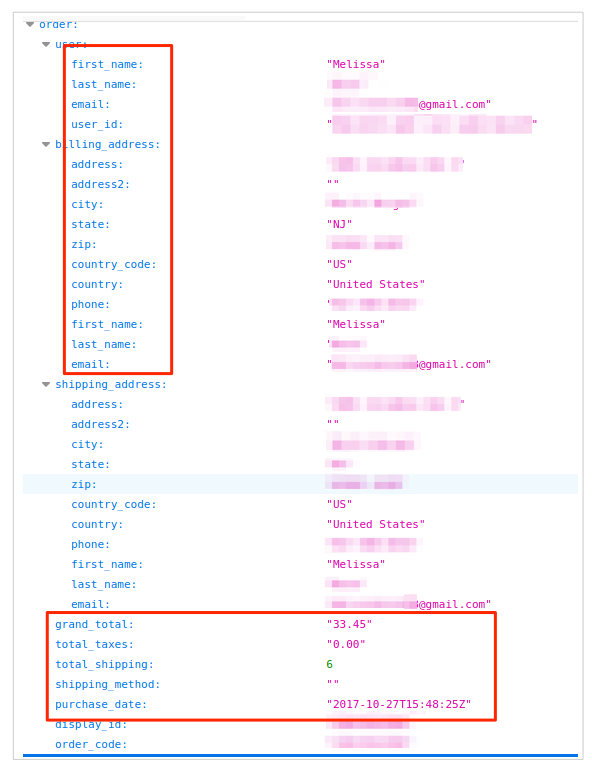
Our team was able to access this data because it was completely unsecured and unencrypted.
As ethical hackers, were obliged to inform a company when we discover flaws in their online security.
The purpose of this web mapping project is to helpmake the internet safer for all users.
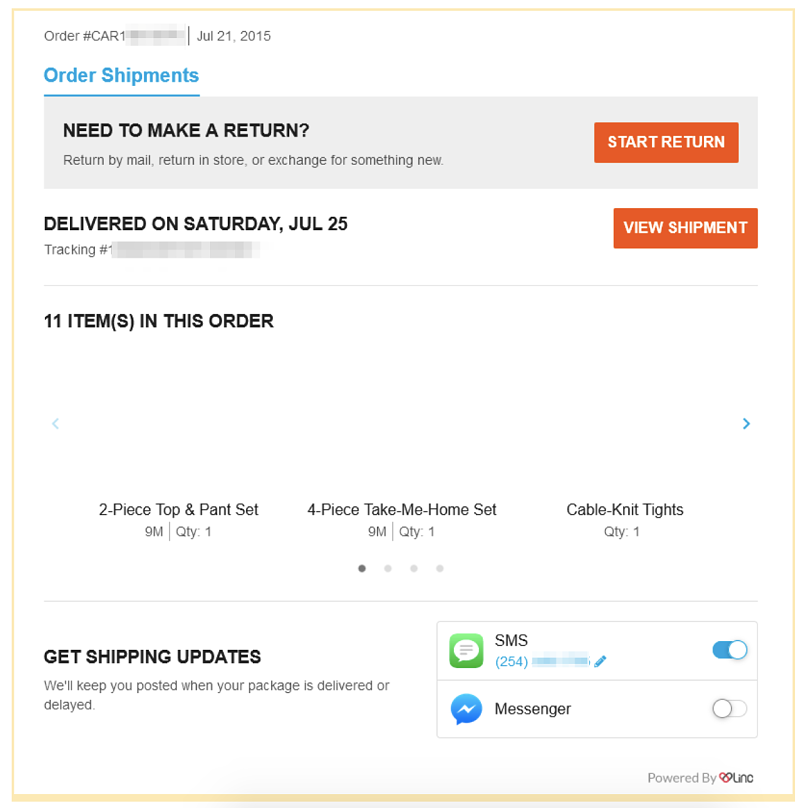
Wenever sell, store, or expose any informationwe encounter during our security research.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
You may also want to read ourVPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Check the Leak Box here »
kindly, comment on how to improve this article.



