The breached database containeddaily logs of user activity by customers of ISPs using web filtering software built by Conor.
It exposed all internet traffic and activity of these users,along with their PII data.
Understanding a breach and its potential impact takes careful attention and time.
We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact.
So, we need to be thorough and confirm everything we find is correct and true.
We then reached out to the company to offer our assistance.
Our team was able to access this database because it was completely unsecured and unencrypted.
In total, this resulted in 890+ GB of data andover 1 million records.

The database belonged to aproprietary software developed by Conor,rather than the ISPs themselves.
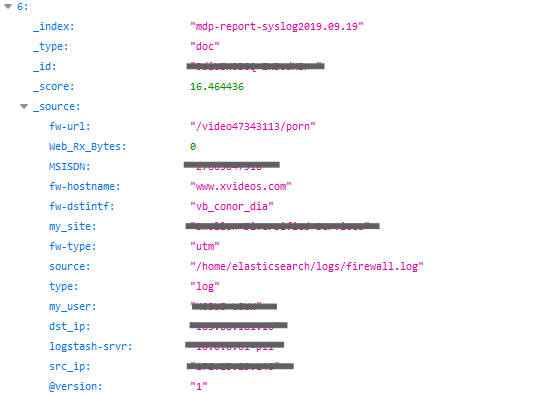
We found entries from users viewing porn for example, as well as their social media accounts.
We could also identify each user.

A person’s internet browsing is always personal and expected to be private.
However, that was not the case in this instance.
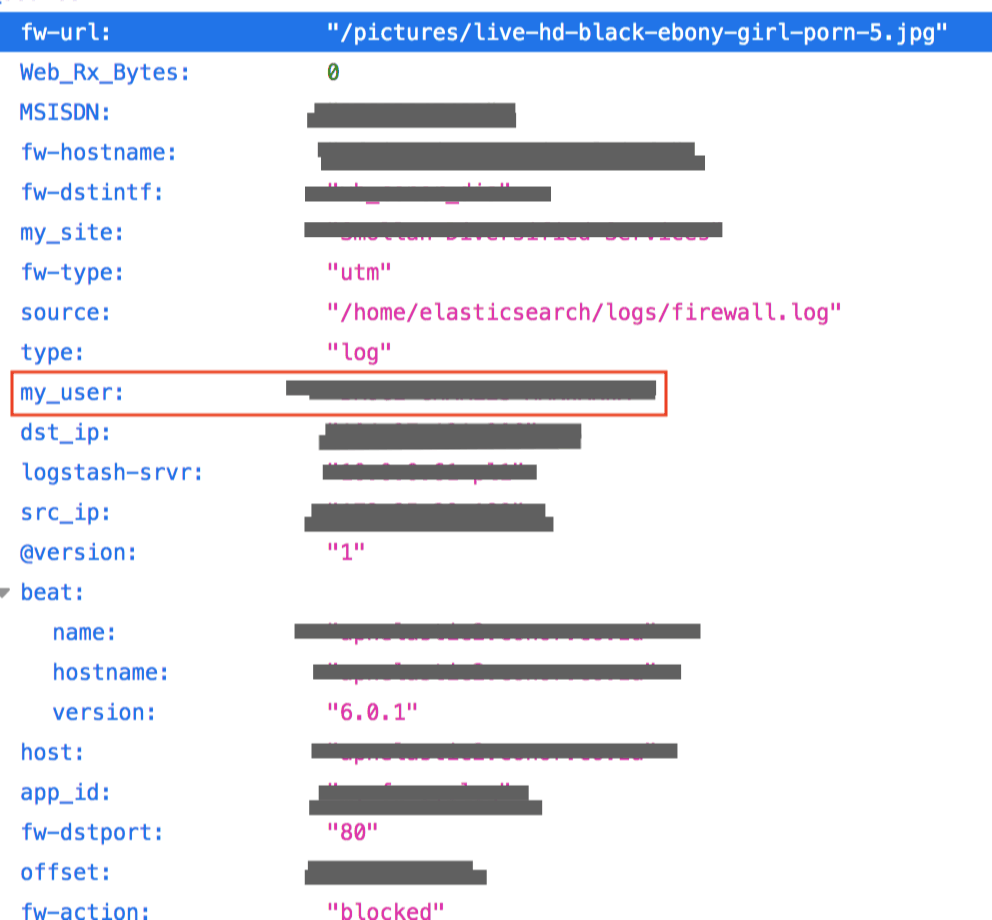
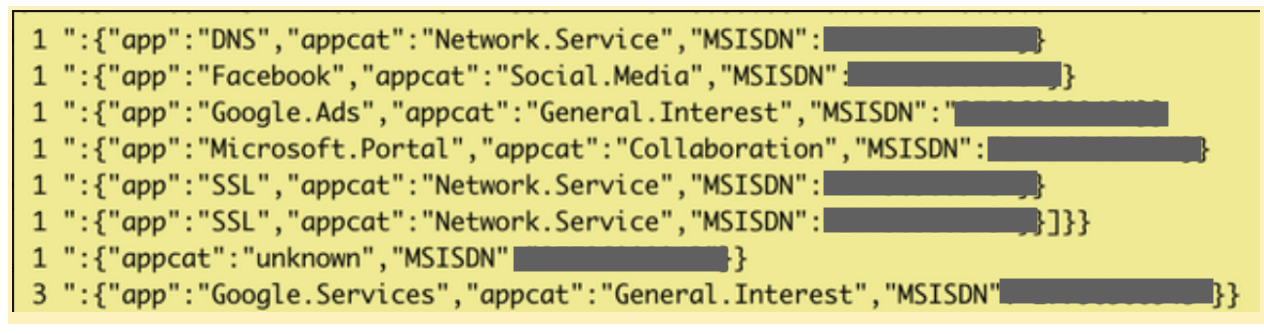
In another example, on the following record,a username is clearly visible.
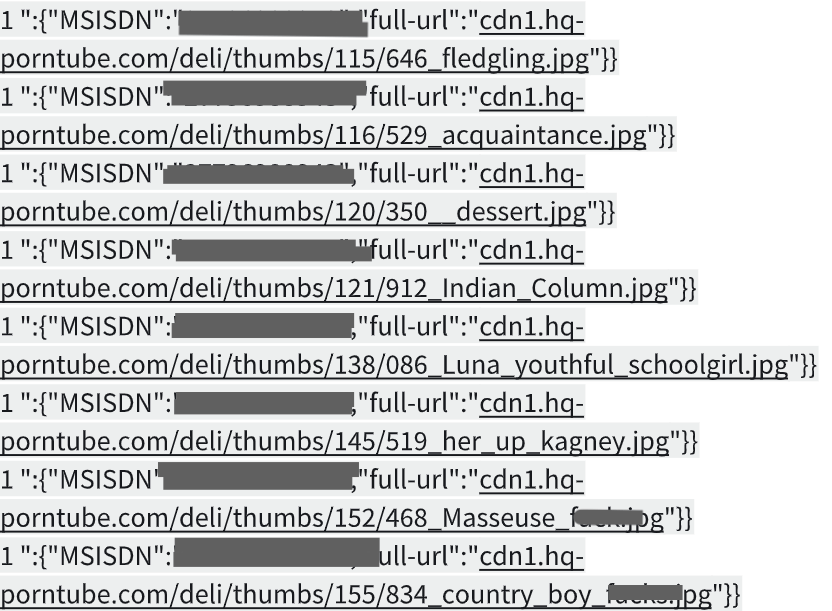
The breached database alsodivulged the workings of Conor’s web filter and its content blocking rules.
Individuals could exploit this knowledge to circumvent the filter, rendering it useless and obsolete.
Likewise, they could be vulnerable to loss of business or legal action.
The leak made them vulnerable to a wide range of online attacks and fraud.
These could havedevastating effects, both personally and financially.
Many people would be deeply embarrassed by their porn search history, and cybercriminals know this.

For Conor’s Clients
We recommend reassessing or auditing your in-house data security and privacy protocols.
The breached database contained logs of all a user’s internet activity.
It also hides your location and IP address, so hackers have almost no identifying information about you.
If you’re concerned about data security and vulnerabilities, read ourcomplete guide to online privacy.
Our researchers use port scanning to examine particular IP blocks and test open holes in systems for weaknesses.
They examine each hole for data being leaked.

When they find a data breach,they use expert techniques to verify the database’s identity.
We then alert the company to the breach.
If possible, we will also alert those affected by the breach.
Our team was able to access this database because it was completely unsecured and unencrypted.
Conor was using an Elasticsearch database, which is ordinarily not designed for URL use.
Users of Conor’s software must also be aware of a data breach that impacts them.
About Us and Previous Reports
vpnMentoris the world’s largest VPN review website.
You may also want to read ourVPN Leak Report and Data Privacy Stats Report.
[Publication date: 16.12.2019]
yo, comment on how to improve this article.
