Dalil is the biggest phone directory in Saudi Arabia.
96% of its users are in Saudi Arabia; the remainder are in Egypt and other Arab countries.
The appworks like Truecaller, helping users identify unknown numbers.

In theory, this offers protection against cold callers and other unwanted contact.
However, reality tells a different story.
As well as the program log, thisdatabase includes both harvested and voluntarily-submitted personal information.
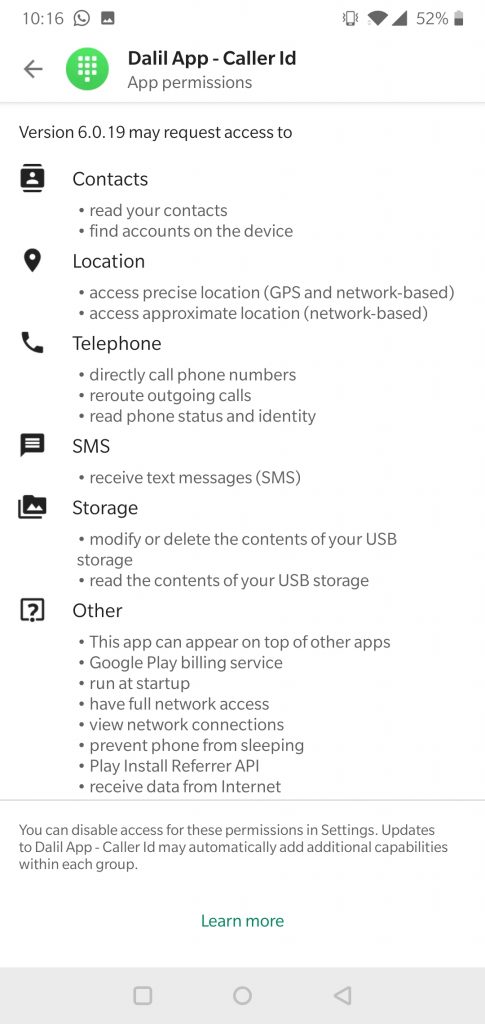
Our team found it: this means anyone else who wants to look for it could, too.
And while our hackers are not malicious, we cannot guarantee others' motivations.
Sample Profile
As demonstrated above, the app collects large amounts of information.

This allowed us tocreate a profile for one Dalil user from hacked data.
Firstly:targeted adware and malware.
This raises two red flags.

Firstly, the permissions allow the app to reroute calls.
Phone calls are automatically filtered through an allowed app, which allows Saudi officials to listen in.
The app also has permission to find accounts on the gadget.

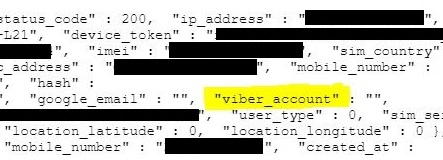
As shown in the user profile below, the app harvests information about users' Viber profiles.
Rakuten’s Viber is permitted in the Kingdom, meaningit’s susceptible to surveillance.
Additionally, the apppermissions allow access to the gadget’s stored media files and received text messages.
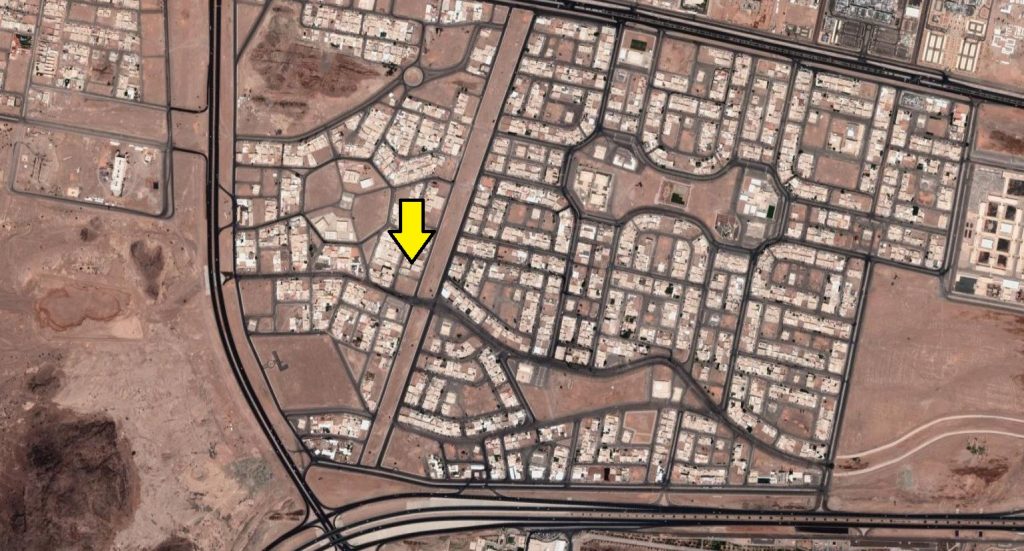
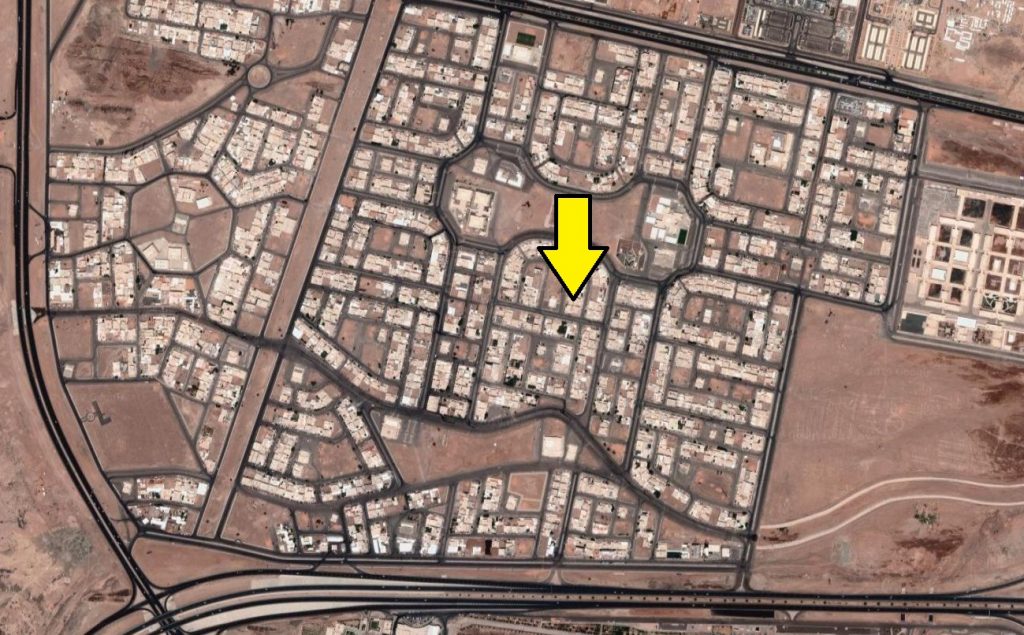
We discovered that theapp also records searches made through it.
The app’s location permissions mean that officials could trace the journalist (and their contact).
They could follow him to a meeting, listen to everything reported, and arrest him immediately.
Ethical Hacking and Conclusion
We discovered this breach as a result of a web mapping project.
Our hacker uses port scanning to examine particular IP blocks and test open holes in systems for weaknesses.
They examine each hole for data being leaked.
In this case,they installed the app and entered their own data.
This allowed them to confirm both that their data was leaked, and the identity of the database.
At the time of publication, we had not yet heard back from them.
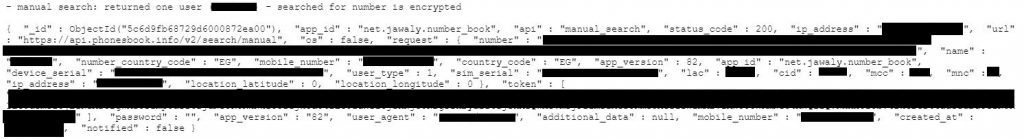
This observation indicates the presence of at least one malicious actor accessing Dalil’s user data.
We emphasize the utmost urgency for Dalil to take swift action and ensure the protection of their users.
The lesson here is clear:popularity does not equal trustworthiness.
Pleaseshare this report on Facebookortweet it.
like, comment on how to improve this article.






