What Is a Remote Access VPN and How Does It Work?
Their main aim, like all VPNs, is to secure your data.
In this setup, the remote user’s gear handles data encryption and decryption thats either sent or received.

Its the NAS that you, as a teleworker, interface with when using a remote access VPN.
With this configuration,the client software must also be installed on the off-site workers machine.
Its then transmitted to the VPN gateway that sits just outside the remote LAN.

Upon receipt, the VPN gateway decrypts the traffic and relays it to the LAN.
The Best Remote Access VPNs for 2025
1.
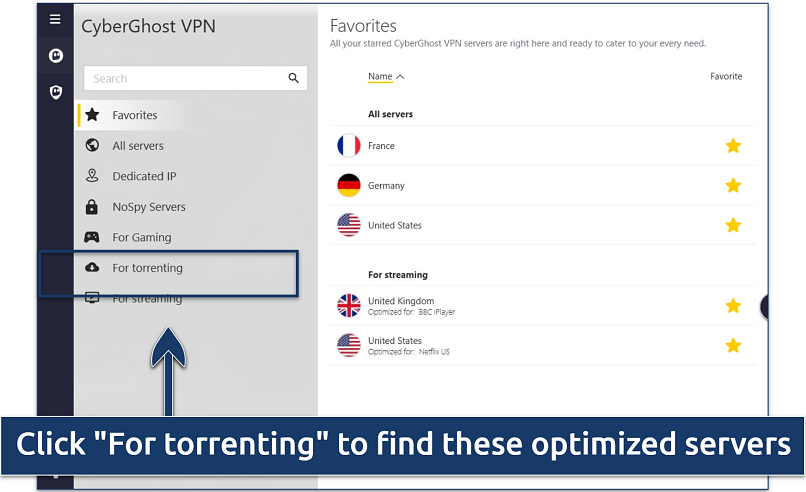
I never ran into any DNS/IP leaks testing CyberGhost’s servers.
The VPN also uses RAM-only servers and an audited no-logs policy to protect your information against online surveillance.
One minor con is the price of short-term plans with a limited refund period.
Getting a refund is easy if its not for you.
However, WireGuard was always the fastest during my tests.
While these customization options might be overwhelming to beginners, everything is pre-configured for online security.
What Is a Site-To-Site VPN and How Does It Work?
They use the public internet to extend your companys internet across multiple office locations.
This allows your company to share information with its partners, while still securing its LAN (intranet).
Below, Ill briefly walk you through the basics of these two VPN techniques.
Internet-Based VPN
The internet VPN methodcombines the companys existing web connection with public internet infrastructure.
Most internet-based site-to-site VPNs use IPSec (Internet Protocol Security)to secure traffic across the WAN.
If both LANs are already connected to the internet, why not use this connection?
Well, IPSec leverages the preexisting internet as the backbone of its encrypted communication.
This results in peak web link performance, ideal for delay-sensitive applications like VoIP (Voice over IP).
MPLS providers will guarantee that the security and performance demands of your business are met.
Furthermore,MPLS offers interface independence, meaning that each of your sites can have different connections(i.e.
T1, Fiber Optic, DSL) to the MPLS infrastructure.
Any compromises in speed and performance will largely go unnoticed.
Site-to-site VPNs allow multiple users traffic to flow through each VPN tunnel.
While a dedicated connection could be used for each lab, the connection demands (i.e.
fast upstream speeds) of each lab dont necessarily justify the very high cost of operating these connections.
Well-known VPN security protocols include OpenVPN, WireGuard, and IKEv2/IPsec.
There are several protocols that play critical roles in securing data transmissions.
Some providers are even offering in-house protocols.
What is the difference between a VPN, remote access VPN, and a site-to-site VPN?
What key aspects should organizations analyze to determine the most suitable VPN solution for them?
This comprehension will help you determine whether to prioritize accessibility for individual users or connections between entire networks.
You should also assess if the current data pipe setup will work with various VPN models.
To summarize, these are the best VPNs for remote work access…
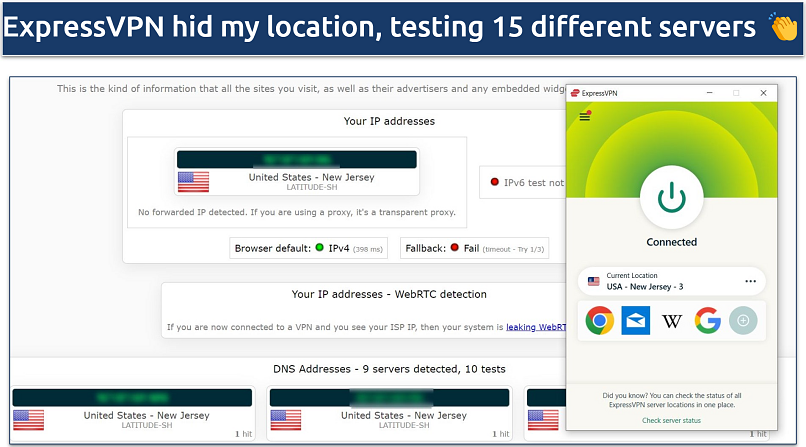
Your data is exposed to the websites you visit!
Visit ExpressVPN
c’mon, comment on how to improve this article.







