The internet breaks down the barriers of global connectivity, allowing people everywhere to connect instantly.
But with this tremendous benefit comes a downside: the dark reality of cyberstalking.
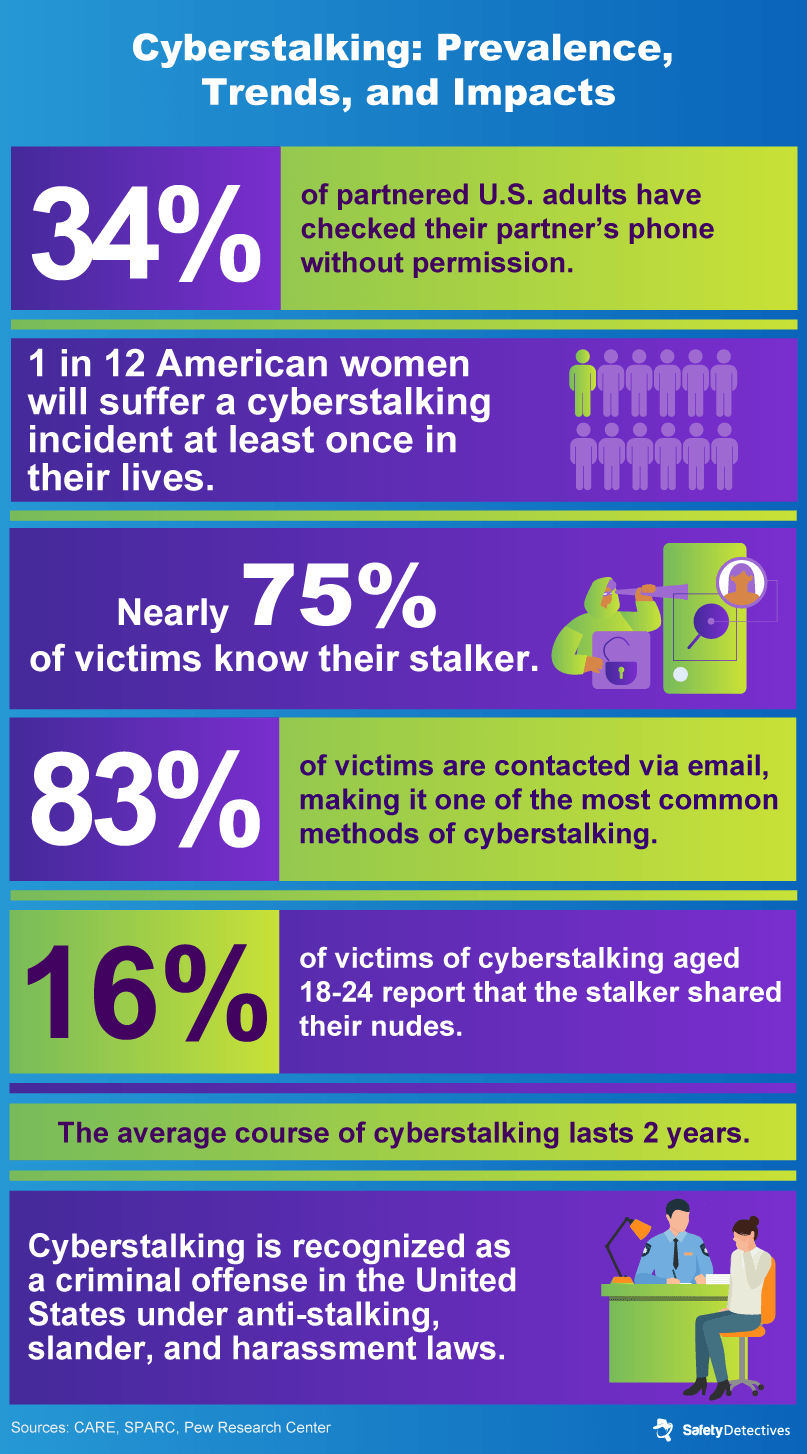
These victims often know their harassers, who may be ex-partners, acquaintances, or even family members.
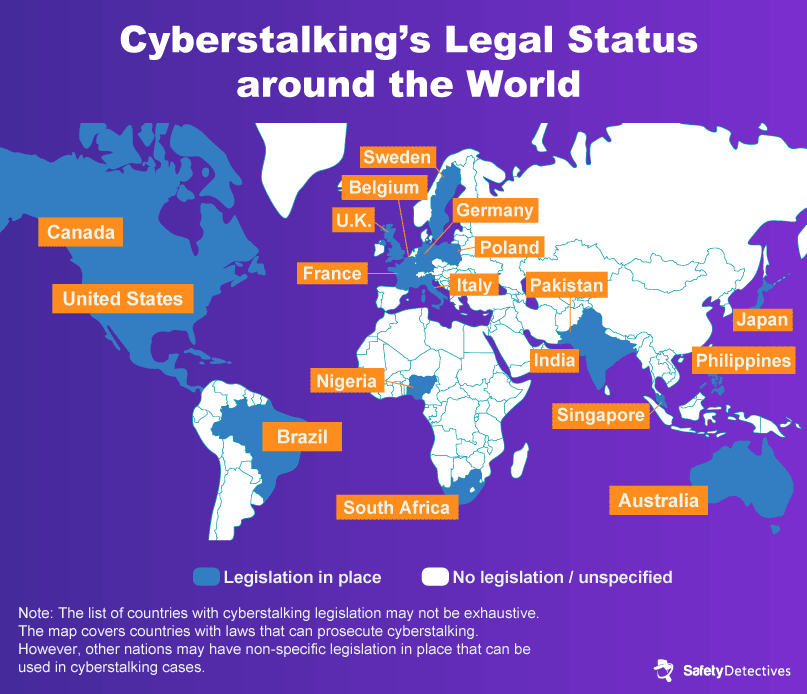
Cyberstalking laws vary, leaving victims unsure of how to keep themselves safe.
What Are the Motives behind Cyberstalking?
This creates a sense of detachment and anonymity, making it an attractive way to carry out such harassment.
A key in of cyberstalkingcalled partner surveillancealso occurs within relationships.
Have you ever heard of a friend or acquaintance who monitors their partners digital activities?
The goal is to track their movements, gather information, or maintain the upper hand in the relationship.
Where Is Cyberstalking Illegal?
Cyberstalking laws vary widely across the globe.
In the United States, Australia, and Poland, cyberstalking is recognized as a criminal offense.

However, cyberstalking is not explicitly illegal in much of Europe, Russia, or China.
The individual sent public tweets and threatening messages directly to the publishing company via Twitter.
Example #2:A Texas man cyberstalked a woman who wouldnt date him.
After more than half a year, the situation escalated to the sending of death threats through these accounts.
He also posted her name, address, and other sensitive information online.
These cases highlight the importance of having legal measures in place to protect individuals from this threat.
These abusive behaviors serve as tools to exert control, instill fear, and cause harm to the victim.
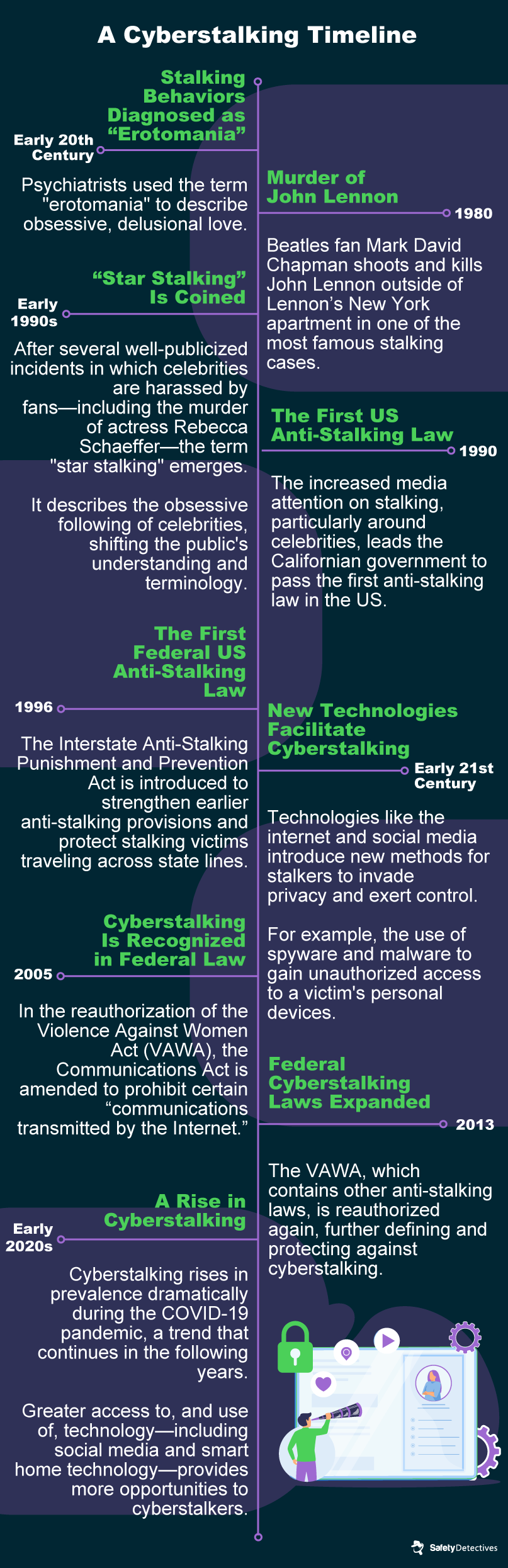
During this time, high-profile celebrities including Madonna and Steven Spielberg were stalked and threatened.
In extreme cases, celebritiesincluding John Lennon, Rebecca Schaeffer, and Monica Seleswere even attacked.
The high-profile nature of these victims helped amplify the need for anti-stalking legislation.
Eventually enacted in all 50 states, the first anti-stalking law was passed in California in 1990.
Balance your need for online visibility with the importance of personal safety.
Many of these updates are specifically designed to address and patch security vulnerabilities that have been discovered.
Keeping your software up to date means that youre equipped with the latest defenses against emerging cyber threats.
Mobile devices are also at risk.
see to it that your smartphones operating system and all apps are up-to-date.
Heres how you’re free to manage this:
4.
Be Wary of Public Wi-Fi
Using public Wi-Fi networks can be a risk factor.
Public Wi-Fi networks are generally less secure than those that are private.
They often lack strong encryption, making it easier for hackers to intercept the data you send and receive.
This can include personal information like passwords, credit card numbers, and other sensitive data.
A safer alternative to using public Wi-Fi is to rely on your phones data connection.
Essentially, a VPN creates a secure, encrypted connection between your unit and the internet.
One of the key benefits of using a VPN is that it hides your IP address.
Most social media platforms provide a feature that lets you view your account as it appears to the public.
Using this feature, you’re able to adjust your privacy parameters effectively.
Set your posts to be visible to friends only or a similarly restricted setting.
Using strong passwords and regularly updating them is equally important.
A strong password should be complex and unique.
They should be difficult to guess and different for each of your accounts.
Clean Up Your Digital Footprint
Your digital footprint comprises all the information about you thats available online.
Each piece of information contributes to the overall picture of your online presence.
This step is crucial for several reasons.
First, it tells the stalker in no uncertain terms that their attention is unwelcome and must stop immediately.
However, understand that in many cases sending this message may not stop the cyberstalker.
Cyberstalkers are often driven by compulsions.
Youll need to clarify your expectations regarding privacy and respect in your shared space.
Understand that the cyberstalkers goal is often to provoke a response from you.
It may also give them more information and emotional leverage to use against you.
Document Everything
Meticulously document each instance of harassment.
This means keeping copies of all interactions, whether through screenshots or printed pages.
Be sure to capture the messages and profile pages, including usernames, from which the abuse originated.
This thorough documentation should extend beyond online interactions.
The importance of this step lies in its utility for legal and protective action.
In addition, keeping your own records helps ensure that you have an unalterable history of events.
Block Your Stalker
Use the blocking feature offered by social media platforms.
Blocking is an easy way to enforce your boundaries and make it harder for the stalker to reach you.
However, understand that this measure has its limitations.
Despite these challenges, blocking remains an essential step.
For more detailed guidance on how to use these features effectively, like visit oursection on blocking strategies.
Here youll find step-by-step instructions and tips to maximize the effectiveness of these tools in your fight against cyberstalking.
Your equipment may be compromised or monitored by the stalker, particularly if they are a partner or housemate.
Instead, use a computer that the stalker cant access.
You should also disable text and email notifications to your phone, tablet, and other devices.
When notifications pop up on your screen, they can reveal sensitive information or private conversations to the abuser.
This action creates a significant barrier, cutting off the line of communication the stalker has been exploiting.
When adopting this strategy, exercise caution in sharing your new contact details.
The act of reporting is a crucial step in itself.
To report cyberstalking, contact your local law enforcement agency.
Initiating this contact is the first step in what could become an official investigation.
Understand that filing a report does not automatically guarantee an investigation or result in charges being filed.
However, its a necessary and valuable step.
Even if reporting the cyberstalking doesnt lead to immediate results, the process is still beneficial.
Having a copy of the police report can be an important piece of evidence.
Setting boundaries in such situations is difficult and can take an emotional toll.
In these times, professional help can be incredibly beneficial.
Moreover, therapy can offer much-needed guidance through the process of recovery and healing.
This legal document serves as a formal directive, legally prohibiting the stalker from contacting or approaching you.
Its an enforceable measure that adds a layer of legal protection.
Obtaining a restraining order can also play a crucial role if your case proceeds to prosecution.
It demonstrates to investigators and the legal system that there is a recognized threat that requires intervention.
Additionally, a restraining order may effectively deter the stalker from continuing their behavior.
For many stalkers, the realization that their actions have legal consequences can be a significant deterrent.
This can protect not just you, but also other users who might be exposed to such content.
By reporting abusive behavior, users contribute to the enforcement of the platforms community standards.
In addition, blocking allows individuals to protect their mental health by limiting exposure to harmful interactions.
But the question remains: Are these tools enough?
Helplines and resources dedicated to this issue provide essential support, advice, and intervention options.
FAQs
1.
It can include monitoring someones online activities, sending threatening messages, or sharing personal information without consent.
Its a form of cyberbullying that can lead to psychological harm and poses a serious privacy concern.
What Are the Different Types of Cyberstalking?
What Laws Protect Me from Cyberstalkers?
Laws protecting against cyberstalking vary by region:
4.
How Do I Stop Someone from Cyberstalking Me?
What Should I Do to Prevent Cyberstalking?
This knowledge is key to ensuring your personal protection online.
Tech companies also bear a responsibility to continually update and strengthen their data protection measures.
As users, we rely on these companies to safeguard our information and provide secure digital environments.