Unfortunately, this includes a few of the most popular security extensions available in the Add-on catalog.
What is a Reuse Attack?
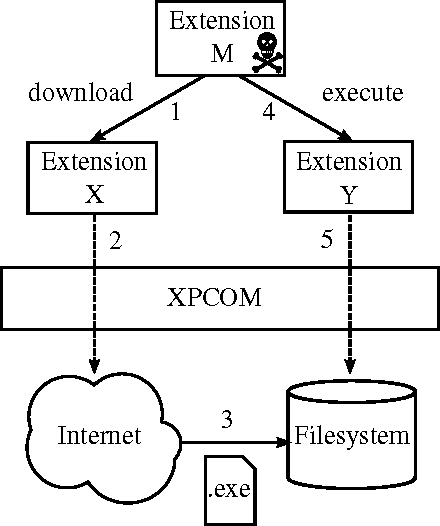
The hidden code within the attacking add-on would then execute without the users knowledge.

The attacks are made possible because legacy Firefox frameworks do not isolate add-on functions.
Are Reuse Attacks Common?
The researchers told vpnMentor that many other news outlets have blown the issue out of proportion.
Credit: Buyukkayhan et al.
Of course, that would not be a sensible reaction to the issue at hand.
In fact, a main point of the research was to prove the inadequacies of current add-on vetting practices.
It was harmless, but it showed how an attack could occur.

Credit: Buyukkayhan et al.
Are Jetpack Add-ons Susceptible?
What Security Extensions Are Vulnerable to Reuse Attacks?
Available to PC users only, it has been downloaded more than 59,000 times.

Note:the researchers tested 323 random extensions along with the ones on the top-10 list.
This random sample may include more security extensions than the ones listed here.
Did Any Security Extensions Pass the Vulnerability Test?
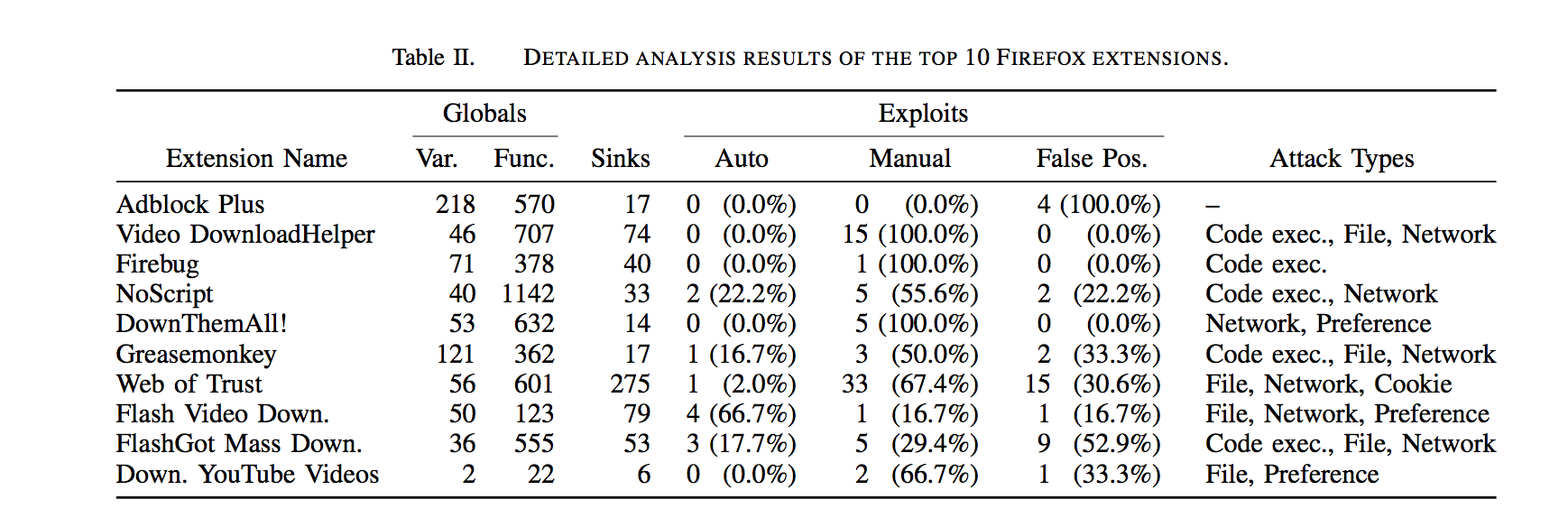
Adblock Plus came through without any reuse vulnerabilities.
This is a positive development for the 20+ million users who have downloaded this extension.
What Are the Best Ways to Prevent Reuse Attacks?

Moreover, extensions that boast robust programming and receive regular updates are less susceptible to such vulnerabilities.
The team is also moving the CrossFire project to GitHub.
Developers would then be able to issue updates to fix the faults.

Is a Universal Fix Being Developed?
Also, whenMozillas Electrolysis Projectlaunches later this year, extensions will be isolated via sandboxing.
This shift will prevent any malicious extension from communicating with a vulnerable one.

Your data is exposed to the websites you visit!
Visit ExpressVPN
just, comment on how to improve this article.








