Most VPNs offer both protocols, allowing you to personalize the security options.
Only the VPN host can decrypt it and relay it to the end user (recipient).
So your sensitive information is well protected from snoops.
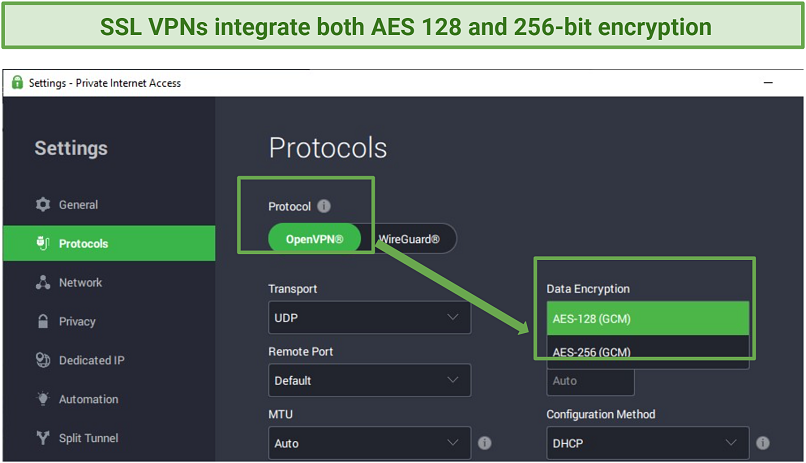
AES 256-bit encryption provides the best possible protection for IPsec and SSL VPNs like PIA
There are 2 modes of securing data transport and tunnel.
As such,IPsec offers high data confidentiality and integrity between the sender and receiver.
It also supports online grid-level peer authentication, data origin authentication, and replay protection.

AES 256-bit encryption provides the best possible protection for IPsec and SSL VPNs like PIA
For example, IPsec can be used between 2 routers to create a site-to-site VPN.
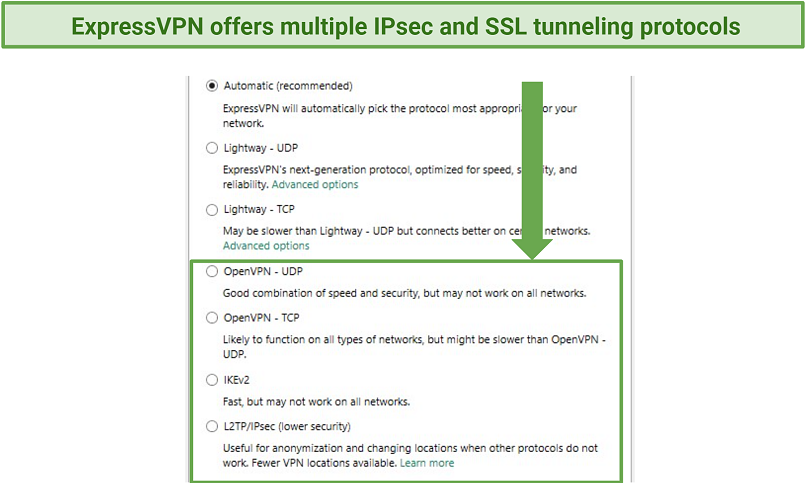
VPNs deploy IPsec-based protocols like IKEv2, L2TP/IPsec, and SSTP for secure traffic tunneling.
SSL solutions came later, in 1999. surfing app-based protocols provide safe end-to-end tunneling whenever remote users access web applications and client-server apps.

For example, when you want to access an online payment website on your net online gate.
The most popular protocol that uses SSL encryption is OpenVPN (OpenSSL library).
It supports both UDP and TCP.
The web app must perform a successful TLS handshake with an SSL gateway server to initiate a communication channel.
Contrary to IPsec, TLS is incorporated by default in web browsers and many other applications.
There are 2 different types of SSL VPNs.
SSL Tunnel VPNs allow access to multiple sites (also the ones that arent web-based) through 1 port.
The software is automatically upgraded on the server and doesnt require user interaction.
Let’s look closely at how these 2 perform and what their pros and cons are.

Here is how the IPsec and SSL VPNs compare to each other.
SSL operates at the transport layer and doesn’t inspect IP packets.
The IPsec encryption is more resistant to DoS attacksthan SSL/TLS because it operates at the lower online grid layer.
It makes this protocol more vulnerable to worm and Trojan attacks.
However, if attackers gain access to the pre-shared key, they can eavesdrop on the information.
Also, SSL uses the lower DES 128-bit cipher key encryption by default.
Hackers may exploit these vulnerabilities and carry out man-in-the-middle (MITM) attacks on SSL VPNs.
Thats why most SSL services integrate AES 256-bit encryption, besides 128-bit, to increase security.
They require frequent updating and patching so hackers can easily exploit it.
Bypassing Firewalls
Public online grid firewalls block threats by filtering out data packets traveling without port numbers.
IPsec VPNs don’t transport encrypted ESP packets with assigned port numbers.
Firewalls can quickly flag down and block them.
The commonly used UDP port number is 4500, but it may not be recognized on most private networks.
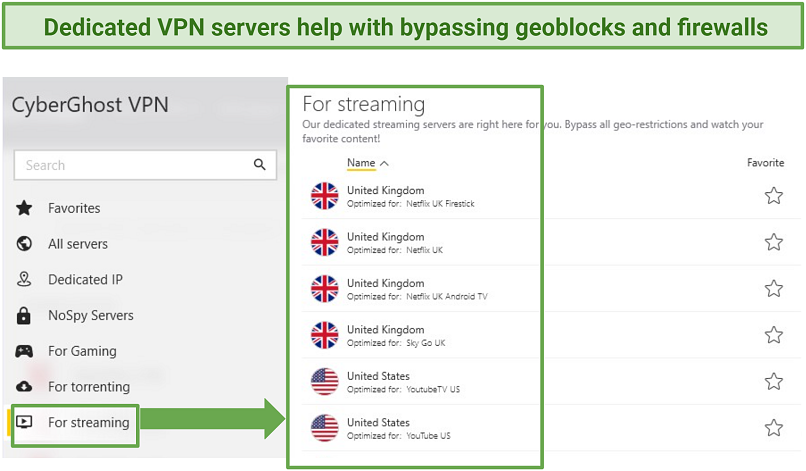
In short,an SSL VPN is better for bypassing firewalls and geoblocks.
However, most VPNs nowadays offer obfuscated servers that hide your traffic from detection.
Others provide optimized servers for bypassing geoblocks on various content platforms, regardless of the protocol you use.
So, an IPsec VPN might be as effective as an SSL one.
On the other hand, SSL protocols are designed to offer safe connections to web-based applications and services.
The IKEv2/IPsec protocol can be relatively faster than SSL protocols.
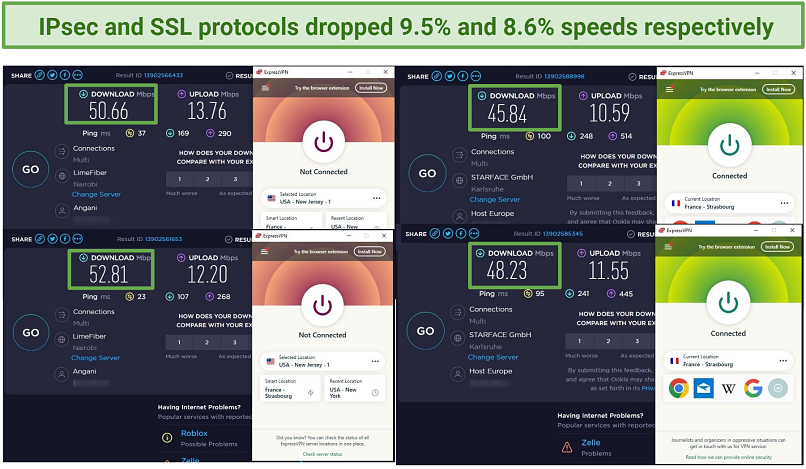
When I did online speed tests, there wasnt any significant difference between the IPsec and SSL protocols.
Most internet-enabled devices already have client software for connecting to an SSL VPN.
Special hardware may be required in large web connection operations.
It can be costly to set up and administer the software through regular updates.
All in all,an SSL VPN is much easier to deploy and more low-maintenance than IPsec.
IPsec might have shortcomings where SSL works better, and vice versa each has pros and cons.
Military-grade encryption also scrambles your data to safeguard you from hackers and snoops.
This authentication is an excellent protection against man-in-the-middle attacks that aim to intercept users data.
Plus, IPv6/DNS leak protection feature masks your actual location.
My personal details didnt show during the leak tests using both IPsec and SSL protocols.
It allowed me to stream buffer-free UHD content and play online games lag-free.
All servers are obfuscated, which helps to hide your traffic from detection by firewalls.
The data pipe is vast, spanning 105 countries, so its easy to bypass geo-blocks.
I used the VPN to access my Netflix US account content while traveling abroad without issues.
Besides, the VPN can be used on up to 8 devices simultaneously.
A minor con of the VPN is its pricey plans.
The subscriptions start at$4.99/month.
Luckily,ExpressVPN frequently offers generous discounts.
I got61% off and 3 months for free when I purchased the 12-month plan.
Other security and privacy tools include a kill switch and IP/DNS leak protection.
There are optimized servers for streaming, gaming, and torrenting.
Sothe VPN is ideal for high-bandwidth activities.
The server web link spans 100 countries, allowing you to easily access geo-blocked content.

The additional WireGuard protocol also provides a good balance of speed and safety.
Configuring the VPNs protocols is hassle-free on any operating system because of the intuitive design.
Plus, 24/7 live chat is in place if you ever get stuck.

However,long-term subscriptions are very affordable, starting at just$2.03/month.
They also have extended refund periods.
I recommend the 2-year plan as it’s the most pocket-friendly.

you could try CyberGhost for free, thanks to a tried-and-tested 45-day money-back guarantee.
Among the supported IPsec and SSL protocols are IKEv2 and OpenVPN.
I ran several leak tests on PIAs US servers, and my actual location wasnt revealed.

The kill switch also prevents your IP address from getting exposed, even on unstable internet connections.
There’s a no-logs policy too, so your data can’t end up in the wrong hands.
Just like CyberGhost,PIA offers ample global servers.

If youre new to VPNs, the many customization configs of PIA can be quite tricky.
However, the default mode is preconfigured, so you don’t have to tweak anything yourself.
There’s also 24/7 live chat support to get assistance at any time.

Longer plans, like the 3-year option, offer the best value for money in the long run.
So,the best VPNs provide both SSL and IPsec protocols to meet your different needs.
To choose the better VPN for yourself, check which one offers faster speeds or more secure connections.

Is IPsec faster than SSL?
Your VPNs performance may also be affected by several other things, like server congestion and unstable connections.
Can SSL VPNs hide my IP address?
you’re able to try such VPNs with confidence because theyre backed by trustworthy money-back guarantees.
What are the pros and cons of IPsec and SSL?
SSL is much easier to implement but doesnt offer extra safety features.
However, SSL might be better at bypassing firewalls, especially on router devices.
IPSec-based VPN protocols lack the open source code, which might be an issue for some users.
According to Edward Snowdens allegations, the NSA targeted IPsec with vulnerabilities that spies and hackers can exploit.
However, VPNs come with other security and privacy features to keep your sensitive data hidden from snoops.
When should I use IPsec vs. SSL?
you’ve got the option to safely use public WiFi or stream with no buffering.
Many remote workers and employers need a VPN to access a company’s data pipe.
It can be set up by a managed service provider (MSP).
Thats because SSL VPNs work by accessing specific applications, not the entire internet.
Access control ensures only the right people can see sensitive information.
So its great for clients and freelance employees.
IPsec is a better option for remote office team members who need full access to company resources.
The servers are obfuscated too, allowing you to bypass geo-blocks and get around firewalls.
Visit ExpressVPN
c’mon, comment on how to improve this article.

