My duties included responding to these attacks, forensics, malware analysis and so on.
Included in these extremely stealthy attacks are fileless malware and in-memory attacks.
What is fileless code/malware?
Fileless attacks are quite complex.
When someone sends you a file, you will see it on your desktop and your disk.
What technology have you developed to protect against these stealthy attacks?
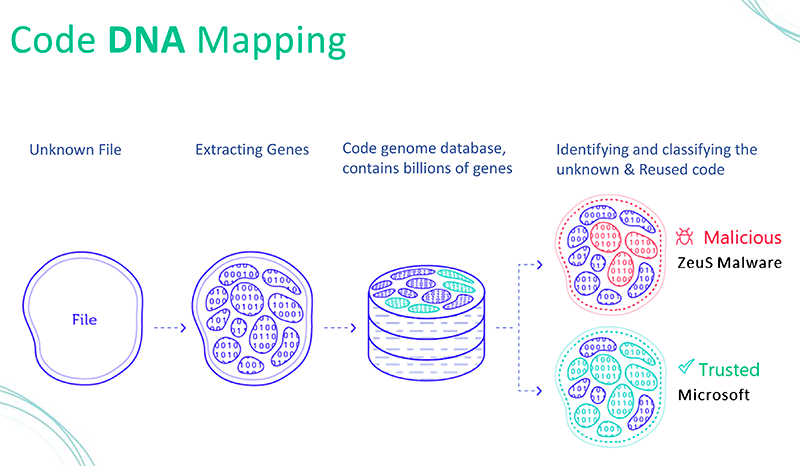
What are the advantages of being able to identify the source of the malicious code?
Secondly, it can help you understand what you are dealing with.
You know, the amazing thing is that everybody reuses code.

Even when Microsoft creates a new product, they reuse code.
So,software really is evolutionary in both legitimate and malicious cases.
Are you then able to identify Zero Day Attacks?

You cant really throw tens of years development into the trash and start from scratch every time.
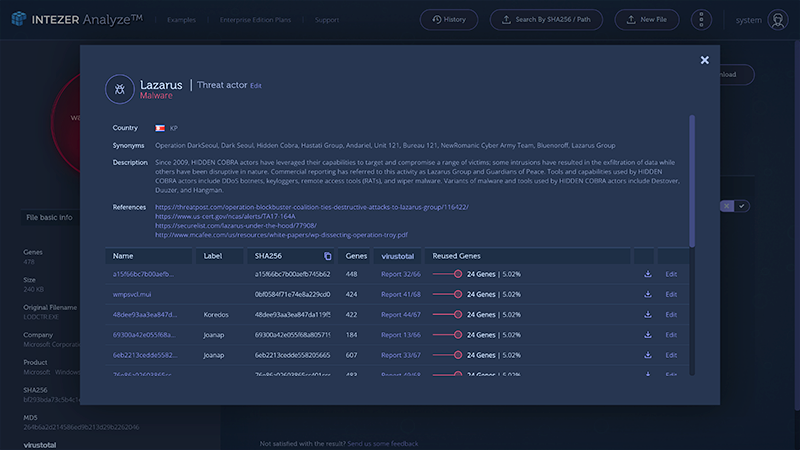
Detecting WannaCry though malicious reused code is our innovation here.
That’s a great question!
So, this scenario is very, very unlikely.
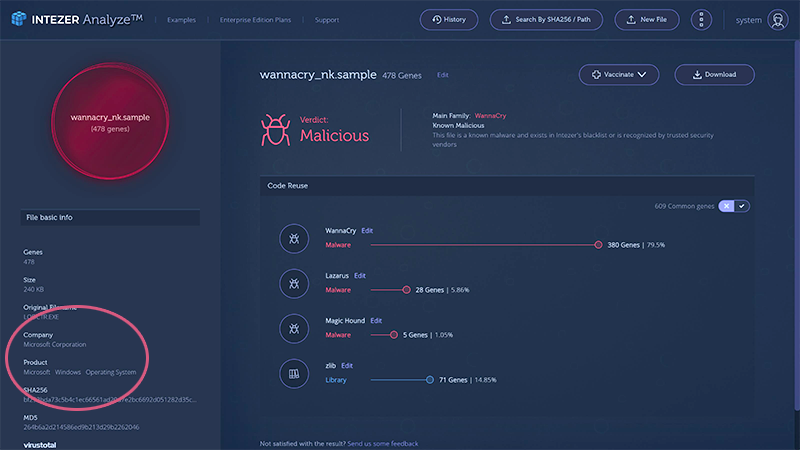
Can you show us an example of Intezer AnalyzeTMs DNA mapping in action?
This instance involves a dubious file, which purports to be a Windows file.
Clickherefor an interactive demo.
The right-hand side of the screen is where the magic happens, and the DNA mapping takes place.
That tells us right away that this cannot be a Windows file.
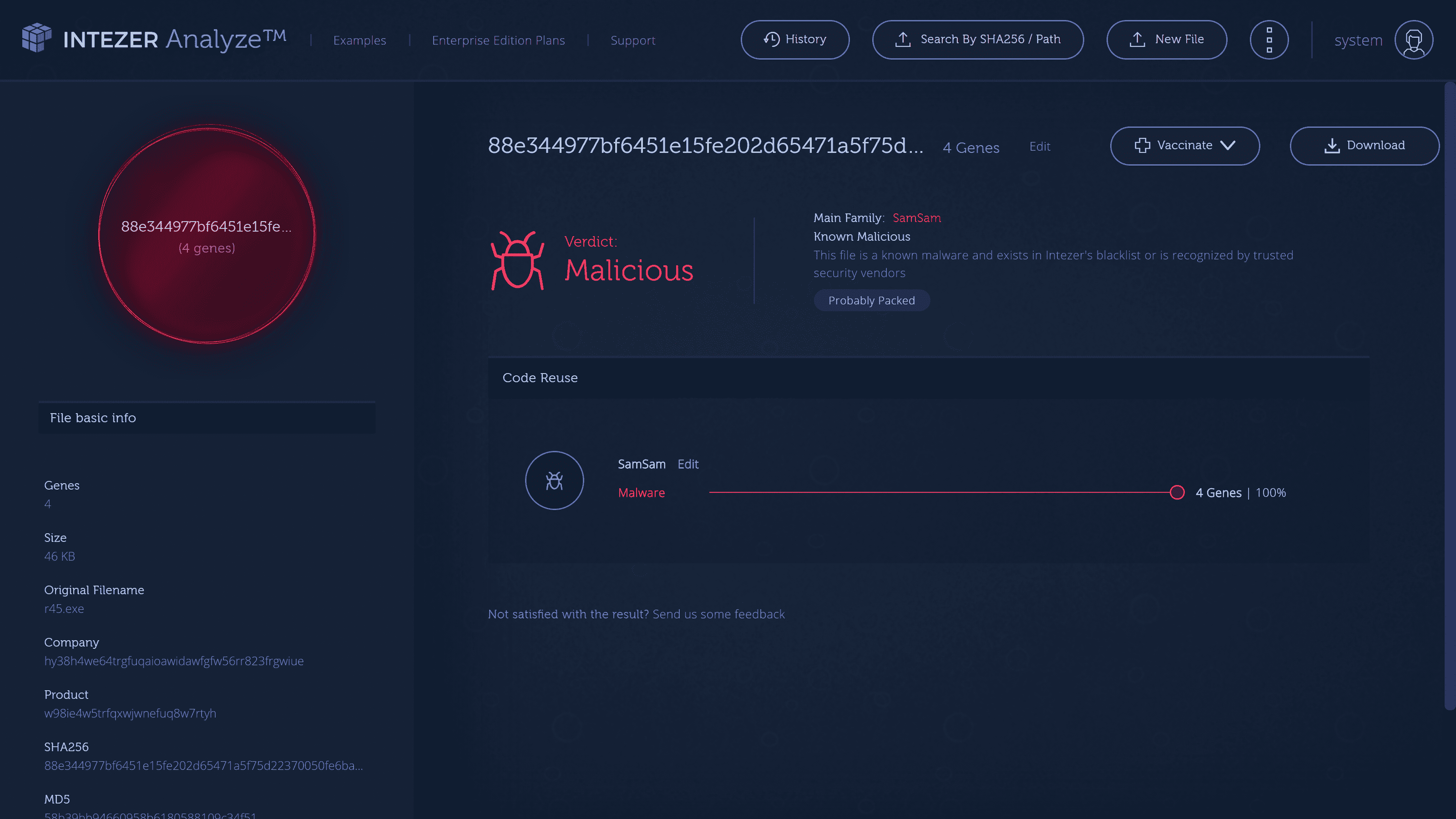
How does Intezer AnalyzeTM reduce false positives when detecting malware?
Do you have any insight into the source of the ransomware attack on Atlanta back in March?
kindly, comment on how to improve this article.




