Related
Most of us will agree that we are paranoid about email security and hack attacks.
We should equally be concerned about the other popular connection gear we use - the humble instant messenger.
It is also open to some of the privacy risks we associate with emails.
Especially in a business environment, unsecured IM installations are creating backdoors for hack attacks.
Spam, worms, Trojans and viruses are familiar email foes.
They are no friends of instant messaging either.
So how do we pick our friends from our foes?
Perhaps by following what Benjamin Franklin said -Distrust and caution are the parents of security.
Also, by putting these10 habitsin place.
Every IM client asks you to create a screen name.
A screen name usually refers to your email ID.
Create a screen name which does not touch upon personal information or your real identity.

For instance, my screen name is " Braniac' and not " Saikat'.
And NEVER provide any personal details including credit card numbers and social security number over the internet.
Always vet your contact list with people whom you know something about.
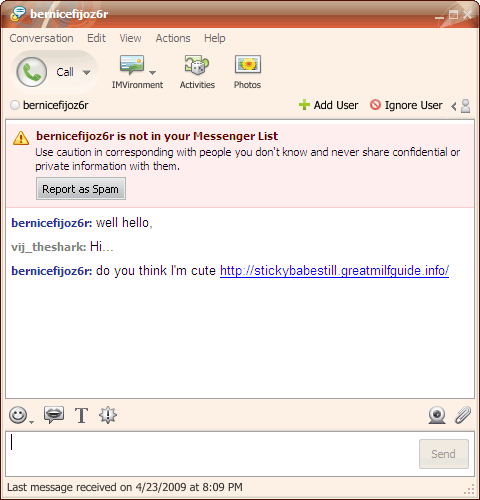
Anonymous at the other end of space may be fraught with risk.
It is possible to discover your gear address (i.e.
your IP) from an instant message and that usually is the first requirement for a remote hack attack.
Don’t believe everything you read and always verify any information or request for information.
A link tempts you to click it just for the lark.
A lot of these links take you to websites which can install spyware stealthily on your rig.
Viruses and worms with colorful names such as W32.Yalove or W32/Spybot-MQ are potential threats to Yahoo users.
An IM client like Yahoo allows P2P file sharing.
Do not share unknown content even if the person is known.
P2P files, like email attachments can carry viruses, Trojan horses, and worms.
They are engineered to seed themselves to other members on your buddy list.
Be especially cautious when someone sends you an .exe or a .zip file.
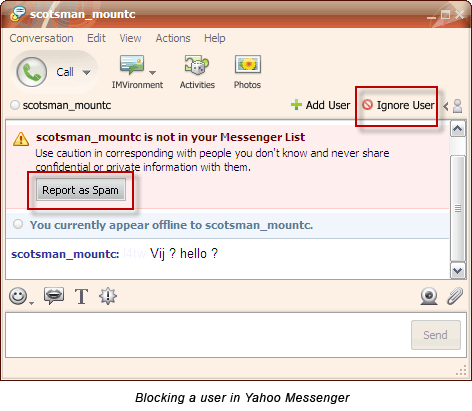
Yahoo has anIgnore userorReport as spamso that he can’t disturb you once again.
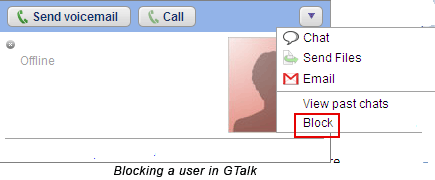
GTalk has aBlockuser option.
Using this option allows you to keep out the unwanted from repeatedly messaging you.
The default security tweaks in chat software tend to be relatively lax.
Thus making you open to attacks.
Check the parameters and preferences of your chat client to apply stricter permission controls.
Most IM clients lack encryption features.
Passwords are also a security loophole with hardly any client using strong password encryption.
The subject of encryption and strong password protection would require another post by itself.
So I hand you over to Tim’s excellent post onHow To Secure & Encrypt Your Instant Messaging Chats.
Here at MakeUseOf.com we have a lot of posts tagged as " passwords'.
Why not take a look at ways to set strong passwords.
IM client companies spend a lot of effort behind doors to prevent backdoor threats.
Newer versions come with bug fixes and enhanced security.
So, always patch your IM client as soon as one becomes available.
It is safer and advisable to always download from the IM client websites themselves or from verified sources.
It is an oft repeated habit to punch the[X]button and exit.
But this action does not close our IM client completely.
Especially in public computers be mindful of logging out and exiting completely.
Also, never press anyRemember My Passwordcheckbox during log-in as an added safeguard.
For Yahoo Users:Before you get up, delete your Yahoo Messenger profile.
It is located by default atC:\Program Files\Yahoo!\Messenger\Profiles.
Sometimes we will click a link; sometimes we will download a file.
These three not only protect us from IM attacks but they are the must-haves for any system.
Check out our recommendations for security programs in our article aboutEssential Security Downloads.
Chatting as against emailing is a real time activity.
It is in that sense more social than any other form of web communication.
The danger is that chatting can lull us into a false sense of security.
Just a few fundamental forethoughts help us to turn that false sense into a more conscious sense of security.
Have you been hacked?
Perhaps, you share the concern for a rigorous defense against hackers?
Let us know what safety measures you personally use"