By doing so, it prevents hackers, prying eyes and even your ISP from intercepting your online activity.
However, unlike other browsers, Tor can also access hidden .onion sites found on the dark web.
Its possible to accidentally download malware and viruses, plus there are plenty of scams.

This is why the dark web has a murky reputation.
Its critics portray it as a place for illegal activity where criminals can communicate secretly.
There are certain limitations to accessing the dark web and some activities you should avoid while using Tor.
As your traffic travels through Tor’s nodes, it slows your connection — which is why it’s helpful to use a fast VPN
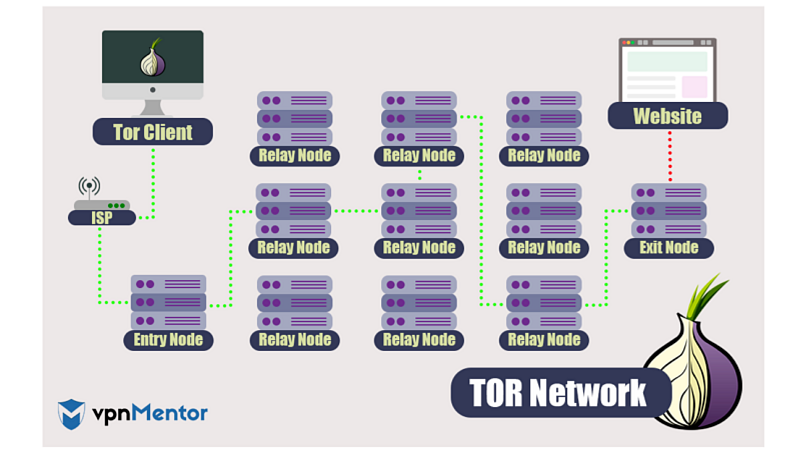
How Does Tor Work?
Nodes are scattered globally and give each other just enough information to reveal the next destination.
None of the nodes can see your traffic’s entire route, which is how Tor offers privacy.

As your traffic travels through Tor’s nodes, it slows your connection — which is why it’s helpful to use a fast VPN
This means your data is always partially exposed in the entry or exit nodes when you use Tor.
Thats whyits recommended to use a VPN alongside Tor to encrypt your traffic end to end.
Is Tor online window Safe?

Plus, you’re not protected from malware, so downloading anything with Tor alone can be dangerous.
Plus, they mask your IP address with one from the server location of your choice.
This hides your real location from Tor’s nodes.

So you dont really have to see anything you dont want to see.
Best VPNs to Use Tor Safely in 2025
1.
ExpressVPN doesnt record or monitor anything you do on the dark web.This has been independently audited by PricewaterhouseCoopers.
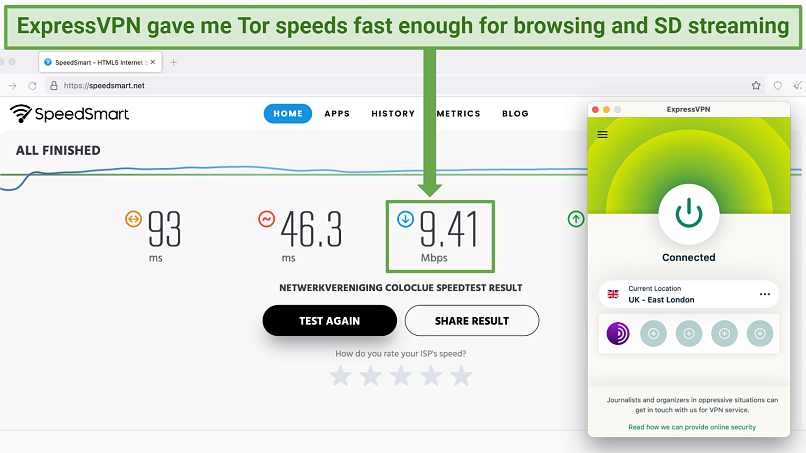
Plus, your data is regularly wiped anyway since it uses RAM-only servers (called TrustedServer technology).
That means that it’s under no obligation to hand over your data to government agencies.
Subscriptions can get a bit pricey, starting at$4.99/month.
However, ExpressVPN offers regular discounts and a 30-day money-back guarantee*.
If you’re not impressed, it’s easy to claim a refund.
I requested mine using the 24/7 live chat and the money was back in my account 2 days later.
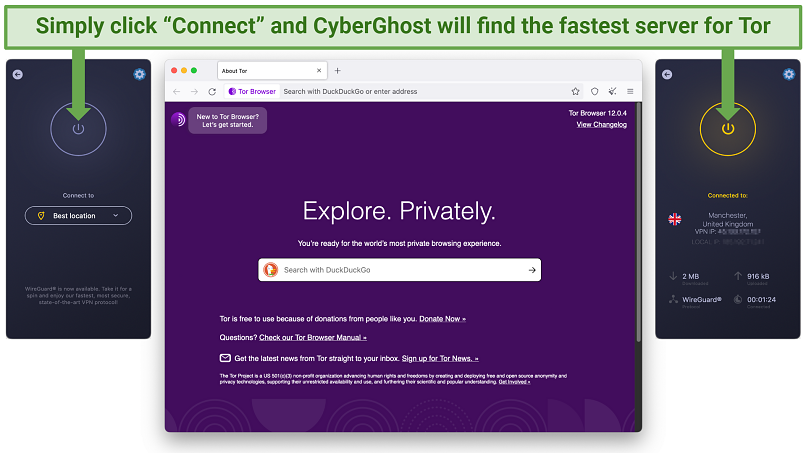
Within seconds, I had a secure connection for browsing the deep web.
The VPN has highly secure NoSpy serversin its Romanian headquarters (outside the 5/9/14 Eyes).
They cost less than a dollar extra per month, but are worth it for the extra privacy.
Only CyberGhost employees can access them, reducing the risk of third-party tampering.
It’s one of the fastest protocols and its open-source, so it’s continuously scrutinized for vulnerabilities.
Like ExpressVPN, the subscriptions can get a bit expensive.
Especially for monthly plans, which only have a 14-day refund period.
That said,CyberGhosts long-term plans let you try it without riskas they have a 45-day money-back guarantee.
It warns you if youre about to hit malicious links that risk infecting your gadget and blocks annoying pop-ups.
Its good at blocking ads on regular websites too.
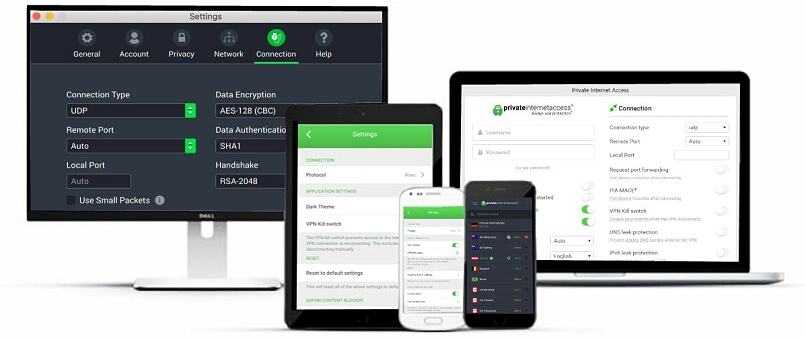
There’s a broad range of choices available to tailor your security on Tor.
This provides the ability to strike a balance between security and speed.
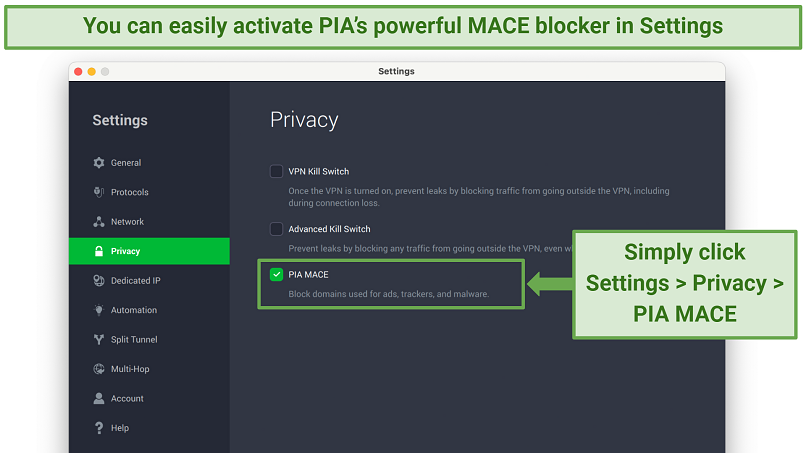
Additionally, there are two options for the kill switch.
The Advanced Kill Switch safeguards against data leaks, even when you deactivate the VPN.
The multitude of security configs can be somewhat daunting if you’re unfamiliar with using a VPN.
All plans include PIA’s 30-day money-back guarantee.I tested the policy myself and had no issue getting a refund.
If your VPN lacks key security features, this method might not work as well.
A kill switch is vital to avoid data leakage to harmful exit nodes when a connection fails.

It offers you some security by concealing traffic from Tor’s exit nodes.
That said, using a VPN over Tor does present some vulnerabilities and limitations.
Using a VPN over Tor just allows you to access surface websites with added privacy.
For this method to work efficiently, the VPN used should support Tor and strictly follow a no-logs policy.
This is whyI recommend taking the following precautionsto give you maximum security while using the net web surfer.
Before downloading and using Tor,I also recommend installing and connecting to a reliable Tor VPN like ExpressVPN.
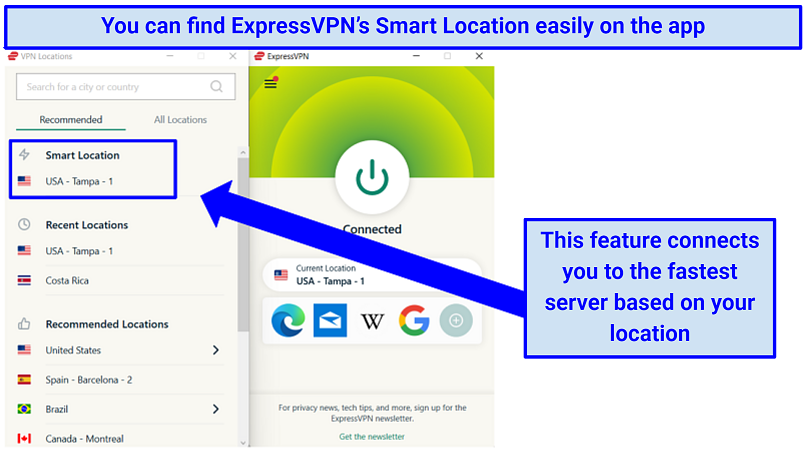
It doesnt matter which server you choose as Tor reroutes your traffic anyway.
Most VPNs will recommend the fastest server for your location.
Additionally, Tor bridges can be used to overcome censorship.
You never know if the user behind the bridge has malicious intentions.
Is it safe to download Tor?
Soit’s recommended to download and use Tor while connected to a VPNto give you more privacy.
Although,you should never download Tor from a third-party site.
Can Tor be traced or hacked?
Using a VPN with a malware blocker can help protect youfrom these attacks.
Whats the difference between the deep web and the dark web?
Thats whyits recommended to use a VPN on the dark web.
Is Tor a VPN?
Are there any alternatives to Tor and the Onion web link?
Plus, its security features give you protection against the threats of the dark web.
you could eventry Express risk-freewith a 30-day money-back guarantee.
Its easy to get a refund if youre not satisfied.
To summarize, these are the best VPNs for Tor…
Your data is exposed to the websites you visit!
Visit ExpressVPN
hey, comment on how to improve this article.













