Quick Links
Summary
Are you worried about your personal files getting stolen by hackers?
What Is Canary Tokens?
It works by embedding your file with a special tracking URL that alerts you through email when opened.
![]()
Suri_Studio/Shutterstock
When a hacker opens the file, a hidden link is opened, alerting you to the breach.
Lets begin by visitingCanary Tokens.
Upon visiting the site, you will be greeted by the Canary Token generator.
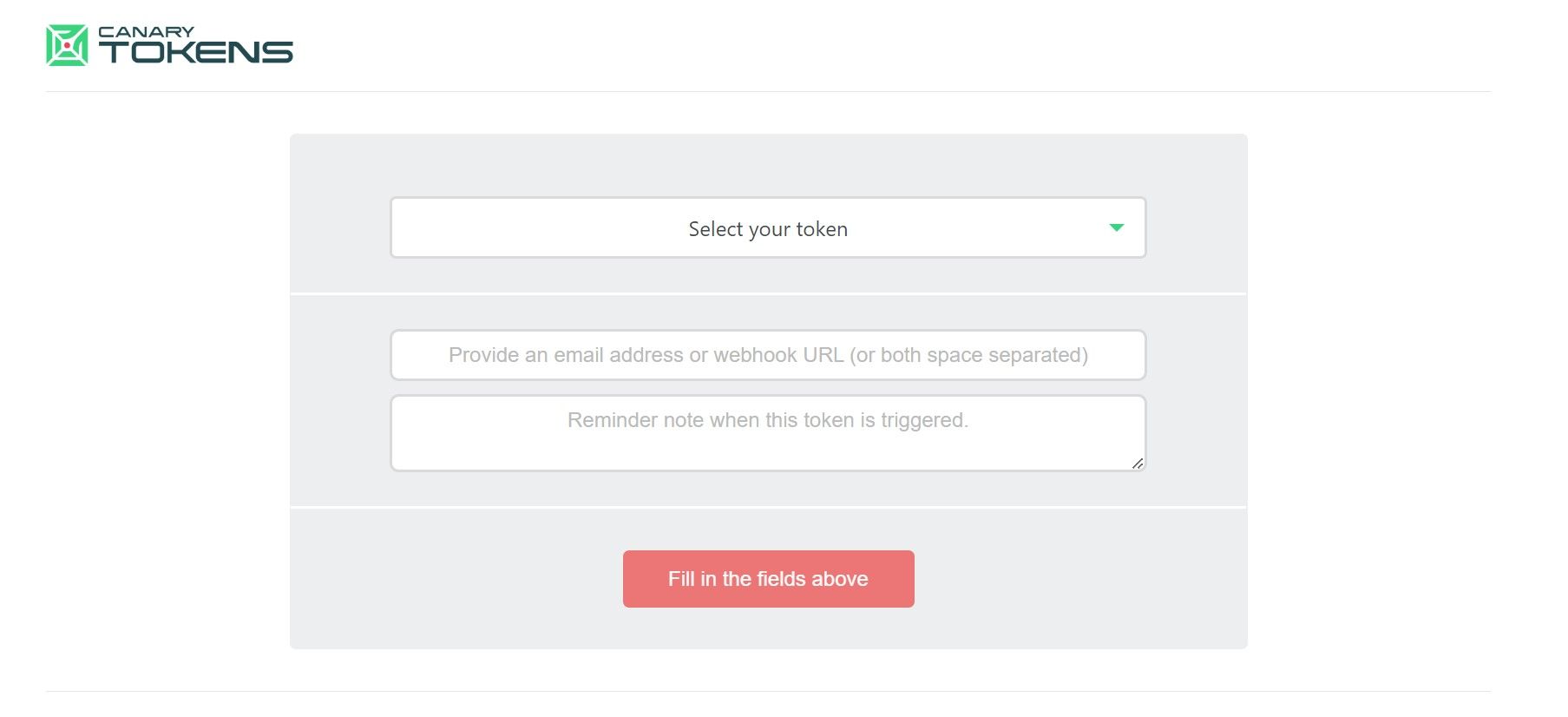
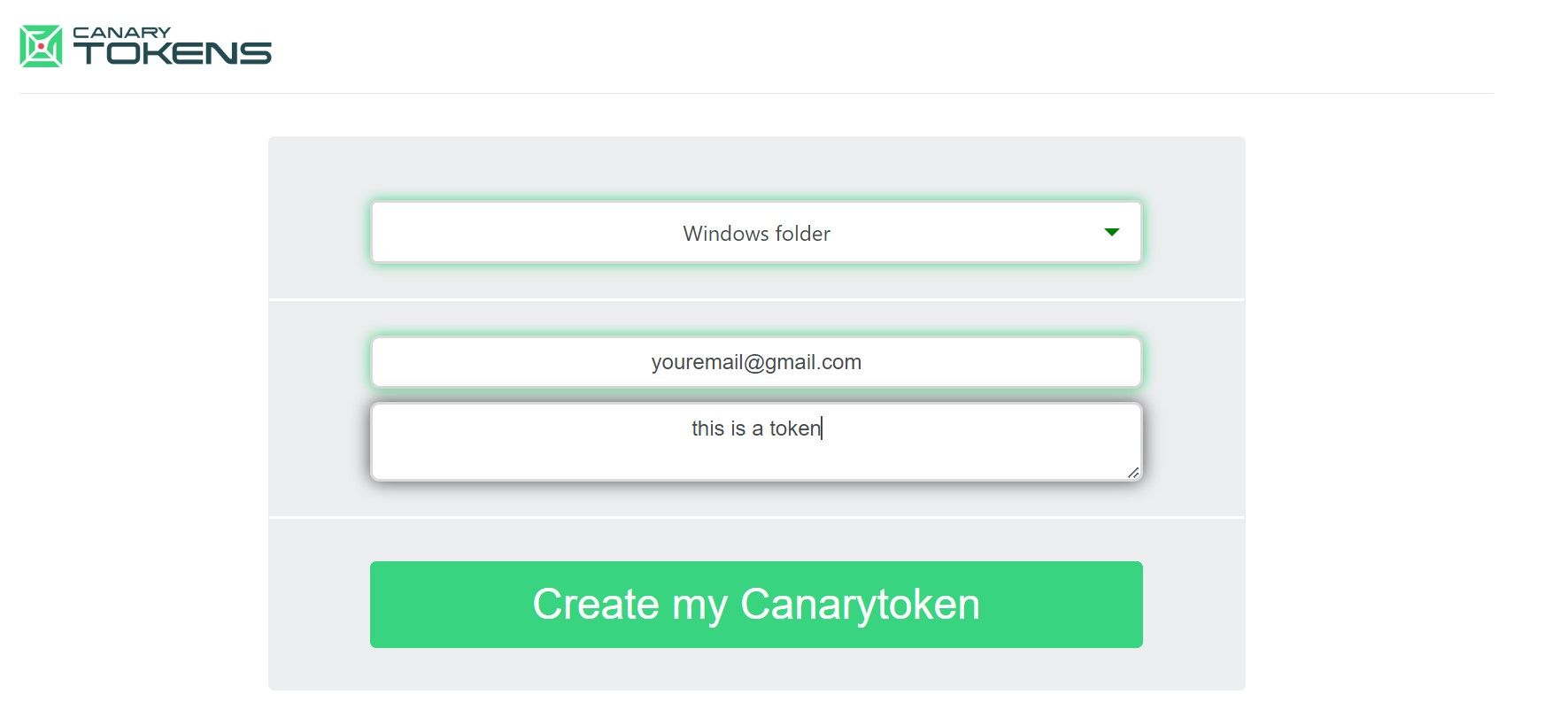
After youve filled out the form, clickCreate my Canarytokenand download the ZIP file embedded with a special token.
Ideally, it should be somewhere easily located for the hacker to find.
You may also want to check your spam folder in case Canarytoken Mailer was identified as spam.
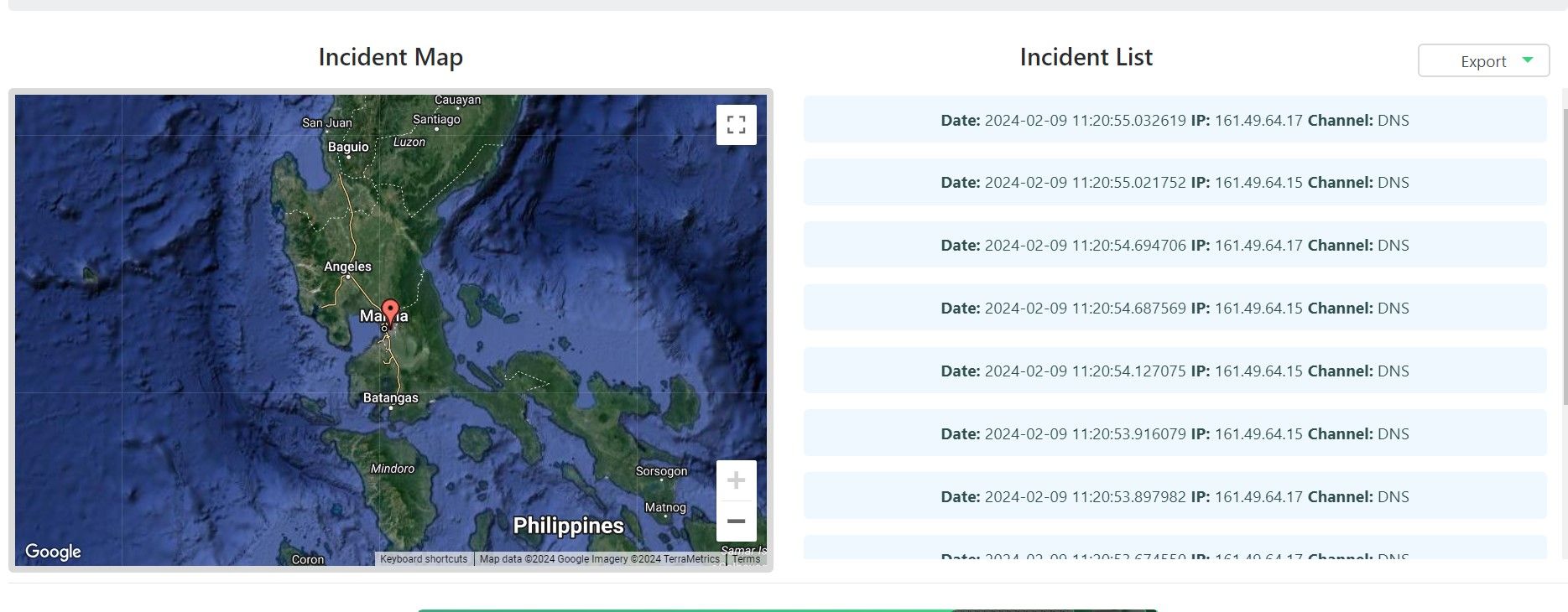
Alternatively, selectMore info on this token hereto view the incident map.
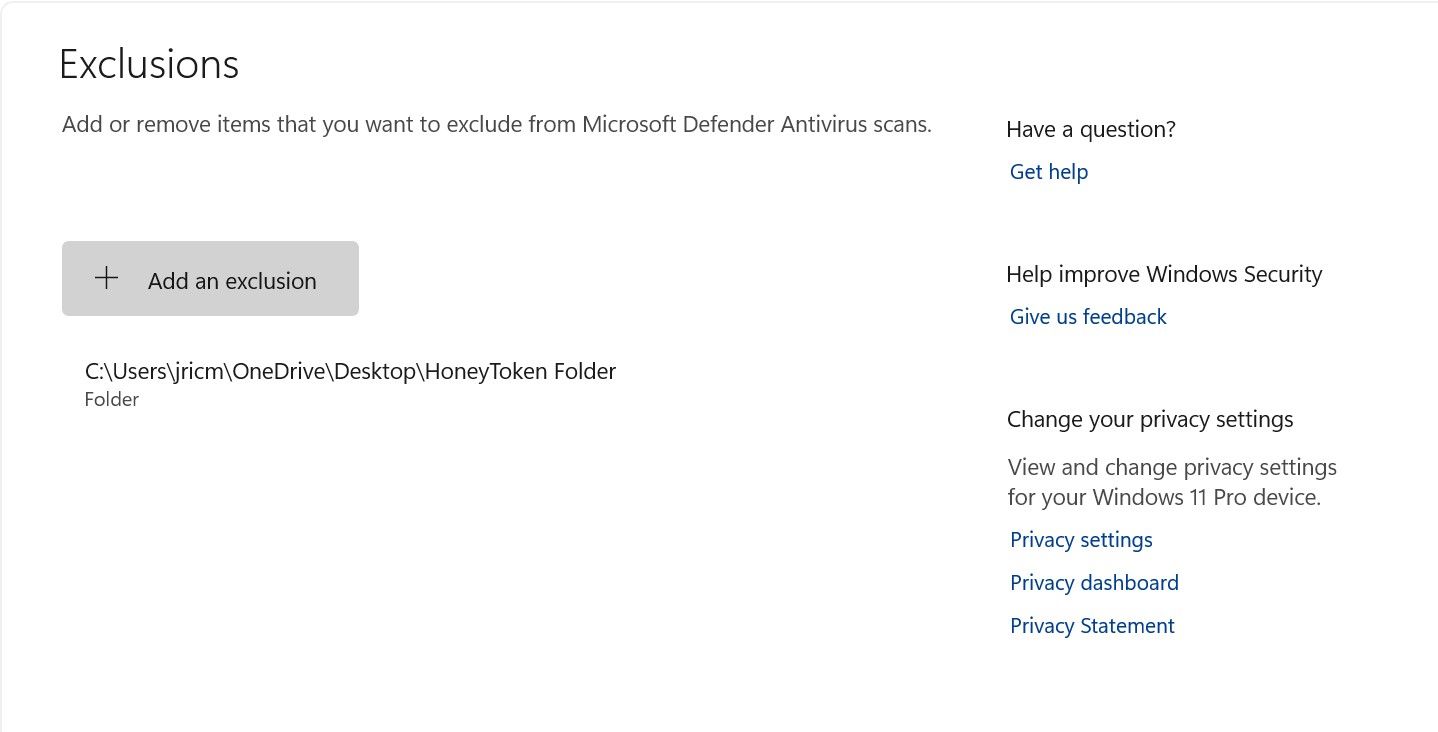
To solve this problem, youll want to exclude the embedded folder from your regular antivirus scans.
Will Canary Tokens Work if the File Is Transferred to Another gear?
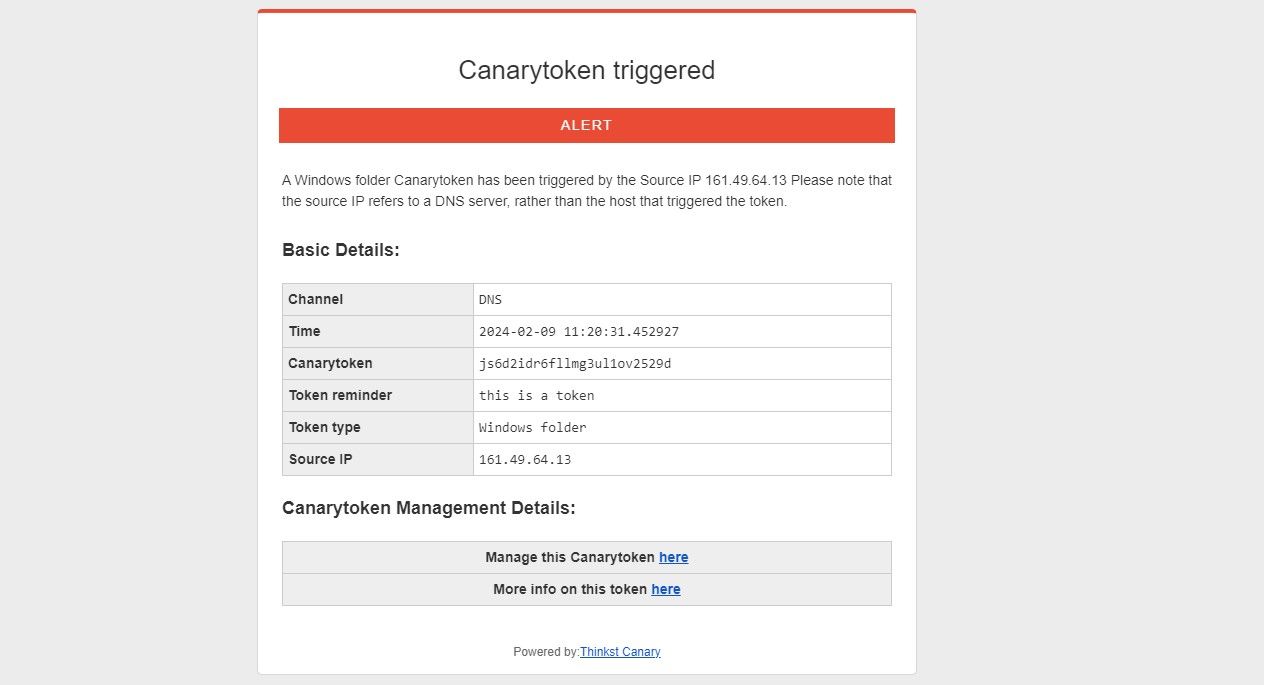
Yes, as long as the tracking URL was visited, you will be alerted about the incident.
As long as the machine is capable of browsing the web, Canary Tokens should work.