The 2016 US election cycle made international hacking part of the global conversation.
Hacking is now one of the most widely discussed threats across all professional sectors.
While Russian hacking dominated the political sphere, Chinese hacking is proving to be the biggest threat to corporations.

Each successive hack reported in the news has madecompanies increasingly aware of the vulnerabilities in their systems.
Large companies have the resources to withstand a dip in sales or large lawsuit.
However, smaller companies may find thateven a small security breach can take down their entire operation.

However,enacting efficient cybersecurity measures isn’t as daunting as it may seem.
Not all hacks are the same, even if they contribute to similar outcomes.
Hackers employ a number of strategies depending on their ultimate goal.

If you run an e-commerce business,website hacks can lead to thousands of lost customers.
Here’s another example.
While consequences for users are relatively minor in this case, it may stillundermine their trust in your site.

Most hackers are far more malicious.
They set up dummy sites that look like yours to trick customers into sharing their private credentials.
From there, they can easilyexploit customers' data.

Often,customer credentials from one site can help a hacker gain access to several other accounts.
Hackers can use these techniques to steal from you and your customers in multiple ways.
Having your site go down even for a few hours can cause asignificant decrease in sales.

While this was a big hit for the tech giants, they had the resources to bounce back.
For a small business, the consequences would be devasting.
Last year, a former Tesla employee admitted tostealing company secrets before passing them to outside parties.
He accomplished this by writing a program that hacked Tesla’s software.
Experts estimate these kinds of hacks are already responsible forlosing millions of dollars of revenue.
There’s another caveat to consider.
You may think that the costs of securing your website are too high.
That’s a grim reality for business owners.
But small businesses are far from the main targets.
Business Insiderrevealed in August 2018that80-90% of login attempts on any retail website are hackersusing stolen credentials.
These hacks range fromphishing attempts to malware attacks and data leaks.
There’s a good reason large companies are more likely to be hacked.
Because they have more infrastructure,hackers have a larger “attack surface.
“This means they have more opportunities to find an opening into their system.
More bugs mean more ways for hackers to exploit the system for their own gain.
Losing billions of dollars can be an extreme consequence of a big company being hacked.
Most people worry about the financial fallout from having their account information exposed through a retail site.
No organization desires to face criticism for subjecting its customers to potential legal proceedings.
Apart from the financial incentives,why else do hackers target companies?
Many aren’t looking to push law enforcement into punishing citizens.
Some hackers justtake pleasure in causing chaos.

However, if we look at the 2016 American elections, Russian hackers appeared to have several goals.
For starters,this is not the first time Russians have caused a political mess for rival countries.
Estonia and Georgia were both targets of DDoS attacks originating from Russia.

Some believe that this chain of events served toweaken a rival country.
Politics aside, the perception that a government is secure gets undermined when they’re so easy to hack.
However,Russian hackers are far from the only national threat to Western interests.

Chinese hacking efforts have continued to increase, despite a brief pause during the Obama administration.
The targets of Chinese hackers are generally different than the Russians'.
Overall,the Chinese have been behind major corporate hacks in recent years.

Behind these data breaches is a Chinese government mandate called Made in China 2025.
Its goal is to make China the frontrunner in global technology and engineering advances.
A majority of corporate hacks can betraced to government-backed hacking agencies.
These companies have managed totake advantage of security weaknesses to uncover top-secret design plans.
Even theUnited States Army isn’t immune to Chinese meddling.
Chinese hackers have targetted every sector of technology including medical technology, aerospace engineering, and robotics.
These security breaches might not have the same individual impact but can stilllead to significant losses in revenue.
Hacking a company can come with several benefits in one package.
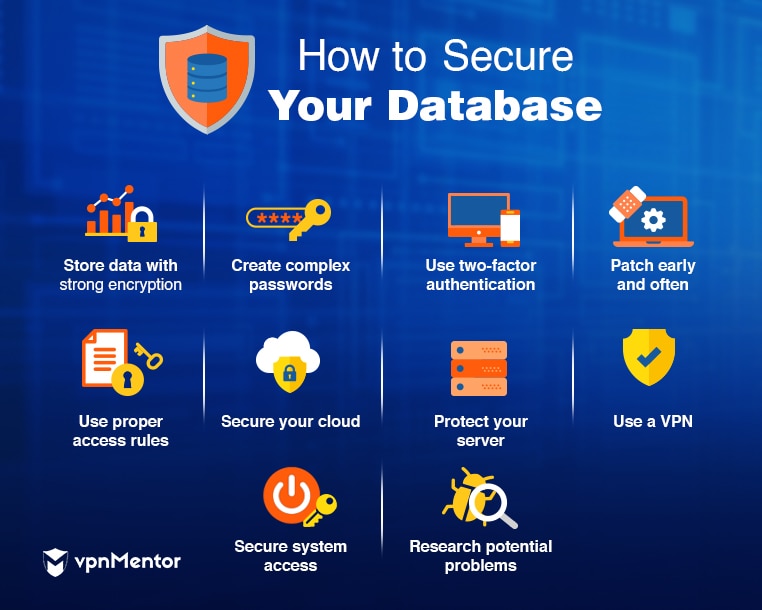
Always store your data with high levels of encryption.
The higher the level of encryption, the more secure your data will be.
AES-256 is frequently chosen because it’s strong but it isn’t too computationally intense for the internet.
RSA, on the other hand, is also strong, but much slower.
Create passwords that are difficult to crack.You may even be better served by a passphrase.
A passphrase is a full sentence that can be used in place of a single word.
Its length and complexity can make them more difficult to interpret.
Passwords should always be longer than eight characters and include a variety of numbers and special symbols.
Repeating sequences, such as 123123 are too easy to crack.
You should avoid using any identifying information like a birthday in your password.
It’s also extremely important tochoose unique passwords for every accountyou have.
Using a single password for several accounts can compromise multiple systems if that information falls into the wrong hands.
Employ two-factor authentication.Two-factor authentication requires a second step on top of a password to access a given account.
Patch early and patch often.
However, they’ve also proven to be some of the most vulnerable to leaks.
You should never assume that the default tweaks are enough to keep your data secure.
This is called “defense in depth” by cybersecurity experts.
Use proper access rules.
Access rules are the way you could control how users and systems communicate with outside networks and systems.
There are several basic rules that should be put in place to maintain a high level of security.
These are all elements that should be considered when your system is first being designed.
Many are still accessed from the outside, posing a security risk.
They also encrypt any data traveling between your unit and a server.
That way, even if there is a leak, your activity will have an added layer of protection.
For more information on how to choose a VPN for your business,we’ve published a helpful guide.
You’ll want to continue reading up on subjects such as new exploits and attack vectors.
New research on how to find leaks is published regularly.
Summary
Having your website hacked or experiencing a database leakcan be devastating to your business.
While securing your system may seem like a daunting task, each step that you take makes a difference.
Being aware is always the best place to start.
This guide will just help you to continue to lower your risk of exposure.
All we ask is that you attribute it to vpnMentor.com
hey, comment on how to improve this article.
