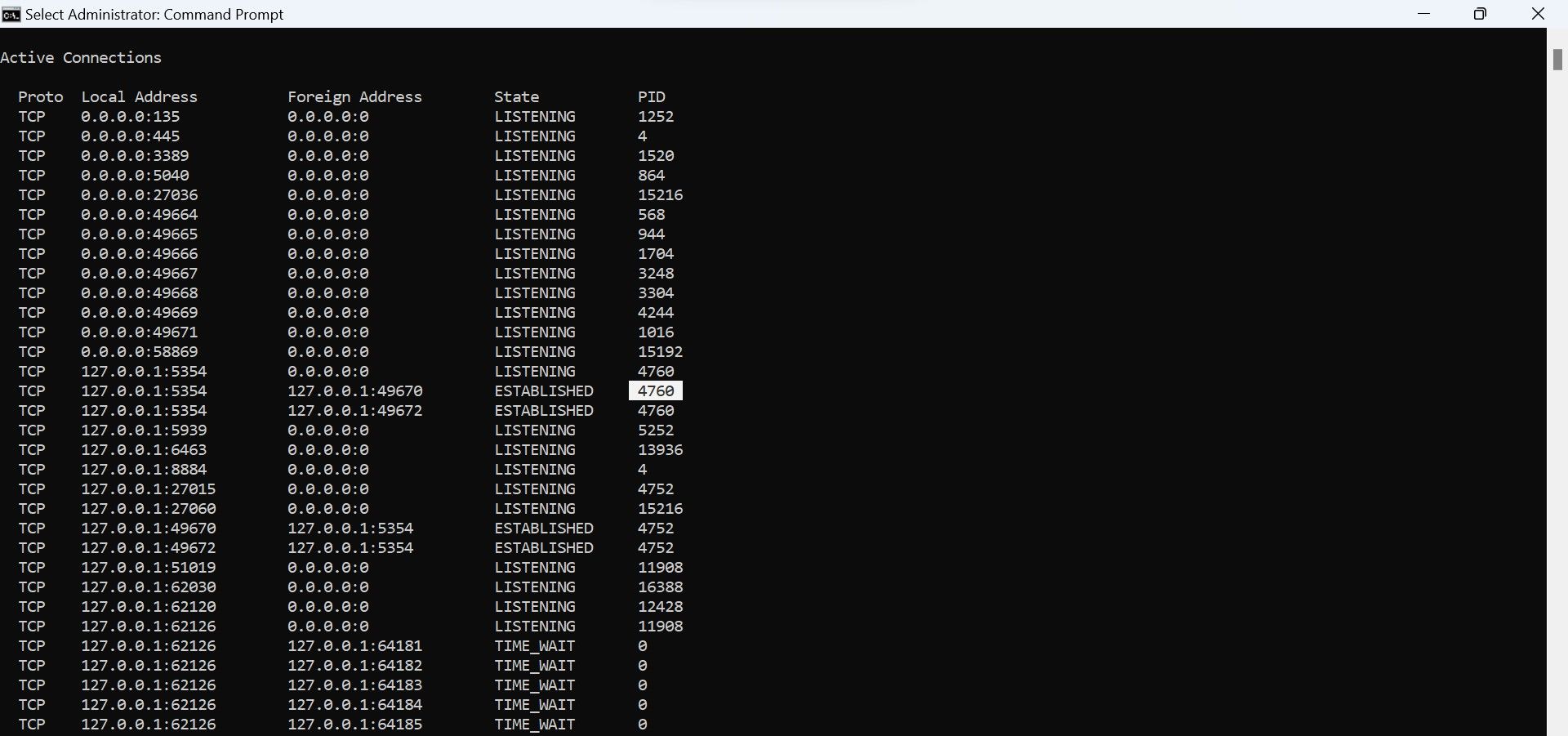
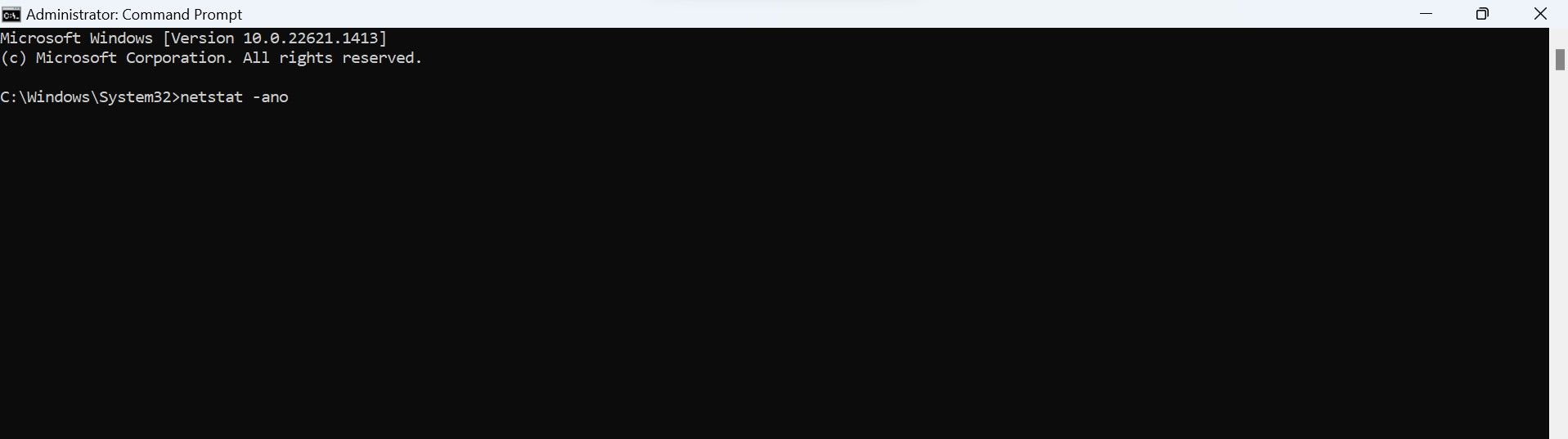
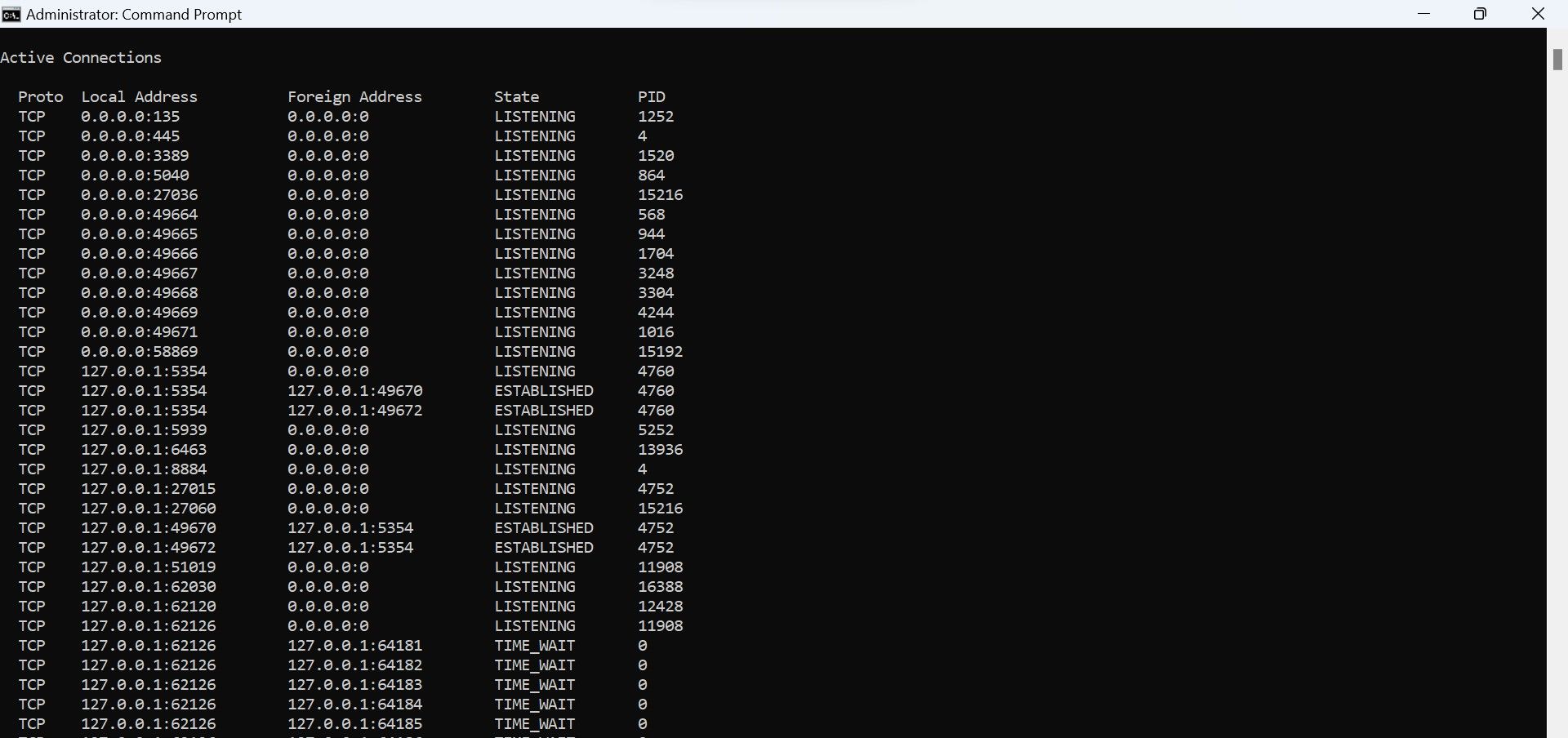
Pay attention mainly to theStatecolumn, where you’ll find three main terms:Established,Listening, andTime_Wait.
From these three, focus on the connections whose state identifies asEstablished.
The"Established"state indicates a real-time connection between your machine and the remote IP address.
Don’t panic if you see a lot of established connections.
However, you oughta analyze each of these connections separately.
This will help you determine if there are suspicious connections being made to a hacker’s server.
Do not wrap up the Command Prompt; we will use the netstat information in the next steps.
Check the ISP and organization that use this IP address.
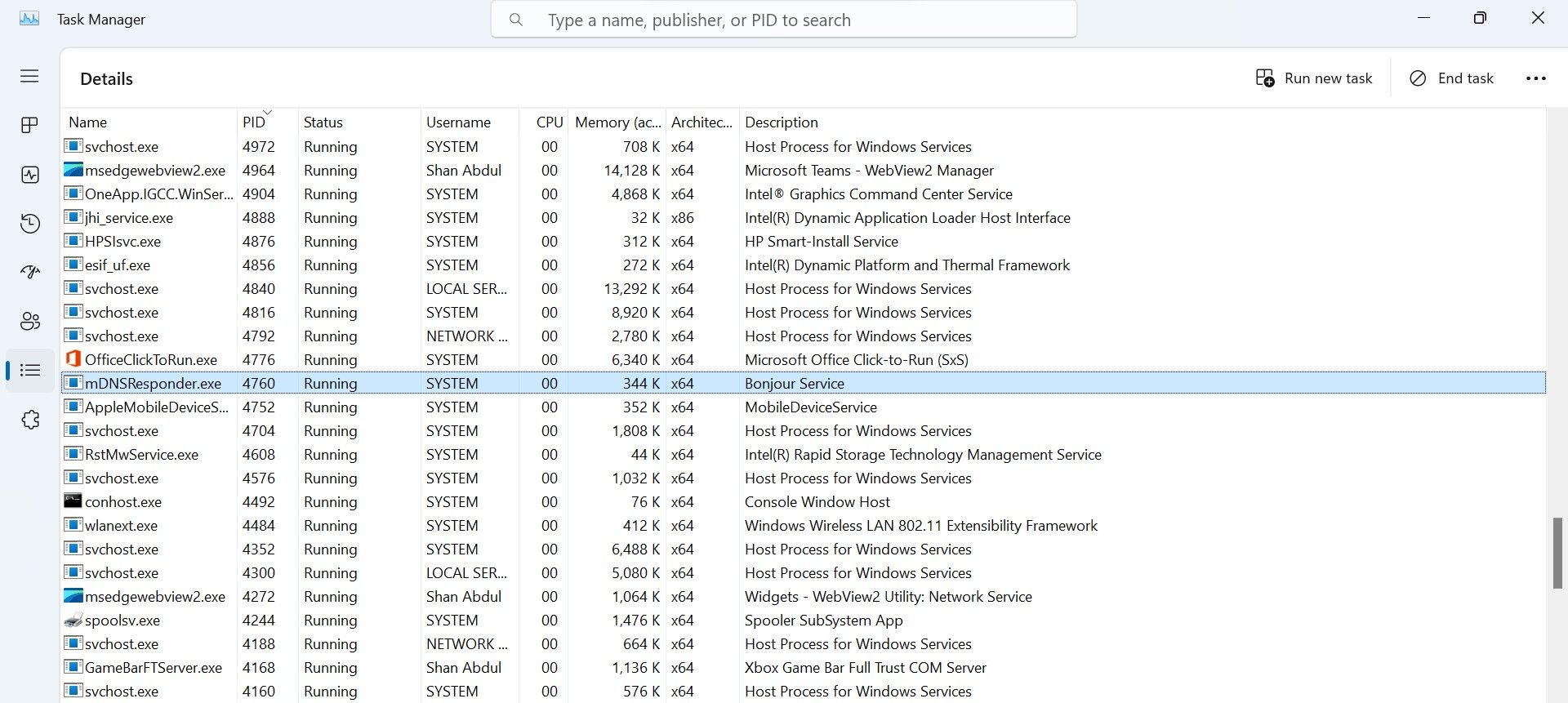
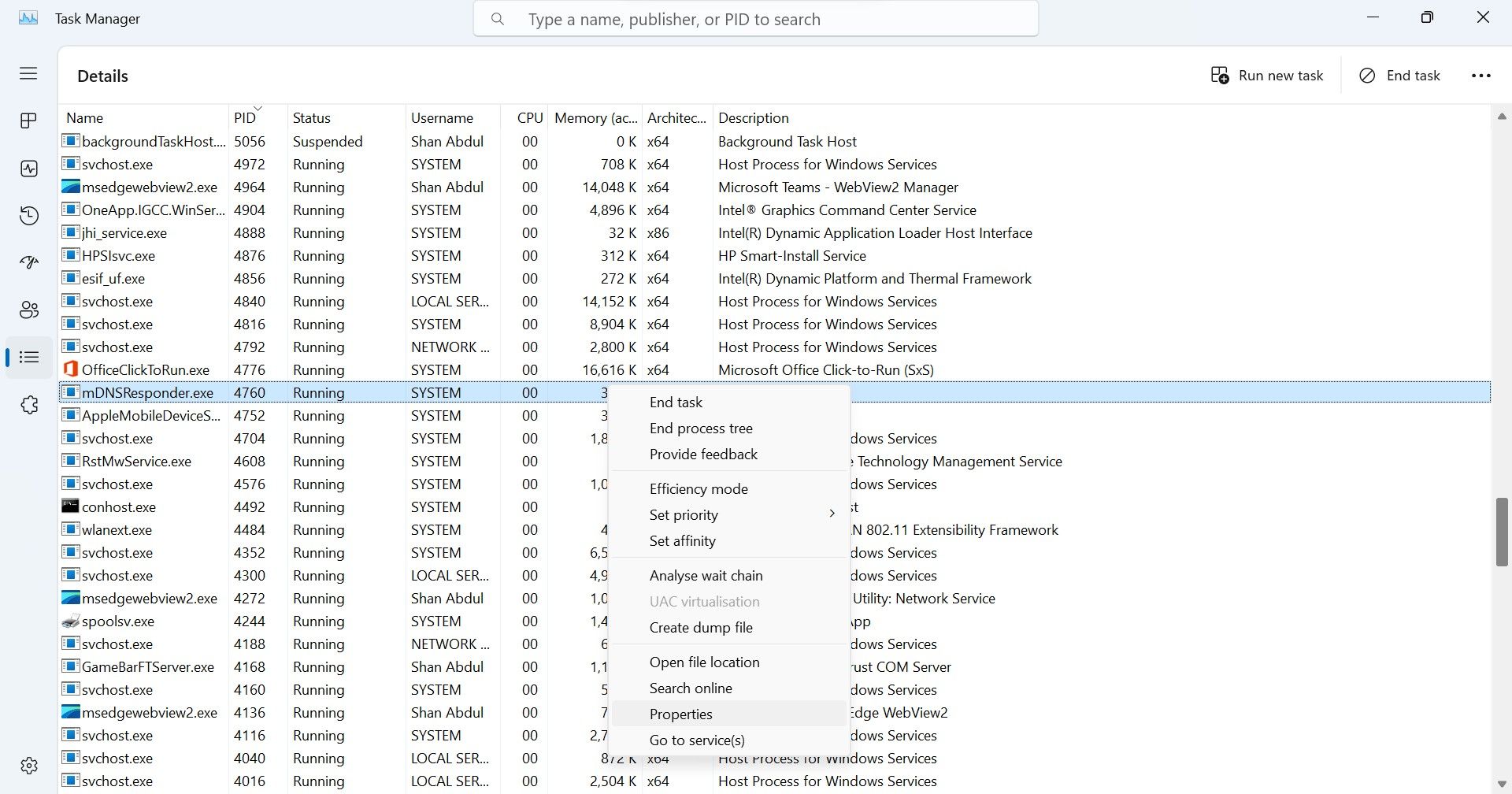
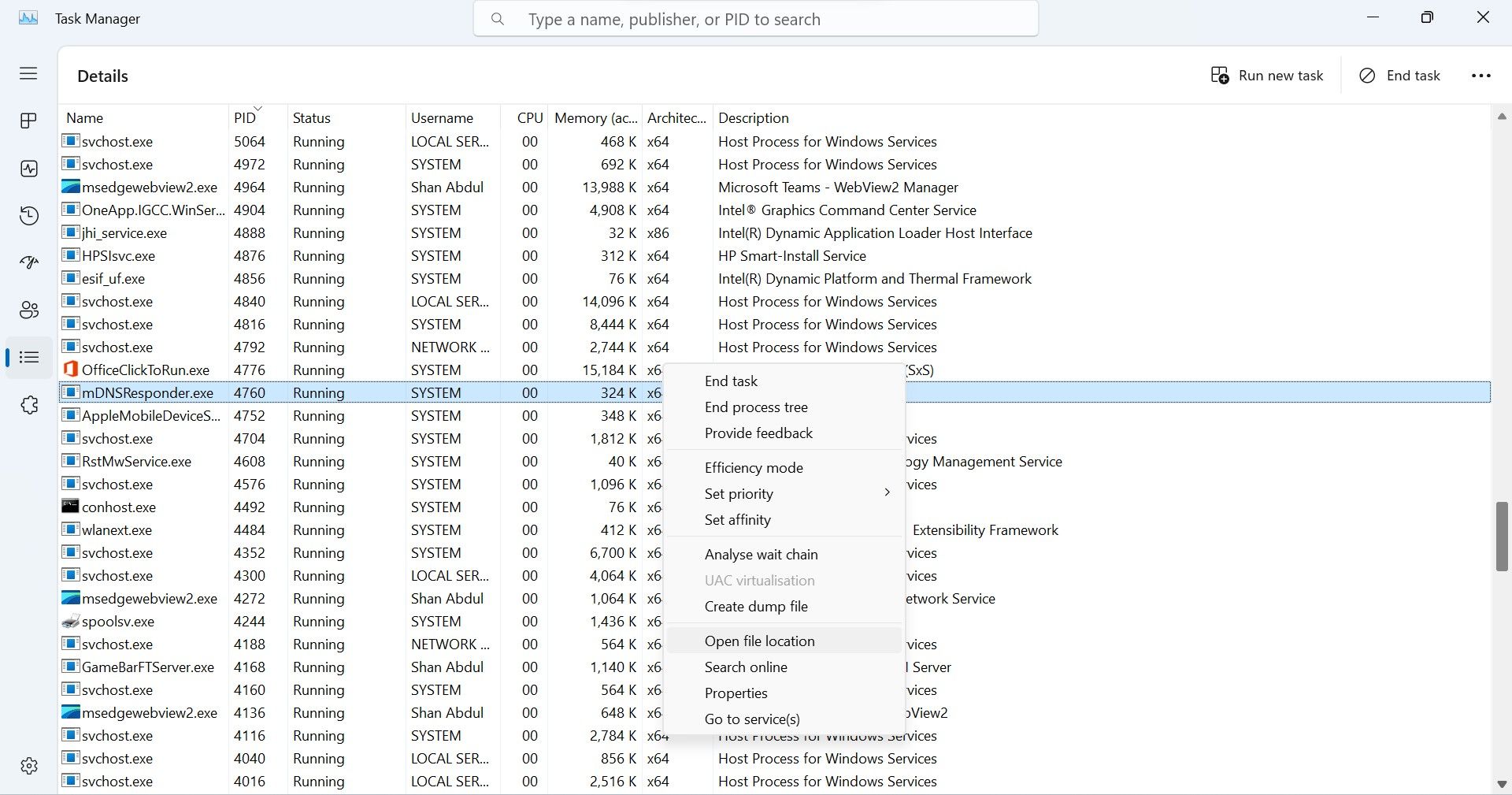
So, right-go for the suspicious process and selectProperties.
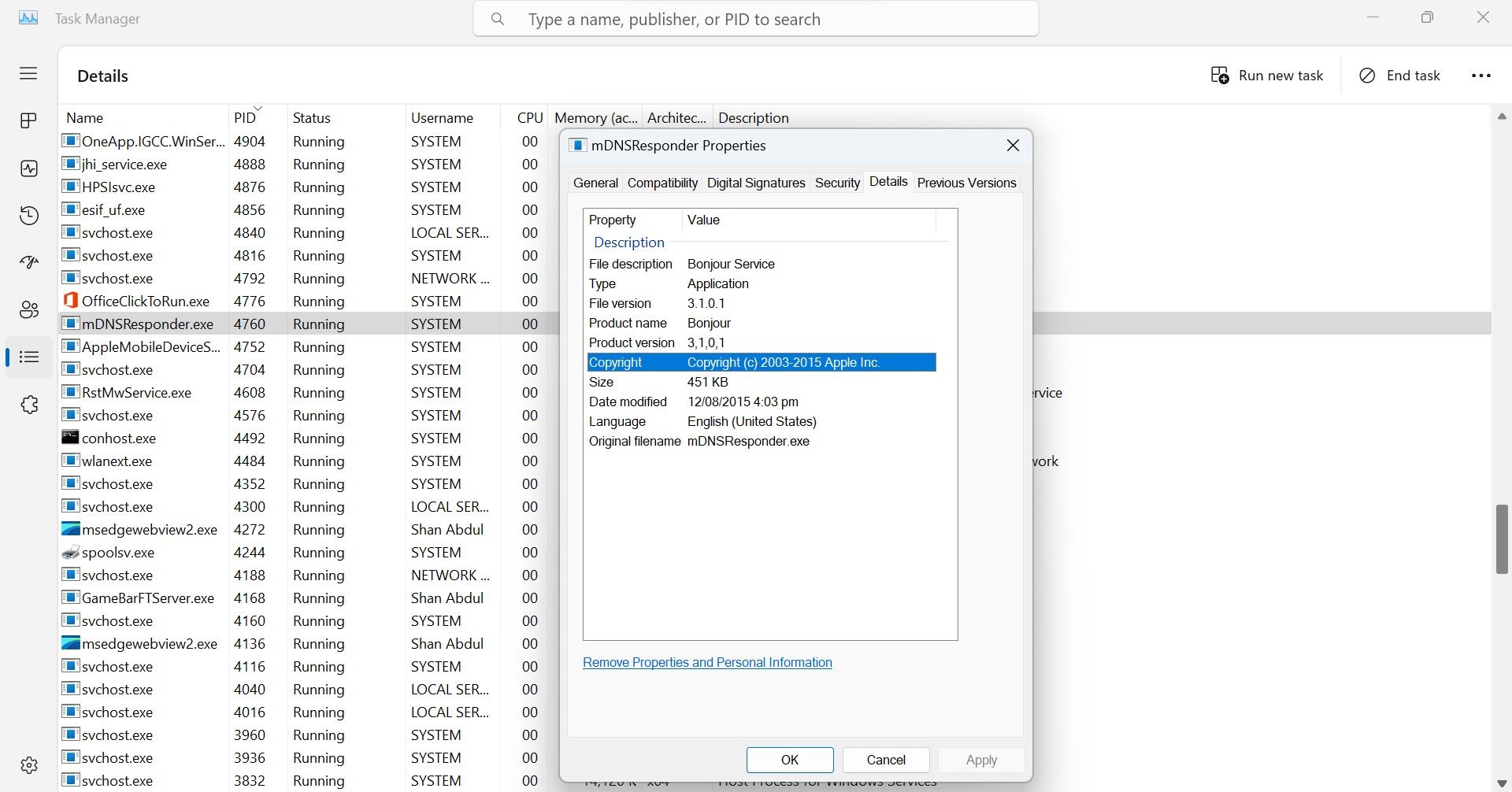
Then, navigate to theDetailstab for more information about the process.
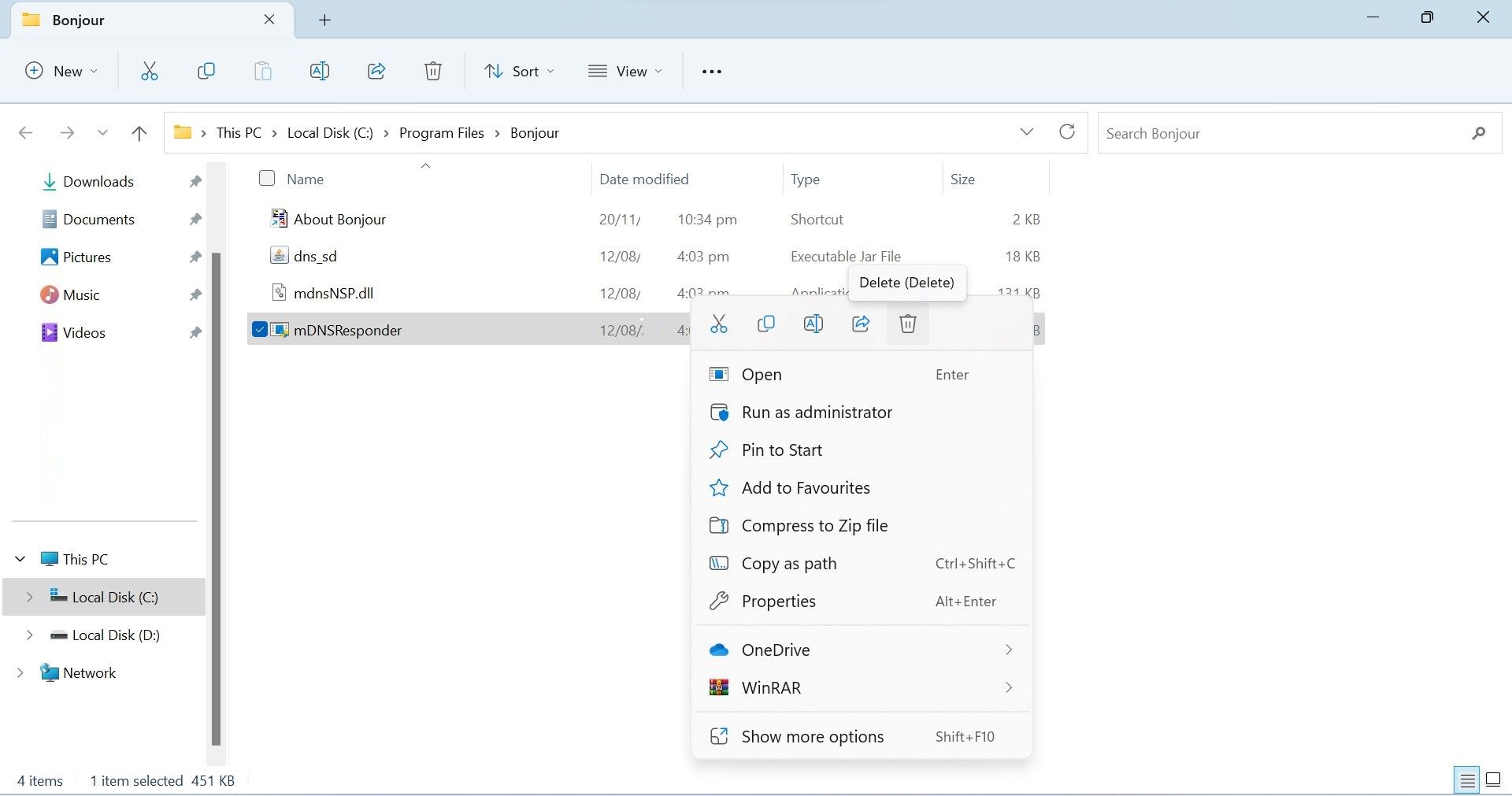
Likewise, they can code the program so it does not appear in Task Manager.
Only then can you be sure that your machine is completely secure.
Hopefully, our guide will help you identify if any suspicious hacker is monitoring your activity.