Botnet attacks are one of the most serious cybersecurity threats today.
So what actually are botnet attacks?
How can you detect such malware on your rig?

And how can you avoid being infected?
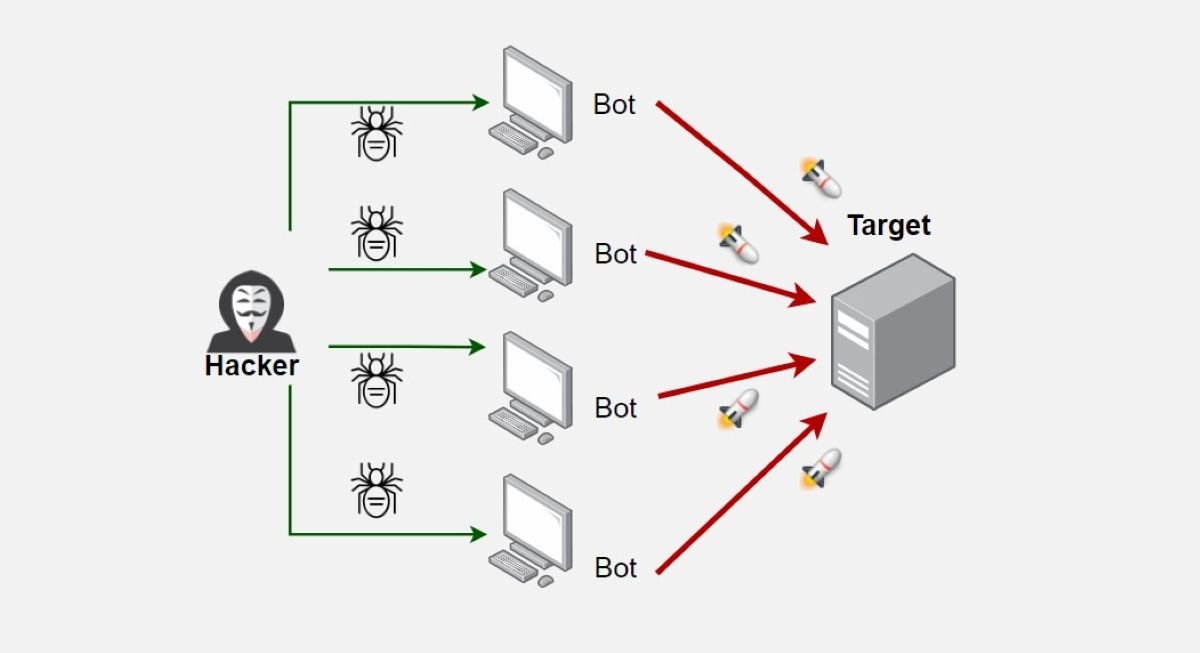
What Is a Botnet Attack?
These devices, managed by the hacker, attack a target system.
Suppose you find a free version of a game you’re interested in online.
But nobodycracks the free versionof a high-paid game so that everyone can download it with no consequences.
If a service is free, it’s too good to be true in most cases.

This file is very likely prepared by a malicious attacker.
The attacker injects malware into it.
When you download this innocent-looking game file, you actually infect your unit with malware.

Of course, there are numerous ways you might be infected with malware, not only through cracked files.
This may seem quite innocent because it is not yet active.
Threats to a malware-infected computer that has joined a botnet are not limited to this.
Attackers can also use it to threaten you, or indeed anyone.
Early detection of botnets plays a crucial role in hazard management as it will minimize damage.
This makes it difficult to tell if there is a botnet on your system.
A decent way to check is to look into your bandwidth.
But the best way is to use your virus scanner.
Antivirus software can effortlessly scan for botnets and other malware.
Some antivirus software even uses a special botnet checker.
Finally, botnets make unexpected changes to your system files.
Also, botnets infect your system files to prevent you from updating your operating system.
Botnets are light and difficult to spotbut not impossible.
Your priority should be ensuring your operating system is up-to-date.
Never delay the update requests your operating system notifies you of.
Almost every update package includes some security improvements.
You should not download a program whose source you do not know.
Use safe, popular download sites, or go for open-source software.
Peer-to-peer (P2P) downloads are very risky as they contain many malicious attachments.
If possible, do not engage with P2P downloads.
When you install a new gear to your web connection, never use default passwords.
In particular, devices such as webcams and modems come with default credentials.
Be sure you change these logins.
Using default passwords makesIoT botnet attacks, like via Mirai malware, easy.
Using a strong password reduces the risk of any malware attack.
In particular, two-factor authentication makes your accounts more secure.
confirm you read and configure the security protocols and security parameters of the applications you use too.
Using a firewall automatically blocks unsafe connections.
This method is a surefire way to protect yourself from botnets and other malware.
When you take these precautions and have an awareness of cybersecurity, you should be protected from many attacks.
Fortunately, the precautions you take against botnets also apply to other malware.