Short on time?
Norton is my top antivirus for checking if a file is infected in 2025.
Ill be usingNortonas my example but the same steps and rules apply regardless of antivirus.

That said, the specifics on how to run a scan or turn on features will vary.
Step 1.
Install Reliable Antivirus Software
The first line of defense against cyber threats is having a reputable antivirus.

Ill mostly be giving instructions on using Norton in this guide.
To install Norton, head to the website, choose your preferred plan, and purchase it.
verify Nortons updated to the newest security patch, so youre not vulnerable.
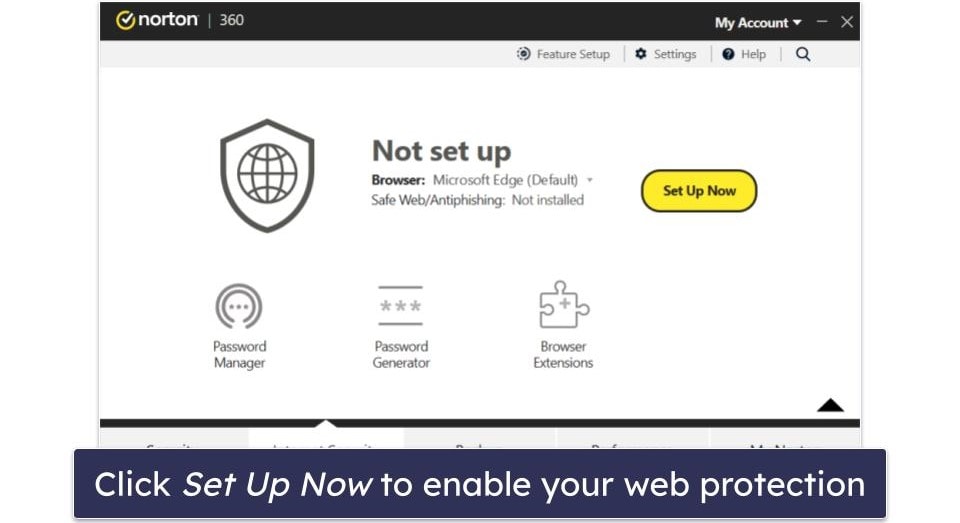
Norton will update itself if there are any pending updates.
Step 2.
Run an Antivirus Scan
Once youve set up your antivirus software, its time to scan the suspicious file.
Opt for the third option.
ClickFile Scan(or a similar alternative) and navigate to the file youre concerned about.
Finally, hit theScanbutton.
If youve already opened the file outside of your antivirus, you may have a bigger malware infection.
In these cases, you should probably execute a full scan by selecting theFull Scanoption.
Step 3.
Turn on Real-Time Protection
Real-time protection will defend you against malware before it can activate.
While its on by default in most antiviruses, its always worth checking.
Step 4. you could filter through most online dangers by following practical safety advice.
For starters, its wise to refrain from opening suspicious files.
Clicking on them could lead you straight to a malicious site or cause an immediate malware download.
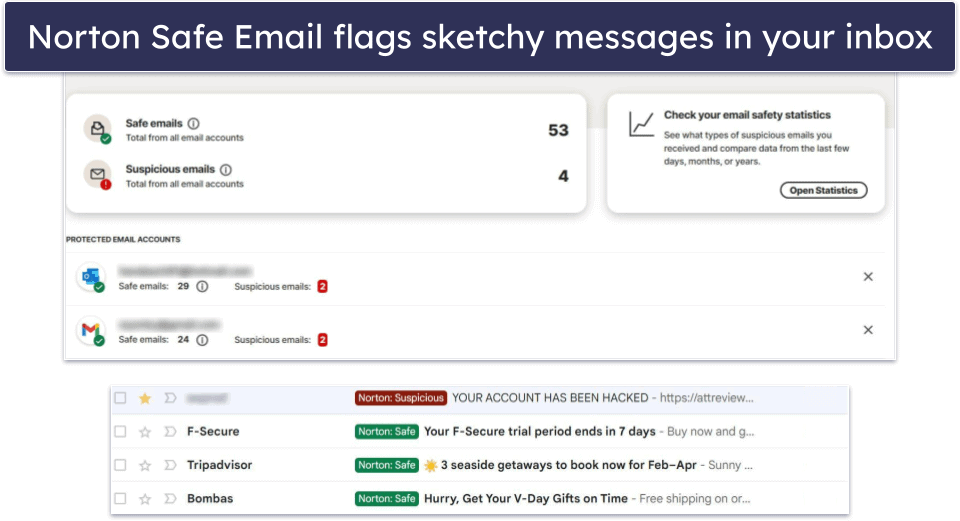
Norton offers an email screening service that takes some of the guesswork out of avoiding online threats.
you might connect Safe Email to up to 5 addresses.
Once you do so, all incoming messages will be screened for dangerous files and other threats.
Safe emails will be marked in green while suspicious ones are given a red tag.
It wasnt perfect in my tests, so you should still use caution, but its better than nothing.
The service is available as an add-on for any Norton bundle.
You should also ensure the URL is verified with SSL (meaning it says HTTPS, not HTTP).
Remember the timeless advice: if its too good to be true, it probably is.
Next, youll want to run an antivirus program.
To start, launch the antivirus and run a thorough system scan.
How Do Infected Files Get Onto Your equipment?
What Can Happen if You Download an Infected File?
Malicious files could be ransomware, locking up your data and demanding payment for its release.
Office documents can carry macro viruses, resulting in data corruption or even covert surveillance of the whole organization!
Some files host trojans, opening backdoors for hackers to take control of your system.
Additionally, keyloggers could record your keystrokes, stealing sensitive information like passwords and credit card numbers.
These include PDFs, Word documents, Excel spreadsheets, and other data files.
Unfortunately, even seemingly harmless image files or MP3s can harbor malware.
Its crucial to consider the source of the file.
What kinds of viruses are usually in infected files?
Infected files can contain a wide range of viruses, all beaten by agood antivirus like Norton.
Yes, unfortunately, mobile devices are not immune to malware.
you’re free to unwittingly download an infected file onto your phone, just like on a PC.
This can occur when downloading attachments, apps from unofficial sources, or even through compromised Wi-Fi networks.
How do antiviruses get rid of malware?
Antivirus softwareemploys several strategies to identify and eliminate malware.
The antivirus then attempts to clean the file by removing the malicious code.
If this isnt possible, the file may be deleted entirely to ensure the safety of the system.