If you’re not, you should be.
What Is Gold Pickaxe?
The email typically pushes the user to download the fake app.

Suttipun/Prostock-Studio/Shutterstock
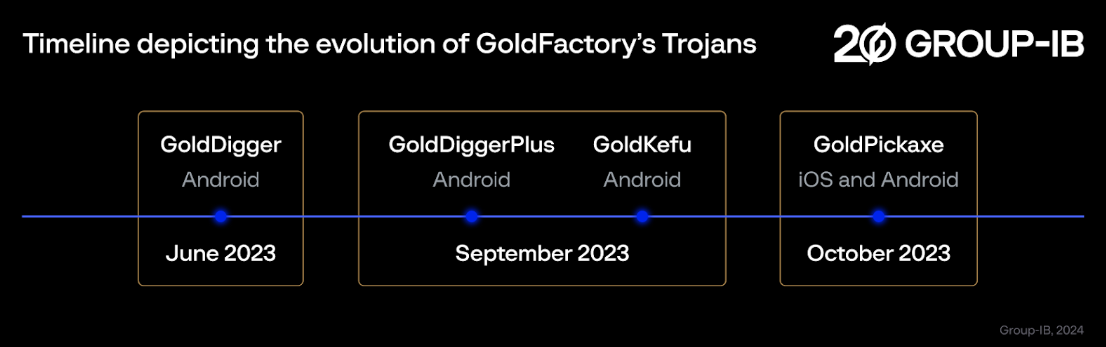
How Does Gold Pickaxe Work?
Once the victim downloads the infected app onto their phone, it immediately starts gathering data on the user.
This includes going through text messages, scanning web traffic, and looking through files.
Group-IB
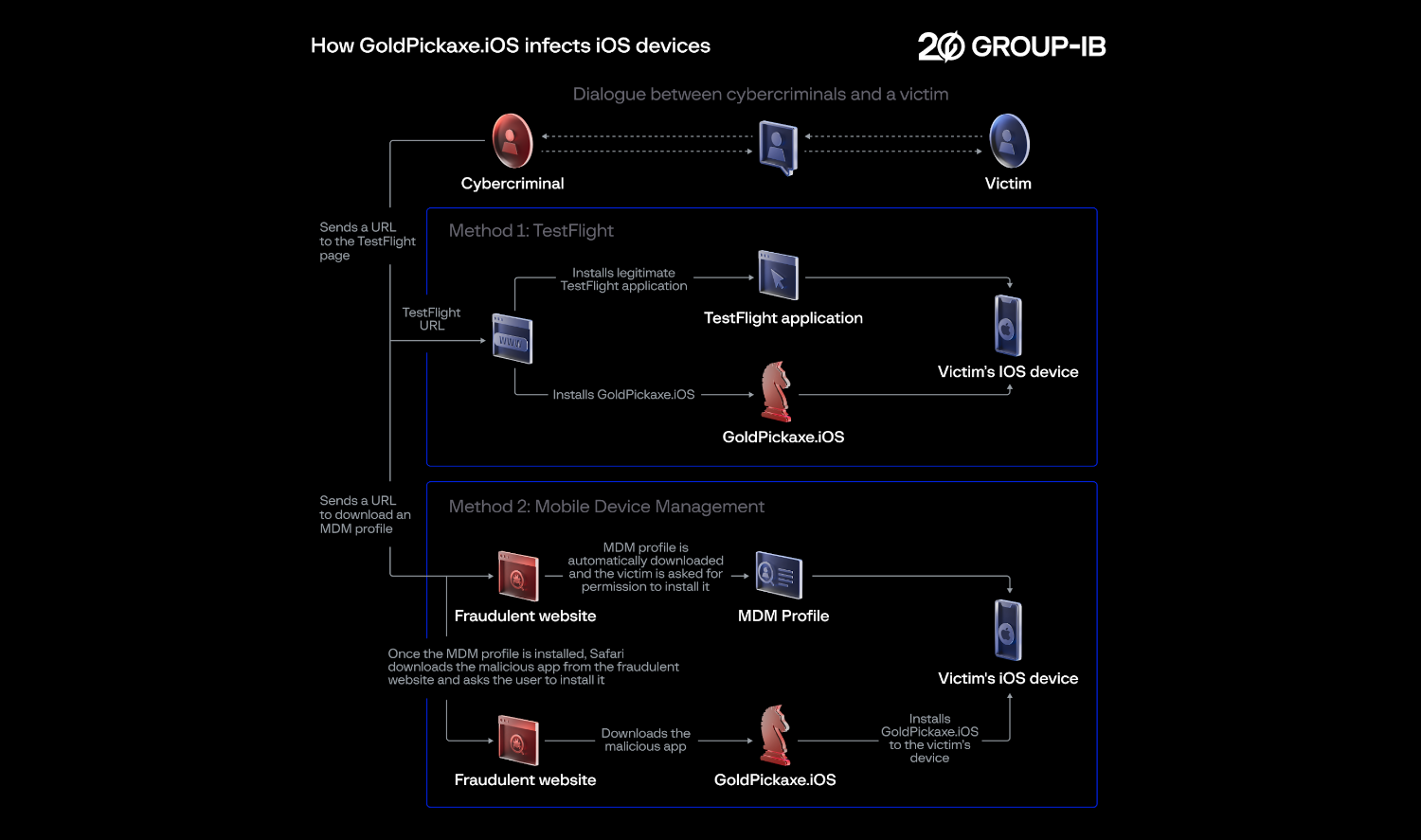
As part of the social engineering, victims are pushed toinstall a Mobile gadget Management (MDM) profile.
The first is by directly asking the user to scan their face.
It’s important to note that the malware does not get biometric face data from services like Face ID.
Group-IB
Instead, it tries to photograph your face through the camera or within your files.
What Can Scammers Do With Your Face?
Gold Pickaxe harvests facial data to help hack bank details.
Group-IB
However, it’s by no means the only way a scammer can use a picture of your face.
These deepfakes can then be used to perform more scams.
With it, they may take out loans and create official documents under your name.

goffkein.pro/Shutterstock
When installing an app, ensure to read all of the permissions.
you’re able to also install an antivirus app to keep these malicious apps off your system.