There are many ways to secure your online accounts.
You might have heard of two-factor and multi-factor authentication, which are both common.
But ensuring that authentication is out-of-band is another vital way to secure your accounts and personal information.
What Is Out-of-Band Authentication?
This way, fraudsters or hackers have a hard time accessing your account.
That way, separate channels are being used to ensure the safety of your account.
Image Credit: Christiaan Colen /Visualhunt.com
Note that OOBA can occur simultaneously with otheruser authentication systems, such astwo-factorandmulti-factor authentication.
This means the same rig is possibly used to establish the authentication process, allowing room for compromise.
Authentication (2FA, MFA, etc.)

The likelihood of any hacker simultaneously gaining access to both of the separate channels is significantly lower.
This makes out-of-band authentication an effective countermeasure against what is referred to asman-in-the-middle (MITM) attacks.
That’s exactly what happens in a MITM attack.

MITM is also known as anadversary-in-the-middle (AiTM) attack.
Your data can be siphoned, funds cleared, and sensitive information made public.
Out-of-band authentication improves your security when you conduct activities online.

Image Credit: Christiaan Colen /Visualhunt.com
Try opting for measures that also request OTPs or tokens, as these add extra layers of security.
Out-of-band authentication is also possible when using one unit but via two different apps independent of each other.
So, it’s no wonder cyber-fraudsters and hackers so easily target them.

you’re able to easily implement OOBA across several of your accounts using a mobile phone.
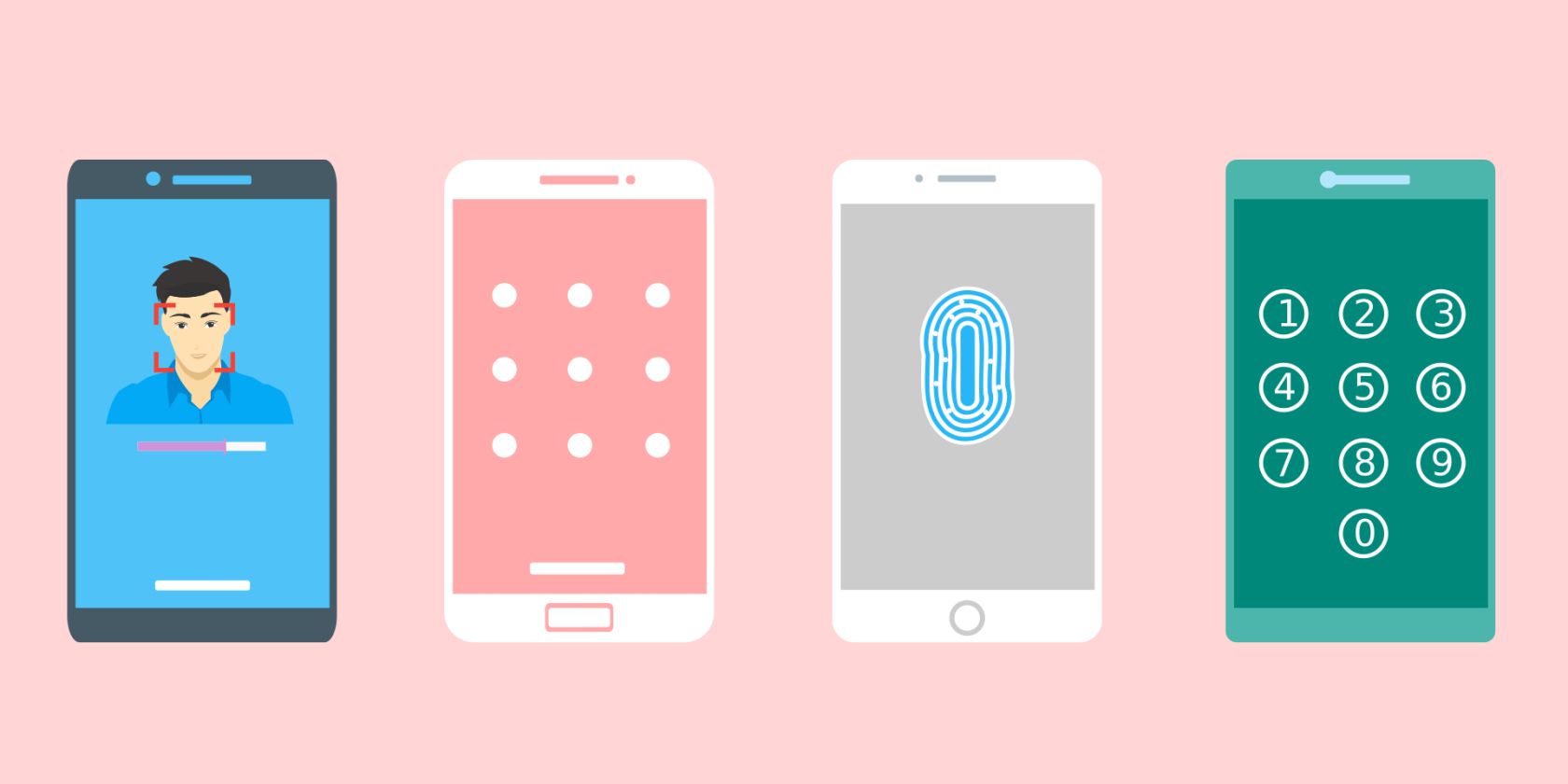
OOBA using a mobile phone is hinged on the three sources of information authentication factors are based on.
Not your literal finger, of course, but a fingerprint or facial recognition should suffice.
It could also answer a secret question you’ve set up before.
What You Own
Another field will involve information gotten from or sent to something you own.
This could be any or all of the information embossed on your bank (credit or debit) cards.
These features are usually employed in the execution of out-of-band authentication.
Who Uses Out-of-Band Authentication?
Out-of-band authentication is worth its weight in cybersecurity gold, which is evident in its diverse applications.
It is commonly used to secure online transactions and social media accounts access.
Small, retail, and medium to large enterprises also bank in on the security benefits OOBAoffers.
Hackers will find your account harder to infiltrate, thanks to out-of-band authentication.