On Windows, attackers can execute a PDF as though it were an EXE.
Have you ever wondered how attackers do this?
Troy is located within the borders of today’s Canakkale city.

Soldiers hid inside this model and secretly entered the city.
If you’re wondering, a copy of this horse model is still found in Canakkale, Turkey.
The Trojan horse once represented a clever deception and an ingenious feat of engineering.
Thisvirus is called a Trojanbecause of the concept of being undetected and causing harm.
They are quite small for this purpose and can cause serious damage.
What Is the RLO Method?
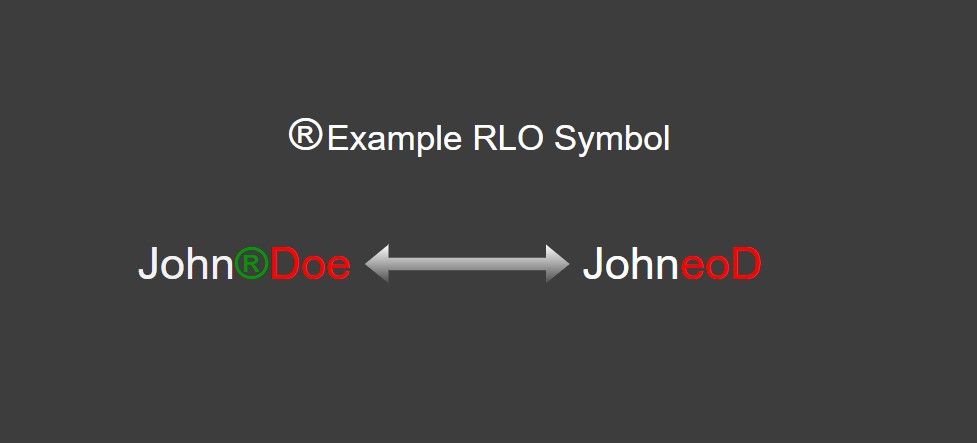
Many languages can be written from right to left, such as Arabic, Urdu, and Persian.
Many attackers use this nature of language to launch various attacks.
There is an RLO character for this in Windows.
Attackers using this get a good opportunity to hide executable filenames and extensions.
As a result, your new word will be Softeraw.
To understand this better, review the diagram below.
Can a Trojan Be Put in a PDF?
In some malicious PDF attacks, it is possible to put exploits or malicious scripts inside the PDF.
Many different tools and programs can do this.
However, the RLO method is different.
So only the image of the EXE changes.
The target user, on the other hand, opens this file believing it to be an innocent PDF.
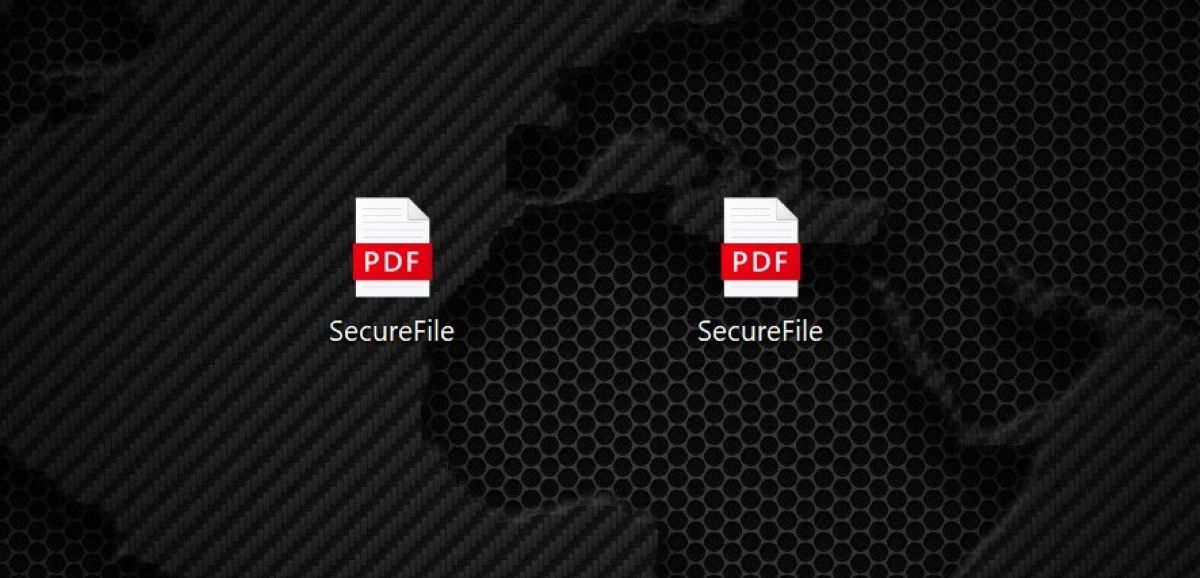
Which of these files is PDF?
You cannot determine this at a glance.
Instead, Y=you should probably look at the contents of the file.
But in case you were wondering, the file on the left is the actual PDF.
This trick is pretty easy to do.
Attackers first write malicious code and compile it.
The compiled code gives an output in exe format.
Attackers change the name and icon of this EXE and turn its appearance into a PDF.
So how does the naming process work?
This is where RLO comes into play.
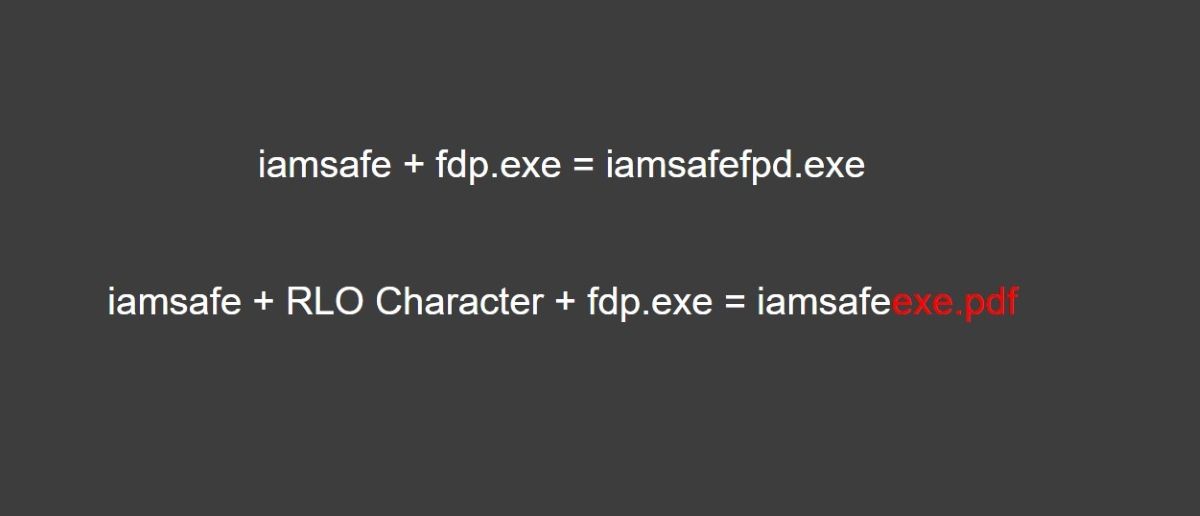
For example, suppose you have an EXE namediamsafefdp.exe.
At this stage, the attacker will put an RLO character betweeniamsafeandfdp.exetorename the file.
It is quite easy to do this in Windows.
Just right-click while renaming.
The file is still an EXE.
It just looks like a PDF in appearance.
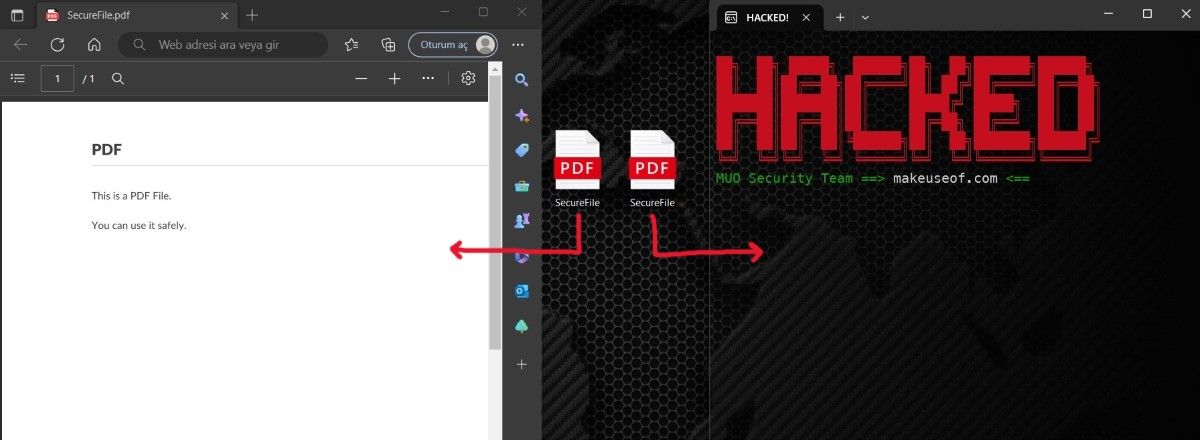
The image below is the answer to our earlier question.
The EXE you see on the right was created using the RLO method.
In appearance, both files are the same, but their content is completely different.
How Can You Protect From This punch in Of Attack?
The first is to use the rename option to check the file you want to open.
So the unselected part will be the actual extension of the file.
If you see the EXE format in the unselected part, you should not open this file.
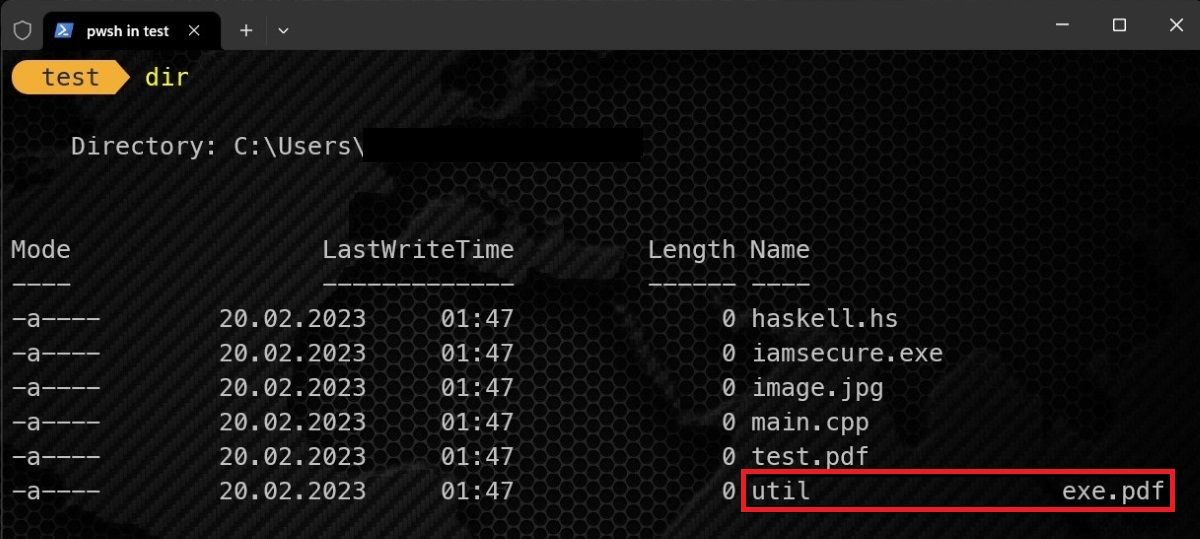
For this, simplyuse thedircommandas follows.
This indicates that there is something you should be suspicious of.
That’s why you shouldn’t download every file you see on the internet.
No matter how safe you think they are, always think twice.
Before downloading a file, there are several precautions you could take.
First of all, you should see to it that the site you are downloading from is reliable.
you’re free to check the file you will download later online.
If you are sure of everything, it is entirely up to you to make this decision.