How did you get into online security?
My background is in software development, later specializing in system architecture.
What are the most common security vulnerabilities you uncovered?
But companies spend a lot of money on data protection.
How is it so easily compromised?
It’s an interesting thing.

Then there is the question of when security is applied.
Many organizations still have their software built (makes air quotes!
), finished, and tested by a vendor, and only apply security once its delivered.

I mean that’s just a terrible way to do security.
I want to help companies avoid that vulnerability in the first place.
How do companies know when they’ve been breached and what data has been stolen?

(Laughs) Well, very often, companies know they’ve been breached when I tell them!
Think of Sony Pictures.
What throw in of data are hackers after?
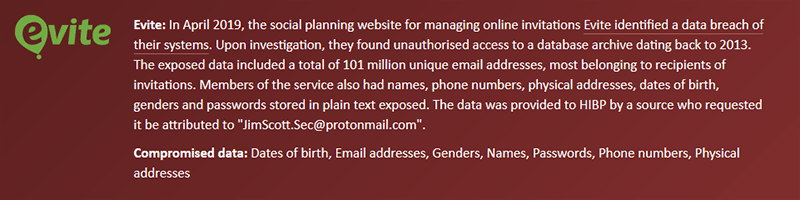
Depending on their motives, anything on the internet is a target.
But there’s plenty of people out there, mostly kids, that only want a trophy.
How does stolen data impact companies and individuals?
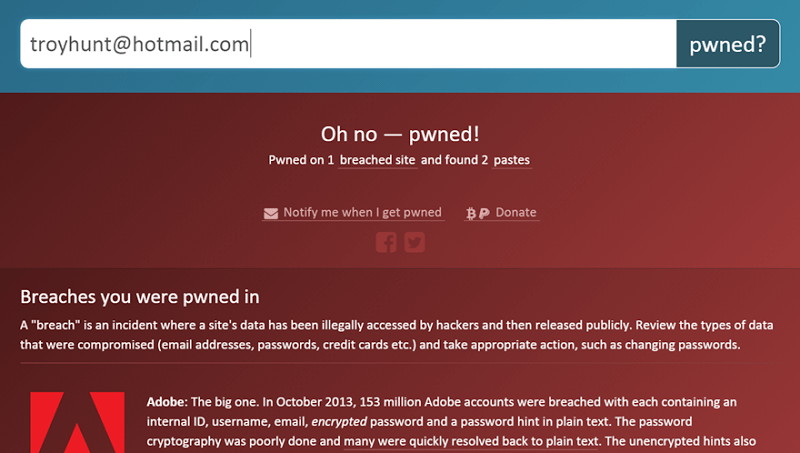
It depends on the throw in of data.
For Sony Pictures, it was unreleased movies which is valuable intellectual property.
Credentials can be used to break into accounts, for sending spam, and for very targeted phishing.
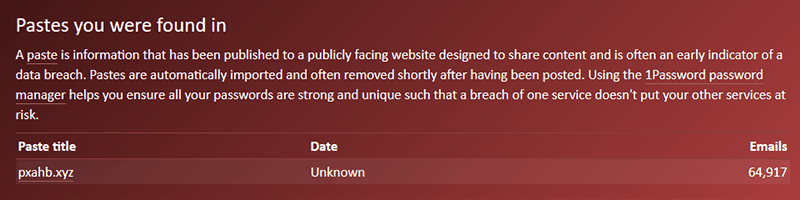
Does a company have to notify individuals of data breaches?
That depends on your jurisdiction.
Under the GDP in Europe, the guidelines are much more stringent.
Why did you start Have I Been Pwned, and what service does it provide?
Another thing I found curious was that a lot of people who had been in data breaches were unaware.
That was the genesis for Have I Been Pwned.
How do you acquire breached databases?
Initially, I went out and grabbed publicly available information.
It does sort of beg the question you know who are these people?
Are they the bad guys?
Are they people who are just trading information?
The reality of it is it’s a bit of everything.
What is a paste?
A paste is text which is literally just pasted onto a website.
What actions do you recommend for an individual whose data has been stolen?
It really depends on the nature of the data.
A password manager is a good tool to make them all unique.
If it’s a password on just that single site, its a lot easier.

Additionally, once sites are aware of a data breach, they usually reset all passwords anyway.
If it’s something more personal like a credit card, go ahead and cancel the card.
What is the Hack Yourself First workshop?

Its designed to help software developers, sysadmins, IT pros, etc.
understand how their security vulnerabilities are exploited so they can better protect themselves.
yo, comment on how to improve this article.


